Potential connections between a subscription-based crimeware-as-a-service (Caas) solution and a cracked copy of Cobalt Strike have been established in what the researchers suspect is being offered as a tool for its customers to stage post-exploitation activities.
Prometheus, as the service is called, first came to light in August 2021 when cybersecurity company Group-IB disclosed details of malicious software distribution campaigns undertaken by cybercriminal groups to distribute Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish in Belgium and the U.S.
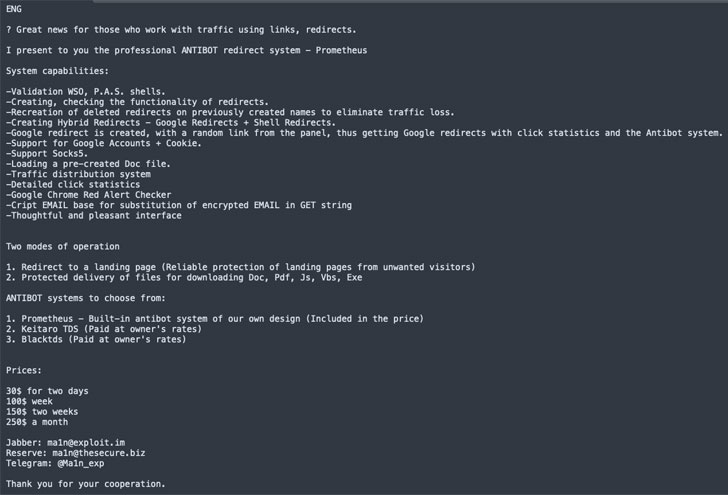
Costing $250 a month, it’s marketed on Russian underground forums as a traffic direction system (TDS) to enable phishing redirection on a mass scale to rogue landing pages that are designed to deploy malware payloads on the targeted systems.
“Prometheus can be considered a full-bodied service/platform that allows threat groups to purvey their malware or phishing operations with ease,” BlackBerry Research and Intelligence Team said in a report shared with The Hacker News. “The main components of Prometheus include a web of malicious infrastructure, malicious email distribution, illicit file-hosting through legitimate services, traffic redirection and the ability to deliver malicious files.”
Typically, the redirection is funneled from one of two main sources, namely with the help of malicious ads (aka malvertising) on legitimate websites, or via websites that have been tampered to insert malicious code.
In the case of Prometheus, the attack chain starts with a spam email containing a HTML file or a Google Docs page that, upon interaction, redirects the victim to a compromised website hosting a PHP backdoor that fingerprints the machine to determine whether the to “to serve the victim with malware or redirect them to another page that might contain a phishing scam.”
Earliest activity connected to the operators of the service, who go by the name “Ma1n” on hacking forums, is said to have commenced in October 2018, with the author linked to other illicit tools offering high quality redirects and PowerMTA kits for mailing to corporate mailboxes, before putting up Prometheus TDS for sale on September 22, 2020.
That’s not all. BlackBerry also found overlaps between Prometheus-related activity and an illegitimate version of the Cobalt Strike adversary simulation and threat emulation software, raising the possibility that the copy is being “proliferated by the Prometheus operators themselves.”
“It’s possible that someone connected with the Prometheus TDS is maintaining this cracked copy and providing it upon purchase,” the researchers said. “It is also possible that this cracked installation may be provided as part of a standard playbook or a virtual machine (VM) installation.”
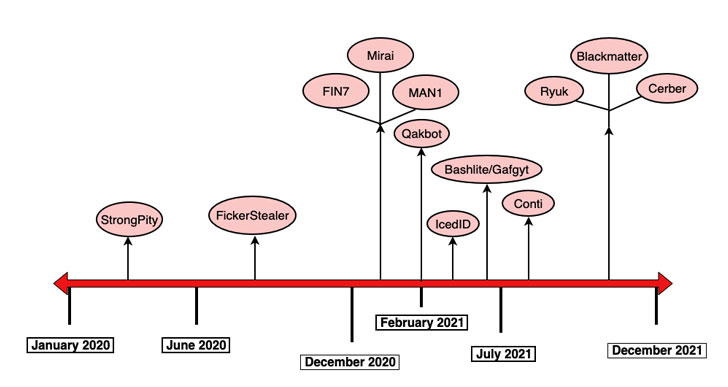
This is substantiated by the fact that a number of threat actors, including DarkCrystal RAT, FickerStealer, FIN7, Qakbot, and IceID, as well as ransomware cartels such as REvil, Ryuk (Wizard Spider), BlackMatter, and Cerber, have used the cracked copy in question over the last two years.
On top of that, the same Cobalt Strike Beacon has also been observed in conjunction with activities associated with an initial access broker tracked as Zebra2104, whose services have been put to use by groups like StrongPity, MountLocker, and Phobos for their own campaigns.
“While TDS’es aren’t a new concept, the level of complexity, support and low financial cost adds credence to the theory that this is a trend that is likely to rise in the threat landscape’s near future,” the researchers noted.
“The volume of groups that are using offerings such as the Prometheus TDS, speak to the success and efficacy of these illicit infrastructure for hire services, which are in essence full-fledged enterprises that support the malicious activities of groups regardless of their size, level of resourcing or motives.”