In this digital era, online threats are booming as much as the internet user base. Sometimes, malware infects devices due to vulnerabilities unknown to people. However, it frequently comes as a direct consequence of users’ actions. For instance, entering that suspicious website promising exclusive content or software for free. Speaking of human error, one of the most popular techniques used by hackers is fake updates.
But what are fake updates? These are malicious software downloads masquerading as legitimate updates. This type of malware is often used to infect devices with ransomware. The recent development in this is Vidar Malware. What are its risks, and how to contain them?
What is Vidar malware?
The recent fake update was discovered impersonating a Windows 11 download portal. These portals ultimately caused a Vidar malware infection. The same malware was found to be spreading through the fake InterVPN website.
Vidar is a kind of info-stealing malware that may be utilized to monitor users. This malicious software can steal login credentials, take screenshots, bank details, etc. Besides general info stealing, Vidar was also discovered downloading and executing additional malware payloads. Moreover, the malware deletes itself from the system after completing its work.
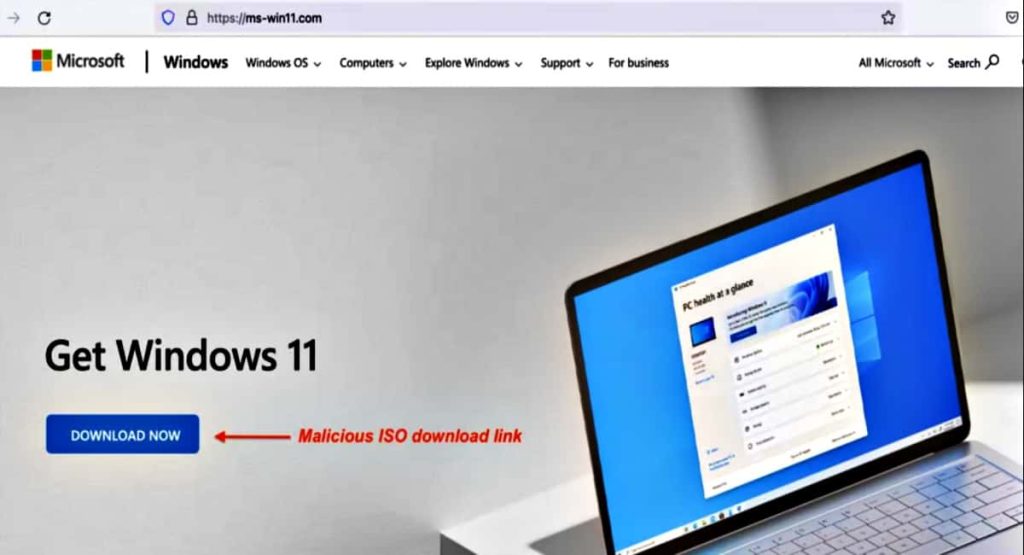
How does Vidar work?
It is being spread across the internet using phishing, fallout exploit kit, and pay-per-install PrivateLoader dropper. The email contains an attachment as a .iso disk image, which is misleadingly called “request.doc.” This ISO is mainly composed of two files: an executable (app.exe) and a Microsoft Compiled HTML Help (CHM) file (pss10r.chm).
Here’s how it enters the systems: When a notorious CHM file is loaded, a JavaScript snippet executes the app.exe. The second stage downloads and decodes the Vidar malware, which is then performed on the system.
Then, the Vidar samples communicate with their C2 server via Mastodon and Telegram. After successful communication, user profile bio sections are examined, and C2 addresses are extracted from the profiles. The malware is then copied to the target system, where it sets up its configuration and begins collecting user data.
So, this is how it hides its presence in your system. But how to save our devices from such attacks?
How to protect yourself?
Now that you know how to identify fake updates, it’s time to take measures to protect yourself. Here are some tips:
Use a firewall
This security system helps screen out incoming and outgoing network traffic. Good firewalls can often prevent malware from contacting the Command & Control server. It is how ransomware works – it needs to contact the C&C server to get a key that can encrypt your files. If it can’t reach the C&C server, it can’t get the key and thus can’t do any harm.
Protect internet connection
Your computer is only a part of the defense strategy you must employ. Malware can exploit many vulnerabilities, including unsecured networks. Luckily, you can guarantee that each network you connect to is safe.
All it takes is setting up a VPN for Windows on your laptop and enabling it whenever you use it outside the home. Public Wi-Fi can be extremely dangerous: outsiders can snoop on your activities or use security loopholes to infect your device. Therefore, remember never to connect your devices, be it a Windows laptop or an Android smartphone, to free Wi-Fi without a VPN.
Change your update settings
We often have our update settings on auto-update. It will install itself as soon as an update is available. This option should be preferred as it ensures you can have a PC running the latest operating system. If you do not schedule automatic updates, you may delay updates indefinitely.
Say no to piracy
Free software and games can be tempting but can be a source of cyberattacks. Therefore, use only licensed software. This way, you will be sure that your updates are from a trusted source. Additionally, stay away from alleged exclusive offers for programs on random websites.
Install an antivirus
An antivirus program will scan all incoming and outgoing files for a malicious activity like ransomware or adware. If it detects anything suspicious, it will alert users and recommend removal. Of course, it is essential to get a trusted antivirus program. Many fake antivirus programs could warn you about fake threats because they wish you to buy premium versions.
So, even if you accidentally click on a fake update, the antivirus will take care of it. Install updates only from official websites. It is the safest way to ensure that the update is legitimate. If you ever come across any pop-ups that look legitimate, don’t click on them. It is best to counter-check the update on the official website and then download it from there.
Always keep your system updated
The best way to know whether any update is fake is to keep your system up to date. Any unexpected update now will be quite suspicious. Moreover, updates often contain security patches that fix vulnerabilities in your system. So, it’s always a good idea to keep your system updated.
Backup your data
This is more of a precautionary measure than anything else. By backing up your data, you ensure that you won’t lose any important files even if your device gets infected with ransomware. Many cloud storage options are available these days that offer good security and are affordable.
Conclusion
Apart from these precautions, it is essential to practice safe surfing to avoid these threats from detecting your device.

