The individual responsible for leaking Conti chat logs has warned the ransomware gang that more files will be made public soon.
Conti ransomware gang declared its support for Russia soon after the country sent its troops to Ukraine on Feb 28th,2022. The gang is now paying the price for getting involved in the conflict.
Conti Ransomware Gang Receive Backlash
Conti ransomware gang posted a statement on its website claiming that they are ready in “full capacity” to deliver “retaliatory measures” if Western entities attacked critical infrastructure in Russia or any Russian-speaking region. The gang threatened to “strike back” at the entity by attacking their infrastructure in return.
Apparently, the group had second thoughts after posting this resentful statement and later revised their stance and issued another message that read:
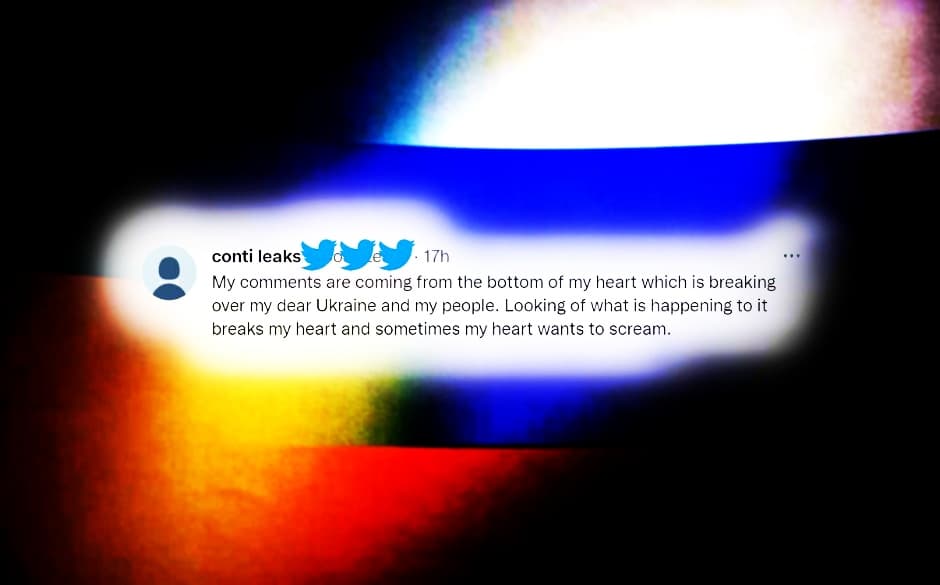
We do not ally with any government and we condemn the ongoing war. However, since the West is known to wage its wars primarily by targeting civilians, we will use our resources in order to strike back if the well-being and safety of peaceful citizens will be at stake due to American cyber aggression.
Conti Ransomware Gang
Full preview of Conti Gang’s post
Cache of Conti Gang’s Chat Logs Leaked
As per VX-Underground, a malware research platform, soon after Conti showed support for Russian troops, a dataset containing around 400 JSON files and 60,000 internal chat logs in the Conti group’s native Russian language was leaked online.
Cisco Talos’ researcher Azim Khodjibaev tweeted that the chats were stolen from the Jabber chat app. Some claim that a Ukrainian security researcher leaked the files, while others believe it is an insider’s job and a Ukrainian member of the gang probably leaked Conti gang members’ chats.
The individual responsible for this leak has warned the Conti gang that more files stolen from them will be made public soon and posted the data with this message: “Glory to Ukraine.”

What Information was Leaked?
The leaked files contain around one year’s worth of internal chats between Jan 2021 and February 2022. Each file has hundreds of messages exchanged between Conti group members. An analysis of some of these files revealed that most chats mentioned their recently acquired TrickBot malware and Emotet and Ryuk malware.
Moreover, researchers identified over 200 Bitcoin addresses holding around $13 million in ransom payments. The chats also revealed personal details of the members, their conversations with victims, critical infrastructure data, and IP addresses, among other information. Security researcher Bill Demirkapi translated the chats and other data into English.
Conti should have taken cues from the LockBit ransomware gang, which also has Russians as its members, as the group has confirmed that it’ll not get involved in the conflict because it doesn’t want to hurt its Ukrainian and other foreign members.
Watch out what you are about to download!
Although the cybersecurity community is well aware of the risks of downloading anonymous files especially those on cybercriminals, researchers at Malwarebytes have a warning for you.
According to a tweet by Malwarebytes Threat Intelligence, since most of the download links are on the self-proclaimed “Anonymous” file sharing service AnonFiles, the site is “pushing bogus extensions and VPNs before one can download the intended file.
More Security News:
- Russia ”neutralizes” REvil ransomware gang, arrests 14
- DDoS Attack and Data Wiper Malware hit Computers in Ukraine
- Ransomware gang with $42 million laundering caught by Ukraine
- Husband and wife among ransomware operators arrested in Ukraine
- Russian TV channels & EV charging station with pro-Ukraine messages