Check Point researchers have shared details of a new campaign in which the cybercriminals are distributing cryptocurrency-mining malware. This malware is hard to detect by unsuspecting users because it is distributed through fake and malicious Google Translate and other popular apps.
According to researchers, the malware is spread via third-party websites hosted on platforms like Uptodown and Softpedia and offer free software downloads. These websites can be accessed through a simple Google search.
Campaign Analysis
The cryptocurrency mining Trojan is called Nitrokod. It is spread disguised as a clean Windows application. The malware keeps its execution on hold for several days or weeks and launches its Monero mining code when it deems safe.
This malware is readily available, and anyone can use it, stated Check Point’s vice president of research, Maya Horowitz. The list of victims is pretty diverse as they are spread across the following countries:
- Israel
- Turkey
- Cyprus
- Greece
- Poland
- Germany
- Australia
- Mongolia
- Sri Lanka
- United States
- United Kingdom
Malware analyst at Check Point Moshe Marelus stated that the malware drops around one month after the infection, and dropping files is a multi-stage process, which makes it rather complicated to track its initial stages.
Attack Tactics
The attack is a multi-stage sequence where each dropper paves the way for another dropper until the actual malware is dropped. The app runs as expected when the user downloads and installs the software loaded with Nitrokod malware while the malicious trojan sneakily works in the background. It fetches and stores several executables and schedules one .exe file to run every day once they are unpacked.
When the files are run, another executable file is extracted, which establishes a connection to a C2 server, obtains device configuration settings for the Monero miner code, and the mining process starts. The generated coins are sent to the attackers’ wallets. At some point, all initial stage files self-delete, and the next stage of the infection chain starts after fifteen days through the Windows utility schtasks.exe.
“This way, the first stages of the campaign are separated from the ones that follow, making it very hard to trace the source of the infection chain and block the initial infected applications.”
Moshe Marelus – Check Point
The malware also inspects for known virtual machine processes and installed security products. If detected, the program stalls and exits.
One stage also checks for known virtual-machine processes and security products. If found, the program exits. If not, it continues. Cybercriminals use RAR encrypted, password-protected files throughout the stages to make them hard to detect.
Who Are the Attackers?
CheckPoint’s research suggests that a Turkish-speaking group of hackers dubbed Nitrokod is behind this campaign revealed Check Point Research’s team. It has been active since 2019. This campaign was discovered in July 2022, and so far, it has affected 111,000 users in 11 countries.
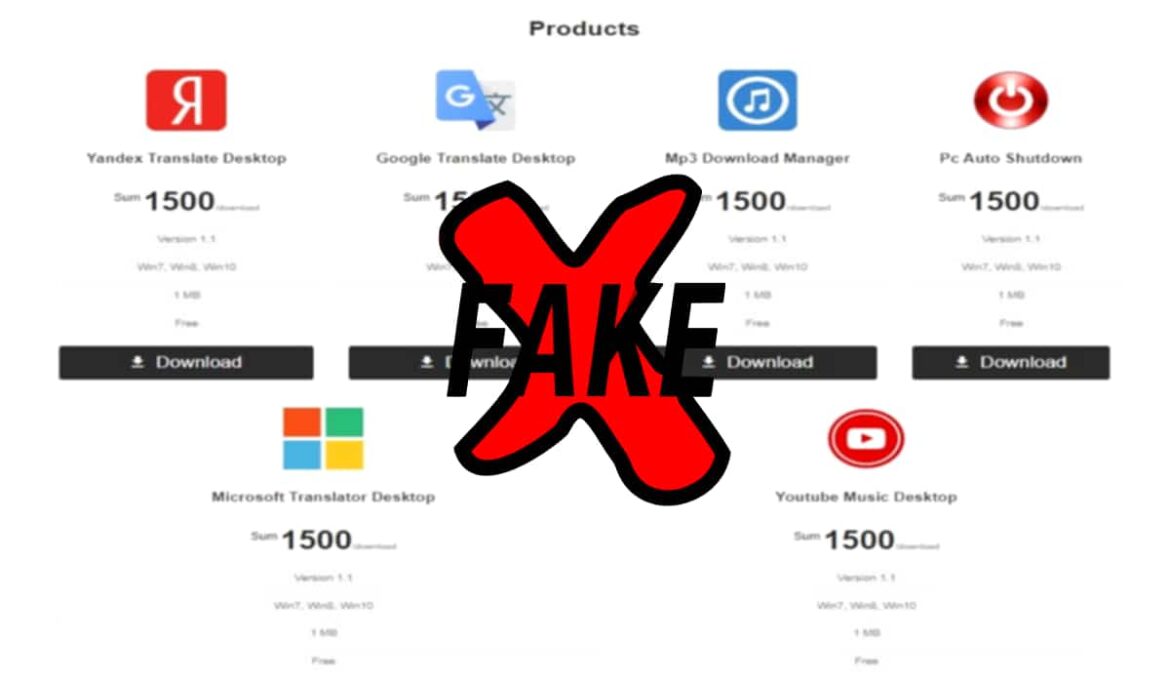
The modus operandi used to trap users is by offering desktop versions of legit apps that don’t have their desktop versions. Nitrokod programmers wait patiently before launching the malware, and their attacks entail multiple stages.
Software Exploited
Apart from Google Translate, Nitrokod leveraged other translation apps, e.g., YouTube Music, Microsoft Translator Desktop and MP3 downloader programs. The malicious apps claim to be 100% clean but contain a crypto miner.
Related News
- Google ReCaptcha flaw lets bots bypass audio captcha challenge
- Fake Brave browser website dropped malware, thanks to Google Ads
- Google, Microsoft and Oracle generated the most vulnerabilities in 2021
- Google shares details of unpatched Windows AppContainer vulnerability
- Google Drive accounted for 50% of malicious Office document downloads