Chinese security firm Qihoo 360 Netlab said it partnered with tech giant Baidu to disrupt a malware botnet infecting over hundreds of thousands of systems.
The botnet was traced back to a group it calls ShuangQiang (also called Double Gun), which has been behind several attacks since 2017 aimed at compromising Windows computers with MBR and VBR bootkits, and installing malicious drivers for financial gain and hijack web traffic to e-commerce sites.
In addition to using images uploaded to Baidu Tieba to distribute configuration files and malware — a technique called steganography — the group has begun using Alibaba Cloud storage to host configuration files and Baidu’s analytics platform Tongji to manage the activity of its infected hosts, the researchers said.
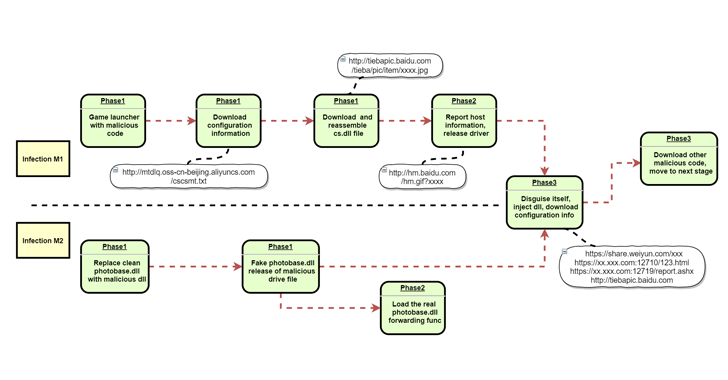
The initial compromise relies on luring unsuspecting users to install game launching software from sketchy game portals that contain malicious code under the guise of a patch.
Once the user downloads and installs the patch, it accesses the aforementioned configuration information to download a separate program named “cs.dll” from Baidu Tieba that’s stored as an image file.
In the subsequent stages, “cs.dll” not only creates a bot ID and reports it back to the attacker-controlled server, but it also injects a second driver that hijacks system processes (e.g., lassas.exe and svchost.exe) in order to download next-stage payloads to advance the group’s motives.
Qihoo researchers also detailed a second infection chain wherein game client software is altered with malicious libraries (a modified version of photobase.dll), using a method called DLL hijacking to release and load the malicious driver before loading the legitimate module.
The company said it reached out to Baidu’s security team on May 14 and that they jointly took action to prevent the further spread of the botnet by blocking all downloads from the URLs involved.
“During this joint operation, through the analysis, sharing, and response of threat information, we have formed a better understanding of the technical means, logic, and rules of the Double Gun gang,” Baidu said.