An information-stealing malware called Amadey is being distributed by means of another backdoor called SmokeLoader.
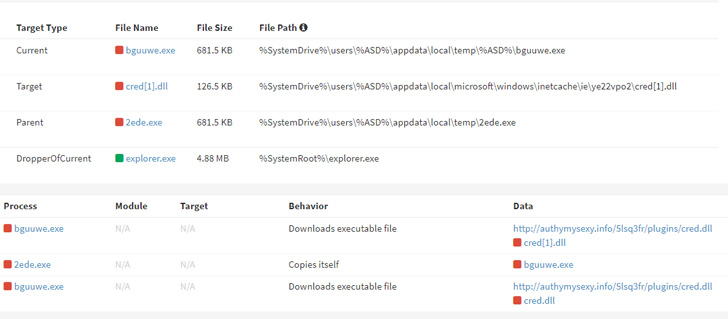
The attacks hinge on tricking users into downloading SmokeLoader that masquerades as software cracks, paving the way for the deployment of Amadey, researchers from the AhnLab Security Emergency Response Center (ASEC) said in a report published last week.
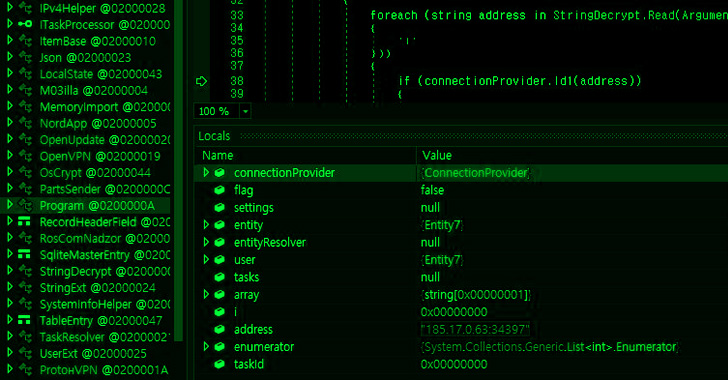
Amadey, a botnet that first appeared around October 2018 on Russian underground forums for $600, is equipped to siphon crendentials, capture screenshots, system metadata, and even information about antivirus engines and additional malware installed on an infected machine.
While an update was spotted last July by Walmart Global Tech incorporated functionality for harvesting data from Mikrotik routers and Microsoft Outlook, the toolset has since been upgraded to capture information from FileZilla, Pidgin, Total Commander FTP Client, RealVNC, TightVNC, TigerVNC, and WinSCP.
Its main goal, however, is to deploy additional plugins and remote access trojans such as Remcos RAT and RedLine Stealer, further enabling the threat actor to conduct an array of post-exploitation activities.
Users are recommended to upgrade their devices to the latest versions of the operating system and the web browser to minimize potential infection routes and steer clear of pirated software.