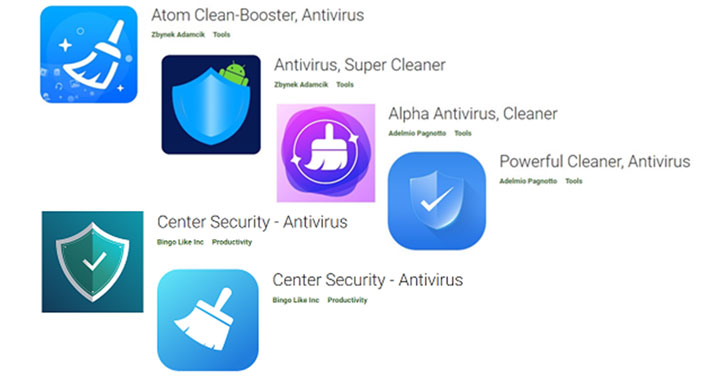
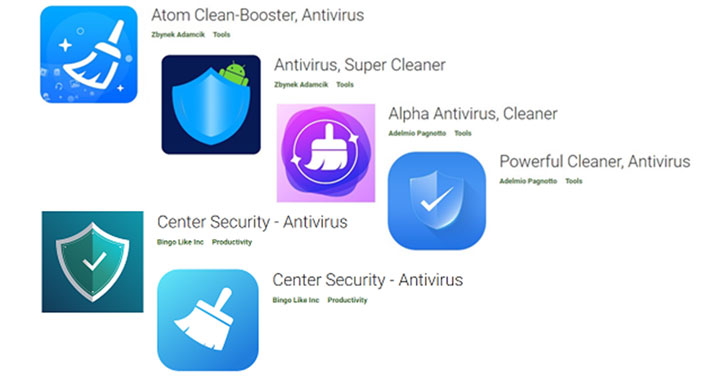
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot.
“SharkBot steals credentials and banking information,” Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News. “This malware implements a geofencing feature and evasion techniques, which makes it stand out from the rest of malwares.”
Particularly, the malware is designed to ignore users from China, India, Romania, Russia, Ukraine, and Belarus. The rogue apps are said to have been installed more than 15,000 times prior to their removal, with most of the victims located in Italy and the U.K.
The report complements previous findings from NCC Group, which found the bankbot posing as antivirus apps to carry out unauthorized transactions via Automatic Transfer Systems (ATS).
SharkBot takes advantage of the Accessibility Services permissions to present fake overlay windows on top of legitimate banking apps. Thus when unsuspecting users enter their usernames and passwords in the windows that mimic benign credential input forms, the captured data is sent to a malicious server.
One new notable feature of SharkBot is its ability to auto reply to notifications from Facebook Messenger and WhatsApp to distribute a phishing link to the antivirus app, thus propagating the malware in a worm-like fashion. A similar feature was incorporated in FluBot earlier this February.
The latest findings come as Google took steps to banish 11 apps from the Play Store on March 25 after they were caught incorporating an invasive SDK to discreetly harvest user data, including precise location information, email and phone numbers, nearby devices, and passwords.
“What’s also noteworthy here is that the threat actors push messages to victims containing malicious links, which leads to widespread adoption,” Alexander Chailytko, cyber security, research and innovation manager at Check Point Software, said.
“All in all, the use of push-messages by the threat actors requesting an answer from users is an unusual spreading technique.”