A nascent service called Dark Utilities has already attracted 3,000 users for its ability to provide command-and-control (C2) services with the goal of commandeering compromised systems.
“It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems,” Cisco Talos said in a report shared with The Hacker News.
Dark Utilities, which emerged in early 2022, is advertised as a “C2-as-a-Service” (C2aaS), offering access to infrastructure hosted on the clearnet as well as the TOR network and associated payloads with support for Windows, Linux, and Python-based implementations for a mere €9.99.
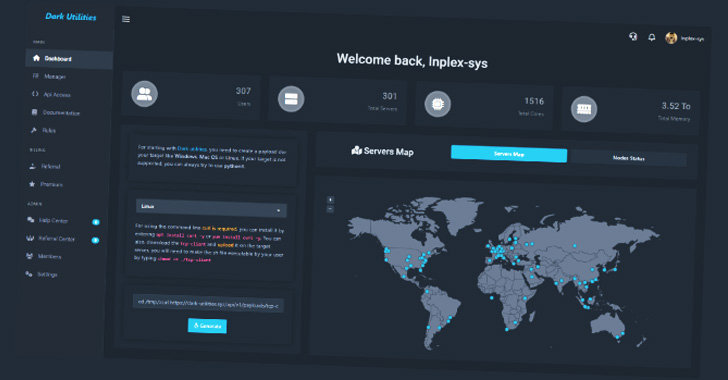
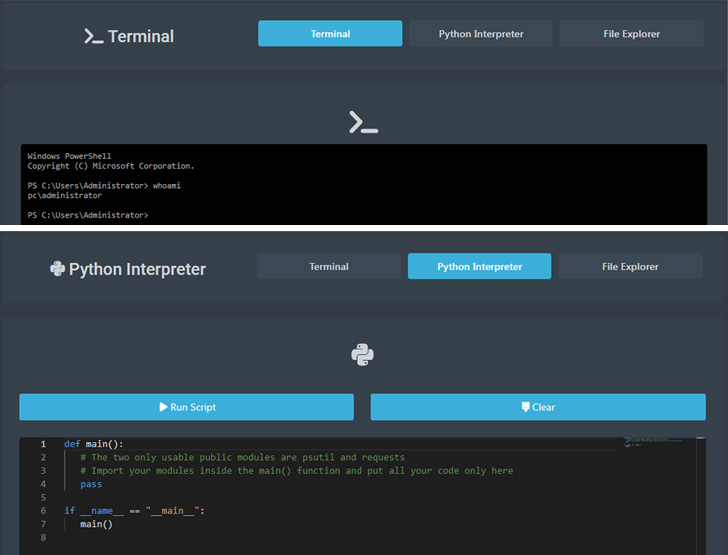
Authenticated users on the platform are presented with a dashboard that makes it possible to generate new payloads tailored to a specific operating system that can then be deployed and executed on victim hosts.
Additionally, users are provided an administrative panel to run commands on the machines under their control upon establishing an active C2 channel, effectively granting the attacker full access to the systems.
The idea is to enable threat actors to target multiple architectures without requiring significant development efforts. Also extended to its customers are technical support and assistance through Discord and Telegram.
“Given the relatively low cost compared to the amount of functionality the platform offers, it is likely attractive to adversaries attempting to compromise systems without requiring them to create their own C2 implementation within their malware payloads,” the researchers noted.
To add fuel to the fire, the malware artifacts are hosted within the decentralized InterPlanetary File System (IPFS) solution, making them resilient to content moderation or law enforcement intervention in a manner similar to “bulletproof hosting.”
“IPFS is currently being abused by a variety of threat actors who are using it to host malicious contents as part of phishing and malware distribution campaigns,” Talos researcher Edmund Brumaghin told The Hacker News.
“[The IPFS gateway] enables computers on the internet to access contents hosted within the IPFS network without the requirement for a client software installation, similar to how Tor2Web gateways provide that functionality for content hosted within the Tor network.”
Dark Utilities is believed to be the handiwork of a threat actor who goes by the moniker Inplex-sys in the cybercriminal underground space, with Talos identifying some sort of a “collaborative relationship” between Inplex-sys and one of the operators of a botnet service called Smart Bot.
“Platforms like Dark Utilities lower the barrier to entry for cybercriminals entering the threat landscape by enabling them to quickly launch attacks targeting a variety of operating systems,” the researchers said.
“They also offer multiple methods that can be used to further monetize access gained to systems in corporate environments and could lead to further deployment of malware in the environment once initial access has been obtained.”