A previously undocumented remote access trojan (RAT) written in the Go programming language has been spotted disproportionately targeting entities in Italy, Spain, and the U.K.
Called Nerbian RAT by enterprise security firm Proofpoint, the novel malware leverages COVID-19-themed lures to propagate as part of a low volume email-borne phishing campaign that started on April 26, 2022.
“The newly identified Nerbian RAT leverages multiple anti-analysis components spread across several stages, including multiple open-source libraries,” Proofpoint researchers said in a report shared with The Hacker News.
“It is written in operating system (OS) agnostic Go programming language, compiled for 64-bit systems, and leverages several encryption routines to further evade network analysis.”
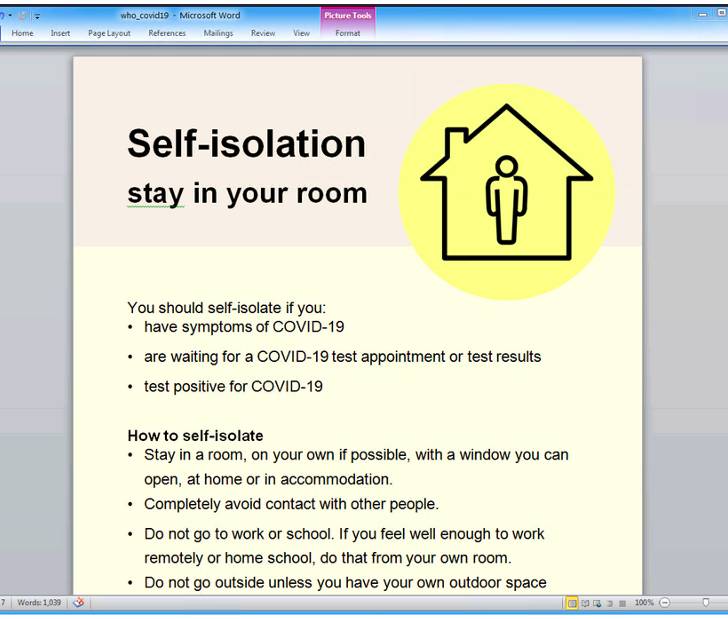
The messages, amounting to less than 100 in number, purport to be from the World Health Organization about safety measures related to COVID-19, urging potential victims to open a macro-laced Microsoft Word document to access the “latest health advice.”
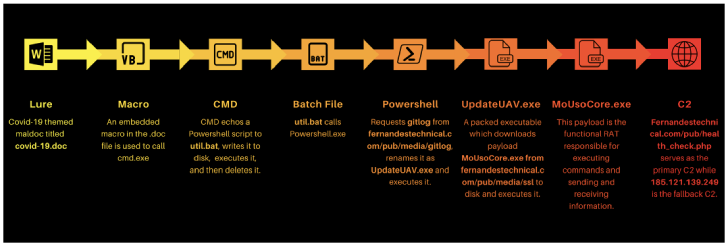
Enabling the macros displays COVID-19 guidance, including steps for self-isolation, while in the background, the embedded macro triggers an infection chain that delivers a payload called “UpdateUAV.exe”, which acts as dropper for Nerbian RAT (“MoUsoCore.exe”) from a remote server.
The dropper also makes use of the open-source Chacal “anti-VM framework” to make reverse engineering difficult, using it to carry out anti-reversing checks and terminating itself should it encounter any debuggers or memory analysis programs.
The remote access trojan, for its part, is equipped to log keystrokes, capture screenshots, and execute arbitrary commands, before exfiltrating the results back to the server.
While both the dropper and the RAT are said to have been developed by the same author, the identity of the threat actor remains unknown as yet.
Furthermore, Proofpoint cautioned that the dropper could be customized to deliver different payloads in future attacks, although in its current form, it can only retrieve the Nerbian RAT.
“Malware authors continue to operate at the intersection of open-source capability and criminal opportunity,” Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said in a statement.