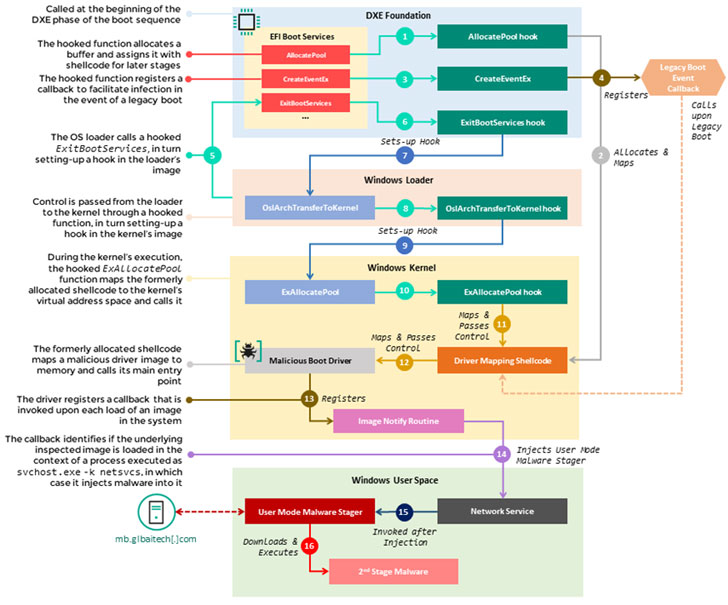
A previously undocumented firmware implant deployed to maintain stealthy persistence as part of a targeted espionage campaign has been linked to the Chinese-speaking Winnti advanced persistent threat group (APT41).
Kaspersky, which codenamed the rootkit MoonBounce, characterized the malware as the “most advanced UEFI firmware implant discovered in the wild to date,” adding “the purpose of the implant is to facilitate the deployment of user-mode malware that stages execution of further payloads downloaded from the internet.”
Firmware-based rootkits, once a rarity in the threat landscape, are fast becoming lucrative tools among sophisticated actors to help achieve long standing foothold in a manner that’s not only hard to detect, but also difficult to remove.
The first firmware-level rootkit — dubbed LoJax — was discovered in the wild in 2018. Since then, three different instances of UEFI malware have been unearthed so far, including MosaicRegressor, FinFisher, and ESPecter.
MoonBounce is concerning for a number of reasons. Unlike FinFisher and ESPecter, which take aim at the EFI System Partition (ESP), the newly discovered rootkit — along the likes of LoJax and MosaicRegressor — targets the SPI flash, a non-volatile storage external to the hard drive.
Such highly persistent bootkit malware is emplaced within SPI flash storage that’s soldered to a computer’s motherboard, effectively making it impossible to get rid of via hard drive replacement and even resistant to re-installation of the operating system.
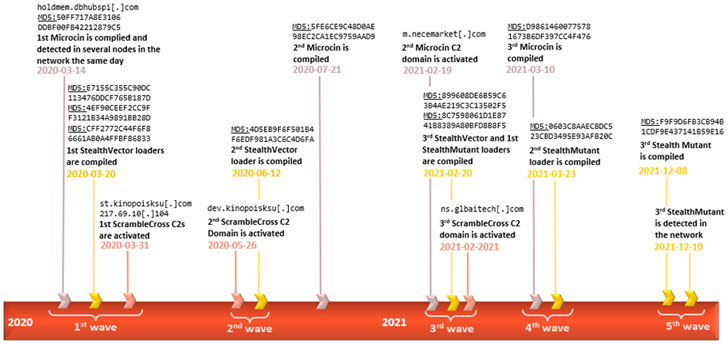
The Russian cybersecurity company said it identified the presence of the firmware rootkit in a single incident last year, indicative of the highly targeted nature of the attack. That said, the exact mechanism by which the UEFI firmware was infected remains unclear.
Adding to its stealthiness is the fact that an existing firmware component was tampered to alter its behaviour — rather than adding a new driver to the image — with the goal of diverting the execution flow of the boot sequence to a malicious “infection chain” that injects the user-mode malware during system startup, which then reaches out to a hardcoded remote server to retrieve the next-stage payload.
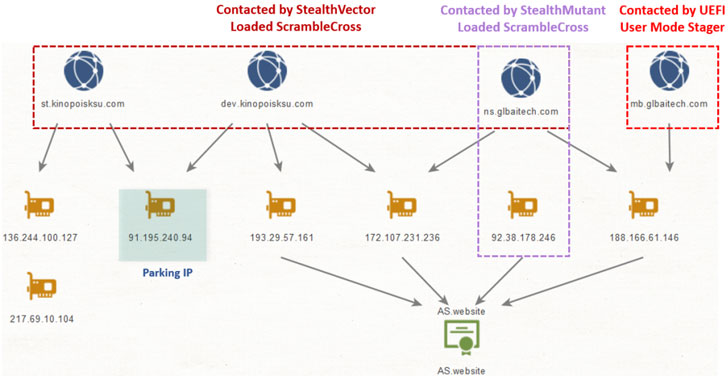
“The infection chain itself does not leave any traces on the hard drive, as its components operate in memory only, thus facilitating a fileless attack with a small footprint,” the researchers noted, adding that it uncovered other non-UEFI implants in the targeted network communicating with the same infrastructure that hosted the staging payload.
Chief among those components deployed across multiple nodes in the network include a backdoor tracked as ScrambleCross (aka Crosswalk) and a number of post-exploitation malware implants, suggesting that the attackers performed lateral movement after gaining an initial access in order to exfiltrate data from specific machines.
To counter such firmware-level modifications, it’s recommended to regularly update the UEFI firmware as well as enable protections such as Boot Guard, Secure boot, and Trust Platform Modules (TPM).
“MoonBounce marks a particular evolution in this group of threats by presenting a more complicated attack flow in comparison to its predecessors and a higher level of technical competence by its authors, who demonstrate a thorough understanding of the finer details involved in the UEFI boot process,” the researchers said.