Following the newest essential replace for Firefox, the Tor Undertaking at the moment launched an up to date model of its anonymity and privateness browser to patch the identical Firefox vulnerability in its bundle.
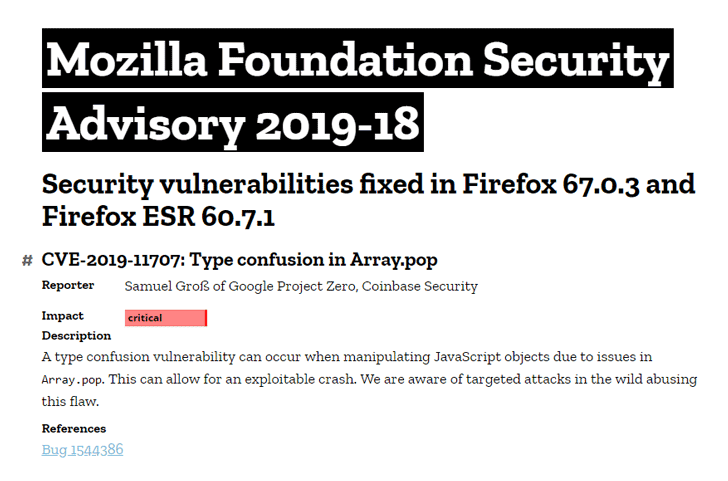
Earlier this week, Mozilla launched Firefox 67.0.three and Firefox ESR 60.7.1 variations to patch a essential actively-exploited vulnerability (CVE-2019-11707) that might permit attackers to remotely take full management over methods operating the weak browser variations.
Apart from updating Firefox, the newest Tor Browser 8.5.2 for desktops additionally contains up to date NoScript model 10.6.three that fixes just a few recognized points.
Based on the Tor Undertaking Staff, if you’re already utilizing Tor browser with “safer” and “most secure” safety ranges, the flaw would not have an effect on you.
For some purpose, the staff hasn’t but launched an up to date Tor model for Android customers, which needs to be obtainable anytime quickly within the subsequent few days. Nevertheless, Android customers have been suggested to modify on “safer” or “most secure” safety ranges with a purpose to mitigate the difficulty till a patched app turns into obtainable.
“The safety degree on Android could be modified by going within the menu on the proper of the URL bar and choosing Safety Settings,” Nicolas Vigier, the Lead Automation Engineer at Tor Undertaking said.
The Google safety researcher who found this flaw additionally revealed that it may very well be abused to launch common cross-site scripting (UXSS) assaults as properly, permitting malicious web sites to bypass same-origin coverage on the sufferer’s net browser and steal delicate info.
Since Tor is primarily being utilized by privacy-conscious customers who cannot afford to get compromised at any price, it is extremely really useful for them to put in the newest model of the anonymity software program instantly.