As a CISO, one of the most challenging questions to answer is “How well are we protected right now?” Between the acceleration of hackers’ offensive capabilities and the dynamic nature of information networks, a drift in the security posture is unavoidable and needs to be continuously compensated. Therefore, answering that question implies continuously validating the security posture and being in a position to check it including, against the latest emerging threats.
Yet, the bulk of cybersecurity is focused on defensive tools. The combination of the rapid evolution of technology and the multiplication of technology layers, combined with the professionalization of the threat landscape, has led to a profusion of cybersecurity tools tackling different security aspects.
Checking the cybersecurity solution stack efficiency is typically done through pen-testing or, more recently, through red teaming – an exercise aimed to map possible loopholes that would lead to a data breach. When performed once or twice a year only, these tests might satisfy the compliance regulators. Still, as new threats emerge daily, they fail to inform about the environment’s current security posture effectively.
In addition, these infrequent tests fail to inform about potential tool overlaps and are not designed to prevent tool sprawl, a frequent occurrence in a field where over half of SOC centers are overrun with redundant security tools and are swamped by too many alerts.
Unrationalized security stacks are not only unnecessarily costly, but they also generate more false-positive calls, needlessly taxing security staff stamina and increasing the risk of missing a critical alert.
The ability to measure each tool’s efficacy, eliminate overlap and maintain continuous control over security baseline variability relies on continuous access to quantified data. This is at the core of what Extended Security Posture Management (XPSM) brings to the table.
Understanding Extended Security Posture Management
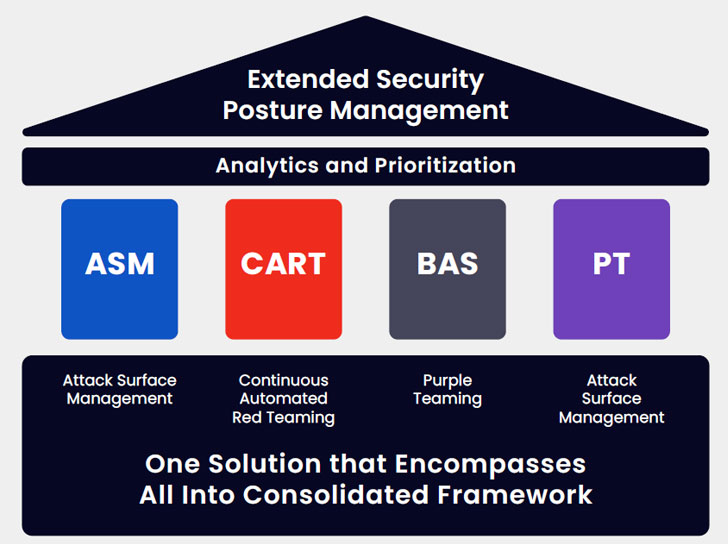
Extended Security Posture Management (XSPM) is a multilayered process combining the capabilities of Attack Surface Management (ASM), Breach and Attack Simulation (BAS), Continuous Automated Red Teaming (CART), and Purple Teaming to continuously evaluate and score the infrastructure’s overall cyber resiliency.
This up-to-date comprehensive snapshot of the active security posture, combined with detailed remediation process recommendations, is conducive to making rational business decisions based on hard data.
Using the granular evaluation of each individual tool and of the security control configuration, an XSPM solution provides granular information about each solution used, the eventual overlap between two or more solutions and the remaining security gaps. It then provides detailed recommendations about the remediation process for each gap and optimization options for identified overlaps.
The Advantage of a Consolidated, Extensive Baseline
Security teams are systematically impressed by the difference in having actionable data made, both in improving the security posture and in rationalizing cybersecurity spending.
XSPM helps the security team to deal with the constant content configuration churn and leverages telemetry to help identify the gaps in security by generating up-to-date emerging threats feeds and providing additional test cases emulating TTPs that attackers would use, saving DevSocOps the time needed to develop those test cases. When running XSPM validation modules, knowing that the tests are timely, current, and relevant enables reflecting on the efficacy of security controls and understanding where to make investments to ensure that the configuration, hygiene and posture are maintained through the constant changes in the environment.
By providing visibility and maximizing relevancy, XSPM helps verify that each dollar spent benefits risk reduction and tool efficacy through baselining and trending and automatically generating reports containing detailed recommendations covering security hardening and tool stack optimization; it dramatically facilitates conversations with the board.
The switch from infrequent to regular testing, made possible by automation, enables both the continuous baseline variability monitoring and the quantified calculation of ROI achieved through tool stack rationalization.
Furthermore, it enables creating attack-based vulnerability management by leveraging the results to prioritize patching.
As a bonus, checking an environment’s ability to withstand the latest attacks can be done almost at a click, and, if needed, recommended mitigation processes can be pushed forward in the prioritized patching schedule.
George Washington’s adage “The best defense is a good offense” definitely applies to cybersecurity, and the continuous offense is the only way to stay ahead of the attackers’ progress consistently.
Note: This article was written by Arien Seghetti, Solution Architect at Cymulate. For more information, visit www.cymulate.com and register for a Free Trial.