The ATT&CK framework, developed by MITRE Corp., has been around for five years and is a living, growing document of threat tactics and techniques that have been observed from millions of attacks on enterprise networks. The funky acronym stands for Adversarial Tactics, Techniques, and Common Knowledge. It began as an internal project and morphed into this behemoth of a public knowledge base that numerous security vendors and consultants have picked up. (More on that in a moment.)
The goal of the MITRE researchers is to break down and classify attacks in a consistent and clear manner that can make it easier to compare and contrast them to find how the attacker exploited your networks and endpoints and penetrated your network. To get a general idea of what ATT&CK is all about, watch the short video below that was recorded at a recent BSides conference where one of the developers, Andy Applebaum, describes its origins and how it can be used in everyday operations.
Building an effective red team
Building a great red team in your IT operations staff can be useful on several levels. This team can help you figure out if your current collection of defensive tools is comprehensive enough to identify and stop potential attacks. A red team can be one way to find and fix the gaps in your firewalls and endpoint detection products. A great red team can be an early warning system to find common origins of attacks and to track an adversary’s techniques.
The first half of building such a team is hiring the right people. We have written before in general terms and another article here about hiring experienced staffers. The second part is a lot harder: getting the right collection of tools to use to understand your potential weak areas. You have several choices:
- Built your own red-team-style attack tools
- Hire a managed security service provider (MSSP) or consultant to monitor your network and defenses
- Assemble a collection of various paid and open source techniques for internal use
Each choice has advantages and disadvantages. Building your own tools is a great way to get what you need, but can be time consuming and expensive. Hiring a consultant is less time-intensive, but could still end up costing you a lot of dough in the long run. Numerous security consultants offer red team penetration-type testing and security monitoring tools and services, from IBM X-Force Red to smaller MSSPs like Network Technology Partners with their ARGISS managed monitoring service. Many consulting firms have their own frameworks or have developed their own tools as part of their practice areas too.
If neither of those paths is attractive, you probably will end up using the third method: a variety of open source tools. Here you will find almost too many choices. Some tools specialize in particular attack scenarios, such as PowerShell exploits or the BloodHound tool that is used for testing Active Directory-based exploits. These are great for what they offer, but aren’t very comprehensive. That is where using the ATT&CK classification framework comes into play.
Why bother with ATT&CK?
As adversaries get more skilled, defenders have to up their game too. By classifying attacks into discreet units, it’s easier for researchers to see common patterns, figure out who authored different campaigns, and track how a piece of malware has evolved over the years as the author added new features and attack methods.
While other tools can identify malware hashes and behaviors, ATT&CK is one of the more comprehensive methods that can look at the actual malware components and lay them out in detail. Most modern malware uses a combination of techniques to hide its operation, stage its exploits, evade detection, and leverage network weaknesses. Finding these various building blocks is a key part of defending against their perfidy.
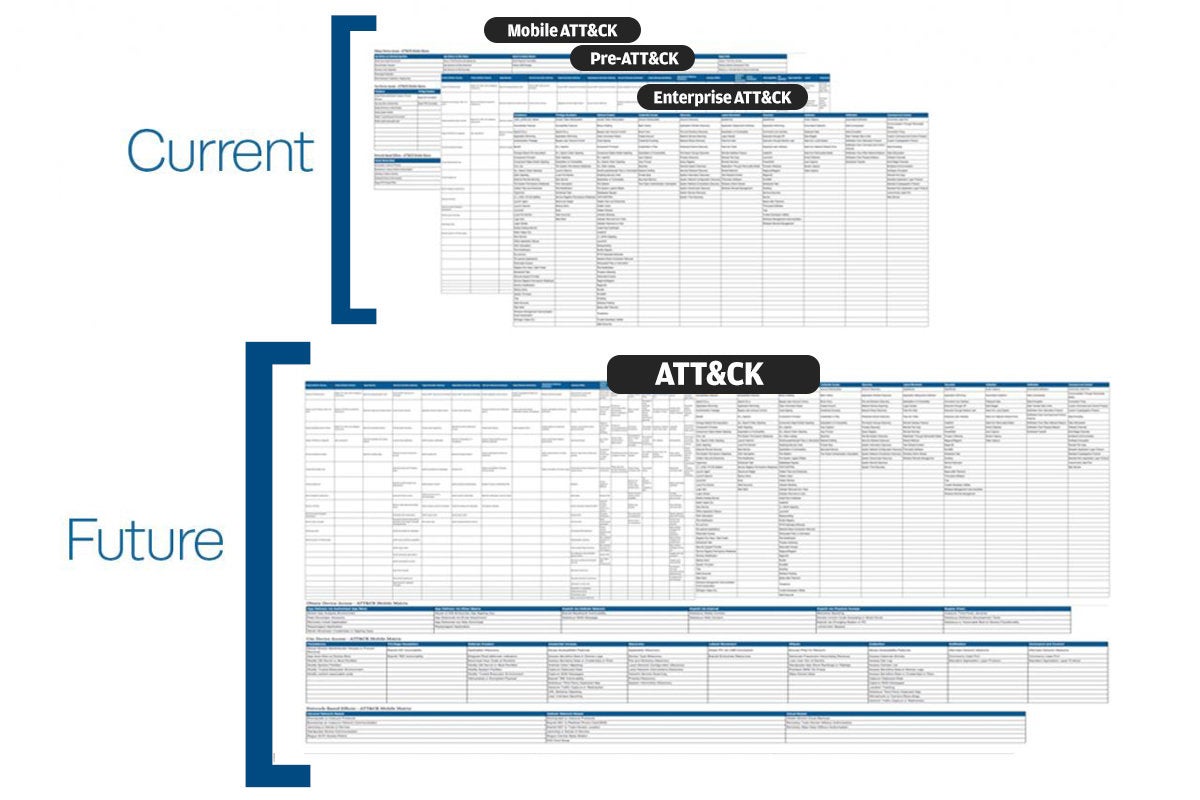
ATT&CK’s five threat matrices
