Safety researchers at Microsoft have launched particulars of a brand new widespread marketing campaign distributing an notorious piece of fileless malware that was primarily being discovered focusing on European and Brazilian customers earlier this 12 months.
Dubbed Astaroth, the malware trojan has been making the rounds since a minimum of 2017 and designed to steal customers’ delicate data like their credentials, keystrokes, and different information, with out dropping any executable file on the disk or putting in any software program on the sufferer’s machine.
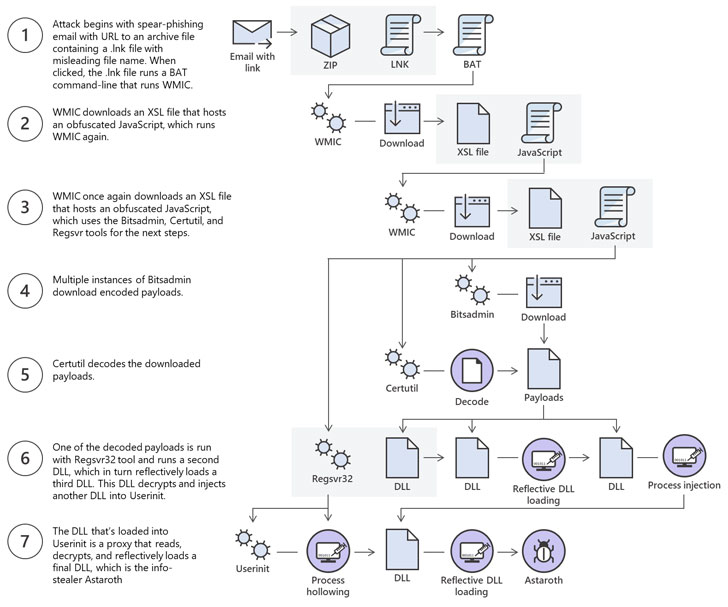
Initially discovered by researchers at Cybereason in February this 12 months, Astaroath lived off the land by working the payload instantly into the reminiscence of a focused pc or by leveraging authentic system instruments, resembling WMIC, Certutil, Bitsadmin, and Regsvr32, to run the malicious code.
Whereas reviewing the Home windows telemetry information, Andrea Lelli, a researcher at Microsoft Defender ATP Analysis Workforce, just lately noticed a sudden uncommon spike within the utilization of Administration Instrumentation Command-line (WMIC) instrument, resulting in the disclosure of a fileless attack.
Additional investigation revealed that the attackers behind this marketing campaign are distributing multi-stage Astaroth malware by means of spear-phishing emails with a malicious hyperlink to a web site internet hosting an LNK shortcut file.
Clicking the shortcut file executes Home windows built-in WMIC instrument that downloads and executes a JavaScript code, which additional abuses the Bitsadmin instrument to obtain all different malicious payloads that truly carry out the malicious duties of pilfering and importing the sufferer’s information whereas disguising itself as a system course of.
“All of the payloads are Base64-encoded and decoded utilizing the Certutil instrument. Two of them end in plain DLL recordsdata (the others stay encrypted),” the researcher stated in a blog post printed Monday.
“The Regsvr32 instrument is then used to load one of many decoded DLLs, which in flip decrypt and hundreds different recordsdata till the ultimate payload, Astaroth, is injected into the Userinit course of.”
Which means that the malware does not depend on any vulnerability exploit or conventional trojan downloader to obtain something on the focused system. As a substitute, it fully depends on system instruments and instructions throughout its total assault chain to masquerade as a daily exercise.
This method known as “dwelling off the land” and lets the malware evade detection from most end-point antivirus safety options that are primarily based on static recordsdata evaluation.
The preliminary entry and execution levels to silently set up the Astaroth malware on course units have been demonstrated within the above-shown assault chain.
As soon as on the focused system, Astaroth tries to steal delicate data like credentials, keystrokes, and different information, and ship it to a distant server managed by the attackers.
The attacker can then use this stolen information to attempt “shifting laterally throughout networks, perform monetary theft, or promote sufferer data within the cybercriminal underground,” the researcher stated.
Microsoft stated the varied characteristic of its Defender ATP next-generation safety might detect such fileless malware attacks at every an infection stage, whereas different file-centric safety options fail to guard their clients.
Andrea stated: “being fileless doesn’t suggest being invisible; it actually doesn’t suggest being undetectable. There isn’t any such factor as the right cybercrime: even fileless malware leaves an extended path of proof.”
To know extra concerning the Astaroth malware, you’ll be able to head on to the Cybereason blog post printed in February this 12 months, in-depth detailing concerning the working of the malware and its talents.