A decade-old botnet malware that currently controls over 450,000 computers worldwide has recently shifted its operations from infecting machines with ransomware or crypto miners to abusing them for sending out sextortion emails to millions of innocent people.
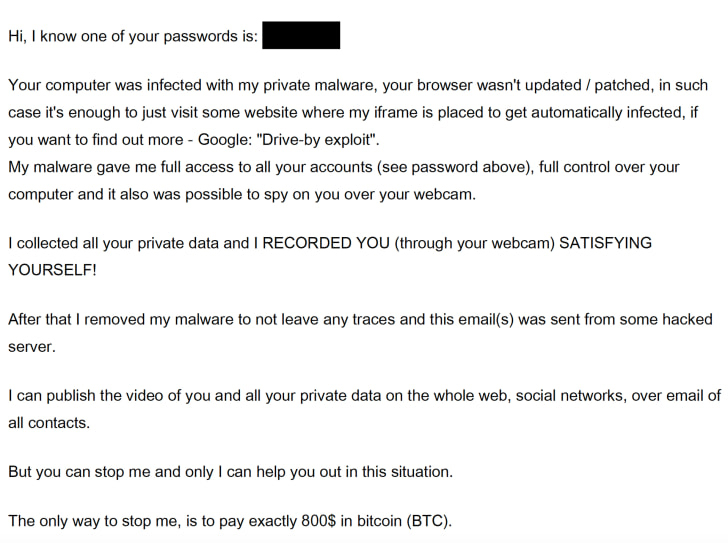
Extortion by email is growing significantly, with a large number of users recently complaining about receiving sextortion emails that attempt to extort money from individuals by blackmailing them into exposing their sexual content.
Though until now, it wasn’t clear how scammers were sending such massive amounts of emails without getting blacklisted by the email providers, security researchers from CheckPoint finally found the missing block in this puzzle.
In its latest report shared with The Hacker News prior to the release, Tel Aviv-based security firm CheckPoint reveals that a botnet, called Phorpiex, has recently been updated to include a spam bot designed to use compromised computers as proxies to send out over 30,000 sextortion emails per hour—without the knowledge of the infected computers’ owners.
How Does Phorpiex Spam Bot Work?
The spambot module of Phorpiex downloads the list of its targets/receipts’ email addresses from a remote command-and-control server and uses a simple implementation of the SMTP protocol to send sextortion emails.
“Then, an email address is randomly selected from the downloaded database, and a message is composed from several hardcoded strings. The spam bot can produce a large amount of spam emails – up to 30,000 per hour. Each individual spam campaign can cover up to 27 million potential victims,” researchers explain.
“The spam bot creates a total of 15,000 threads to send spam messages from one database. Each thread takes a random line from the downloaded file. The next database file is downloaded when all spam threads finish. If we consider the delays, we can estimate that bot is able to send about 30,000 emails in an hour.”
To intimidate innocent recipients, criminals behind these sextortion campaigns also add one of the victims’ online passwords in the subject line or content of the sextortion email, making it more convincing that hacker knows their passwords and might have access to their private content.
In reality, these combinations of email addresses and passwords of recipients were curated from various previously compromised databases. So, the passwords displayed to the victims don’t necessarily belong to their email accounts; it could be old and related to any online service.
“The downloaded database is a text file, which contains up to 20,000 email addresses. In various campaigns, we observed from 325 to 1363 email databases on a C&C server. Therefore, one spam campaign covers up to 27 million potential victims. Each line of this file contains email and password delimited by colons,” researchers say.
The same sextortion campaign powered by similar or the same botnet has also been named as “Save Yourself” malware attacks by other teams of researchers.
In over five months, cybercriminals behind this campaign have made more than 11 BTC, equivalent to approximately $88,000. Though the figure is not huge, researchers say the actual revenue made by the hackers could be larger, as they did not monitor the sextortion campaigns in the years before.