The first matrix is a “pre-attack” collection of 17 different categories that help to prevent an attack before the adversary has a chance to get inside your network — when an attacker is reconnoitering your domain, for example. Three matrices, each with a collection for Windows, Mac or Linux endpoints that cover a total of 169 different techniques. Finally, a fifth collection offers additional categories for mobile-based attacks.
Each cell of these matrices contains a single tactic, such as forced authentication using Server Message Block (SMB) protocols and how a malware author can use this to gain entry to your network. The framework also contains information on recent malware that uses this technique (in this case, Dragonfly), the way you can detect it (monitor SMB traffic on the appropriate ports), and how you can mitigate its abuse (using egress filters to block SMB traffic).
My short description really doesn’t do the MITRE effort justice: If you dive deep enough into ATT&CK, you will find it incredibly rich and detailed, and perhaps overwhelming. It can also be used to fill in gaps of your own knowledge about exploits and malware techniques.
ATT&CK undergoing constant improvement
The ATT&CK blog post describes some of these innovations, including:
- Combining the various threat matrices into a coherent single document (see graphic below)
- Hosting ATT&CK on a new wiki platform and making it easier to navigate
- Developing a new API that can make it easier to interact with ATT&CK using the STIX/TAXII threat sharing schemas
- Adding better search capabilities
- Creating a governance committee to decide on future improvements, particularly as more private security vendors begin to offer ATT&CK-based enhancements and tools.
 MITRE
MITREMITRE also uses the ATT&CK threat model to test various endpoint detection and prevention products. The first round of which was an adversary emulation of APT3/Gothic Panda.
ATT&CK integrated into VERIS
A recent development is a project to create a mapping and translation layer between Verizon’s Vocabulary for Event Recording and Incident Sharing (VERIS) and ATT&CK. VERIS is a set of metrics that provides a common language to describe security incidents in a structured way. It is used in Verizon’s Data Breach Investigations Reports to classify incidents.
The goal of the integration is to allow incident analysis that combines the adversary behavior information that ATT&CK describes with the demographics and metadata from VERIS. “The resulting mapping between VERIS and ATT&CK will allow cyber defenders to create a fuller and more detailed picture of cyber incidents, including the threat actor, technical behavior, assets targeted, and impact,” wrote Jon Baker, director of research and development at MITRE Engenuity, and Richard Struse, director of the MITRE Engenuity Center for Threat-Informed Defense, in a blog post.
The VERIS/ATT&CK mapping is available on GitHub.
Third-party ATT&CK projects
The real genius in ATT&CK is how others have embraced and extended its features. Here are just a few references to ongoing third-party projects:
All the above tools are free and open source projects. Another tool that isn’t free called AttackIQ FireDrill can script out more complex interactions to evaluate your network risk and vulnerabilities.
Each tool has a somewhat different approach to interacting with ATT&CK, and we plan on doing a comparative review in the near future that will showcase their differences, how they are set up, and under what circumstances are they most useful. For example, the Palo Alto playbook is only relevant to exploring the OilRig malware, but it references more than 100 different indicators that cover 19 different ATT&CK techniques, showing exactly how complex a piece of malware it is. If you are interested in building out your red team capabilities, check out what MITRE has put together.
Copyright © 2021 IDG Communications, Inc.

