Cybersecurity researchers yesterday unveiled the existence of a extremely subtle adware framework that has been in operation for at the least final 5 years—however remained undetected till just lately.
Dubbed TajMahal by researchers at Kaspersky Lab, the APT framework is a high-tech modular-based malware toolkit that not solely helps an unlimited variety of malicious plugins for distinct espionage operations, but in addition contains never-before-seen and obscure methods.
By the best way, Kaspersky did not point out why they named the framework after Taj Mahal, one of many Seven Wonders of the World situated in India.
TajMahal toolkit was first discovered by safety researchers late final yr when hackers used it to spy on the computer systems of a diplomatic group belonging to a Central Asian nation whose nationality and site haven’t been disclosed.
Nonetheless, malware samples examined by the researchers recommend the cyberespionage group behind the assault has been energetic since at the least August 2014.
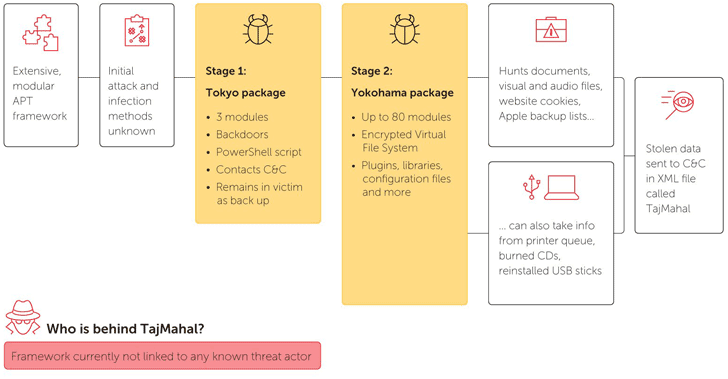
The TajMahal framework consists of two foremost packages—”Tokyo” and “Yokohama”—that collectively comprise over 80 distinct malicious modules, which based on researchers, is without doubt one of the highest numbers of plugins ever seen for an APT toolset.
“It contains backdoors, loaders, orchestrators, C2 communicators, audio recorders, keyloggers, display and webcam grabbers, paperwork and cryptography key stealers, and even its personal file indexer for the sufferer’s machine,” the researchers say.
Researchers haven’t but discovered how TajMahal contaminated its targets on the first place, however they do reveal that when accessed, first stage an infection Tokyo is downloaded on focused machines, which then ship the fully-functional second-stage malware Yokohama.
Yokohama shops malicious modules in its encrypted Digital File System which permits the malware to:
- log keystrokes,
- steal browser cookies and knowledge, together with backup for Apple cellular gadgets,
- file and take screenshots of VoIP calls,
- steal written CD photographs,
- steal paperwork despatched to the printer queue.
Apart from regular spying capabilities, the malware additionally contains some extra distinctive options like requesting to steal a selected file from a beforehand plugged in USB stick. So, subsequent time when the USB is linked to the contaminated pc, the file shall be stolen.
Although the researchers discovered just one TajMahal sufferer to date however given the framework’s sophistication, they consider there are different victims which have but to be found.
“To date we’ve detected a single sufferer based mostly on our telemetry,” Kaspersky stated.
“This principle is bolstered by the truth that we could not see how one of many information within the VFS was utilized by the malware, opening the door to the potential of further variations of the malware which have but to be detected.”
Extra technical particulars might be discovered on the SecureList blog, the place the researchers have additionally revealed a full set of Indicators of compromise (IOCs) and an entire record of 80 malicious modules saved within the malware with a brief description describing what they do.