Intelligence agencies in the U.K. and the U.S. disclosed details of a new botnet malware called Cyclops Blink that’s been attributed to the Russian-backed Sandworm hacking group and deployed in attacks dating back to 2019.
“Cyclops Blink appears to be a replacement framework for the VPNFilter malware exposed in 2018, which exploited network devices, primarily small office/home office (SOHO) routers, and network-attached storage (NAS) devices,” the agencies said. “In common with VPNFilter, Cyclops Blink deployment also appears indiscriminate and widespread.”
The joint government advisory comes from the U.K. National Cyber Security Centre (NCSC), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) in the U.S.
Sandworm, aka Voodoo Bear, is the name assigned to a highly advanced adversary operating out of Russia that’s known to be active since at least 2008. The hacking group has displayed a particular focus on targeting entities in Ukraine and is alleged to be behind the Ukrainian energy sector attacks that caused widespread power outages in late 2015.
The threat actor, in October 2020, was formally linked to Russia’s General Staff Main Intelligence Directorate (GRU) Main Center for Special Technologies (GTsST) military unit 74455.
VPNFilter was first documented by Cisco Talos in May 2018, describing it as a “sophisticated modular malware system” that shares overlaps with the Sandworm’s BlackEnergy malware and features capabilities to support intelligence-collection and destructive cyber attack operations.
The IoT botnet malware was found to have compromised more than 500,000 routers in at least 54 countries, targeting devices from Linksys, MikroTik, NETGEAR, and TP-Link, ASUS, D-Link, Huawei, Ubiquiti, QNAP, UPVEL, and ZTE.
That same month, the U.S. government announced the seizure and takedown of a key internet domain used for the attacks, urging owners of SOHO and NAS appliances that may be infected to reboot their devices to temporarily disrupt the malware.
As of January 2021, an analysis from Trend Micro identified “residual infections” still remaining on thousands of networks years after sinkholing VPNFilter, even as the Sandworm actor simultaneously opted to retool the malware in response to public disclosures.
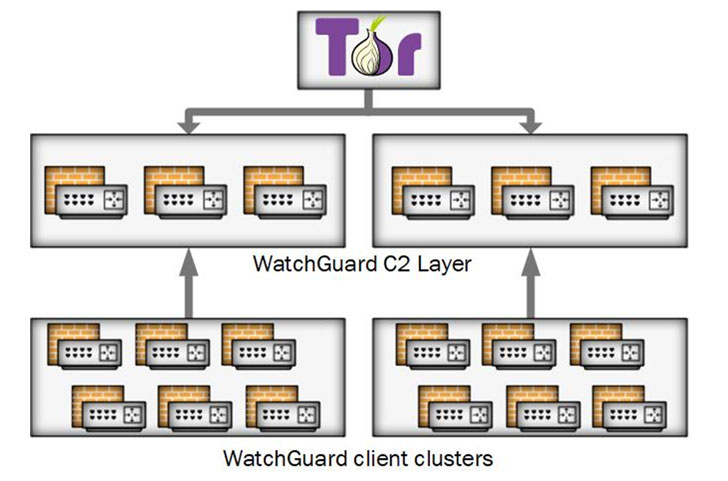
Cyclops Blink, as the substitute is called, is believed to have been in action since at least June 2019 primarily setting its eyes on WatchGuard firewall devices, although the agencies said that the malware could be repurposed to strike other architectures and firmware.
Even more concerningly, the botnet malware is deployed as a fake update and is capable of surviving reboots and firmware upgrades, with command-and-control (C2) communications facilitated over the Tor anonymity network.
“The malware itself is sophisticated and modular with basic core functionality to beacon device information back to a server and enable files to be downloaded and executed,” the researchers noted. “There is also functionality to add new modules while the malware is running, which allows Sandworm to implement additional capability as required.”
WatchGuard, in an independent bulletin, called it a state-sponsored botnet that leveraged a previously identified security vulnerability in the Firebox firmware as the initial access vector. The shortcoming was eventually addressed as of May 2021.
“Based on current estimates, Cyclops Blink may have affected approximately 1% of active WatchGuard firewall appliances,” the company said. “Only those appliances that had been configured to have management open to the Internet are vulnerable to Cyclops Blink.”
The Seattle-headquartered firm is also recommending customers to immediately follow the steps outlined in the 4-Step Cyclops Blink Diagnosis and Remediation Plan to diagnose and eliminate the threat posed by potential malicious activity from the botnet.
The findings come as Russia formally launched a full scale military operation to invade Ukraine, just as its IT infrastructure was crippled by a string of data wiper and distributed denial-of-service (DDoS) attacks.