A nascent information stealer called Mars has been observed in campaigns that take advantage of cracked versions of the malware to steal information stored in web browsers and cryptocurrency wallets.
“Mars Stealer is being distributed via social engineering techniques, malspam campaigns, malicious software cracks, and keygens,” Morphisec malware researcher Arnold Osipov said in a report published Tuesday.
Based on the Oski Stealer and first discovered in June 2021, Mars Stealer is said to be constantly under development and available for sale on over 47 underground forums, darknet sites, and Telegram channels, costing only $160 for a lifetime subscription.
Information stealers allow adversaries to vacuum personal information from compromised systems, including stored credentials and browser cookies, which are then sold on criminal marketplaces or used as a springboard for launching further attacks.
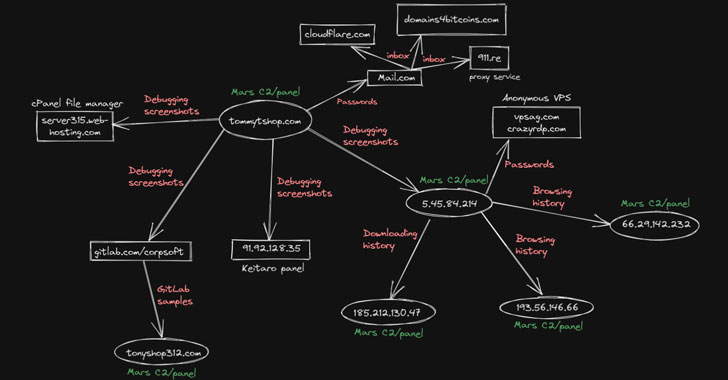
The release of Mars Stealer last year has also been accompanied by a steady increase in attack campaigns, some of which have involved the use of a cracked version of the malware that has been configured in such a manner that it has exposed critical assets on the internet, inadvertently leaking details about the threat actor’s infrastructure.
Also notable is a campaign observed last month that siphoned the passwords belonging to students, faculty members, and content makers who have downloaded trojanized versions of legitimate applications.
On top of that, the cybersecurity company noted that it “identified credentials which led to the full compromise of a leading healthcare infrastructure provider in Canada, and a number of high-profile Canadian service companies.”
While Mars Stealer is most commonly distributed via spam email messaging containing a compressed executable, download link, or document payload, it’s also propagated via fraudulent cloned websites advertising well-known software such as OpenOffice that were then pushed through Google Ads.
The goal is to leverage geographically targeted ads to trick potential victims searching for the original software into visiting a malicious site instead, ultimately leading to the deployment of the malware.
Mars Stealer, for its part, is engineered to harvest and exfiltrate browser autofill data, credit card information, browser extension details, including that of cryptocurrency wallets like Metamask, Coinbase Wallet, and Binance Wallet, and system metadata.
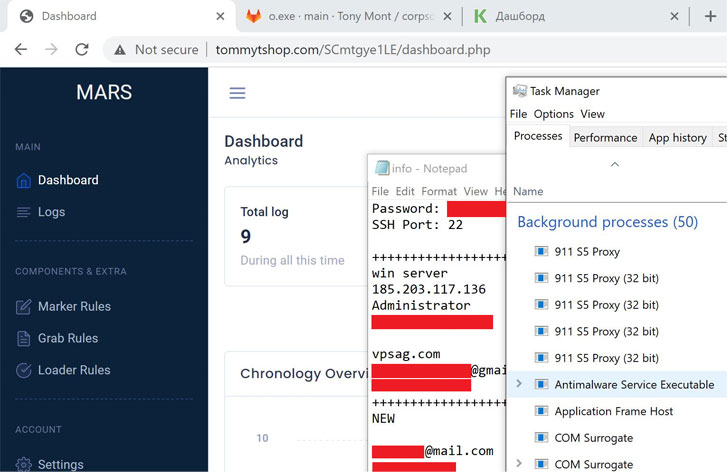
But because the threat actor compromised their own machine with the Mars Stealer during debugging, the OPSEC mistake allowed the researchers to attribute the campaign to a Russian speaker as well as uncover details about the adversary’s use of GitLab and stolen credentials to place Google Ads.
“Infostealers offer an accessible entry point to criminal activity,” Osipov said, adding such tools “empower novice cybercriminals to build a reputation they can leverage to acquire more powerful malware from more sophisticated actors.”