Attackers usually use duties as a way to cover their tracks. They may additionally use the power to run duties with completely different person rights to realize extra entry. Earlier, I really helpful that you set up auditing to trace duties being set. Now I like to recommend you harden a setting in your workstations to stop activity scheduling within the first place.
Under are the Microsoft Defender Superior Risk Safety (ATP) really helpful actions:
 Susan Bradley
Susan BradleyHome windows Defender ATP suggestions
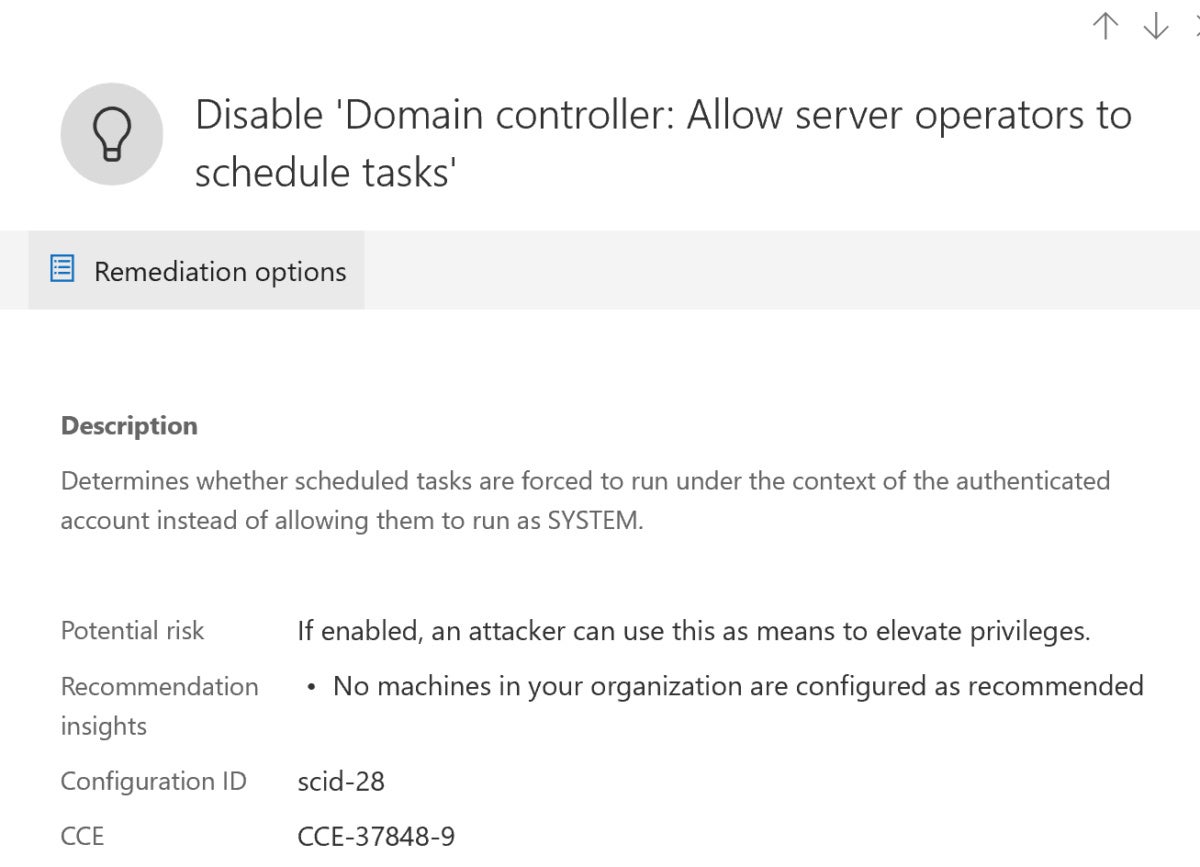
The “Area controller: Permit server operators to schedule duties” setting determines whether or not scheduled duties are pressured to run beneath the context of the authenticated account as a substitute of permitting them to run as SYSTEM. Disabling this setting impacts solely the power to schedule jobs utilizing the AT command and doesn’t have an effect on duties set utilizing Activity Scheduler.
As famous by blogger Randy Franklin Smith, “In contrast to Scheduled Duties which require you to specify the credential beneath which the duty will run, AT jobs run beneath the authority of no matter account the AT service runs, which is SYSTEM by default. Non-administrators who can schedule AT instructions thus have a way to raise their privileges. This coverage controls whether or not members of the native Server Operators group can schedule AT jobs. If disabled, solely directors can.”

