The insidious Emotet botnet, which staged a return in November 2021 after a 10-month-long hiatus, is once again exhibiting signs of steady growth, amassing a swarm of over 100,000 infected hosts for perpetrating its malicious activities.
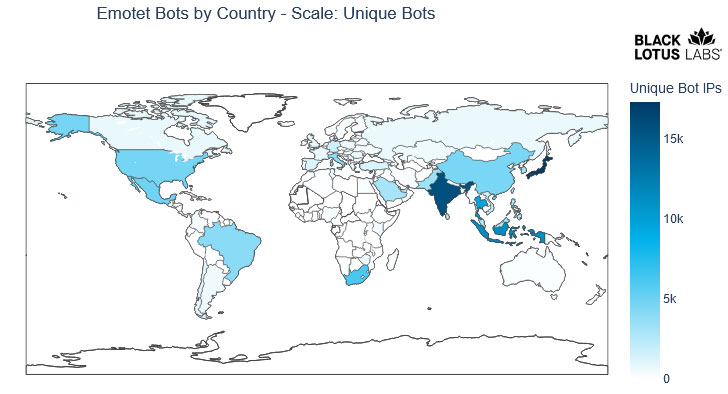
“While Emotet has not yet attained the same scale it once had, the botnet is showing a strong resurgence with a total of approximately 130,000 unique bots spread across 179 countries since November 2021,” researchers from Lumen’s Black Lotus Labs said in a report.
Emotet, prior to its takedown in late January 2021 as part of a coordinated law enforcement operation dubbed “Ladybird,” had infected no fewer than 1.6 million devices globally, acting as a conduit for cybercriminals to install other types of malware, such as banking trojans or ransomware, onto compromised systems.
The malware officially resurfaced in November 2021 using TrickBot as a delivery vehicle, with the latter shuttering its attack infrastructure late last month after several key members of the group were absorbed into the Conti ransomware cartel.
Emotet’s resurrection is said to have been orchestrated by the Conti gang itself in an attempt to shift tactics in response to increased law enforcement scrutiny into the TrickBot’s malware distribution activities.
Black Lotus Labs noted that the “aggregation of bots really didn’t begin in earnest until January [2022],” adding the new variants of Emotet have swapped the RSA encryption scheme in favor of elliptic curve cryptography (ECC) to encrypt network traffic.
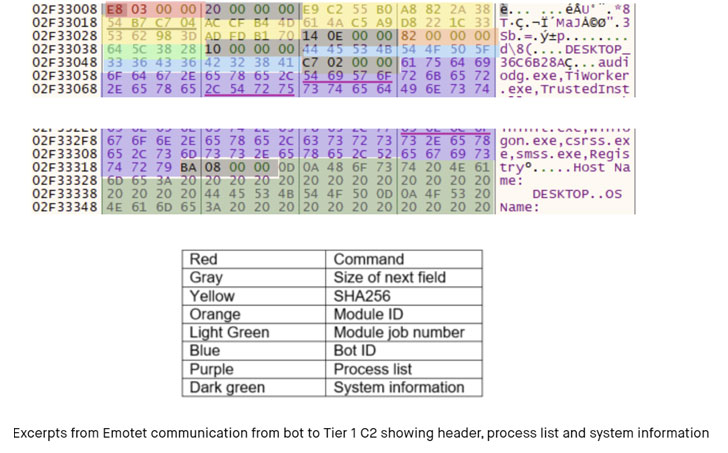
Another new addition to its capabilities is its ability to gather additional system information beyond a list of running processes from the compromised machines.
What’s more, Emotet’s botnet infrastructure is said to encompass nearly 200 command-and-control (C2) servers, with most of the domains located in the U.S., Germany, France, Brazil, Thailand, Singapore, Indonesia, Canada, the U.K., and India.
Infected bots, on the other hand, are heavily concentrated in Asia, chiefly Japan, India, Indonesia, and Thailand, followed by South Africa, Mexico, the U.S., China, Brazil, and Italy. “This is not surprising given the preponderance of vulnerable or outdated Windows hosts in the region,” the researchers said.
“The growth and distribution of bots is an important indicator of Emotet’s progress in restoring its once sprawling infrastructure,” Black Lotus Labs noted. “Each bot is a potential foothold to a coveted network and presents an opportunity to deploy Cobalt Strike or eventually be promoted to a Bot C2.”