The operators of the XCSSET macOS malware have upped the stakes by making iterative improvements that add support for macOS Monterey by upgrading its source code components to Python 3.
“The malware authors have changed from hiding the primary executable in a fake Xcode.app in the initial versions in 2020 to a fake Mail.app in 2021 and now to a fake Notes.app in 2022,” SentinelOne researchers Phil Stokes and Dinesh Devadoss said in a report.
XCSSET, first documented by Trend Micro in 2020, has many moving parts that allow it to harvest sensitive information from Apple Notes, WeChat, Skype, and Telegram; inject malicious JavaScript code into various websites; and dump cookies from Safari web browser.
Infection chains entail using a dropper to compromise users’ Xcode projects with the backdoor, with the latter also taking steps to evade detection by masquerading as either system software or the Google Chrome web browser application.
The primary executable is an AppleScript that’s designed to retrieve second-stage AppleScript payloads from a network of remote servers that siphon data stored in web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, Brave, and Yandex Browser as well as chat apps like Telegram and WeChat.
The threat actor is also known to use a custom AppleScript (“listing.applescript”) to determine “how up-to-date the victim is with Apple’s XProtect and MRT malware removal tool, presumably all the better to target them with more effective payloads,” the researchers said.
One of the novel aspects of the attack is that deploying the malware within Xcode projects is seen as a method of propagation via GitHub repositories to further expand its reach.
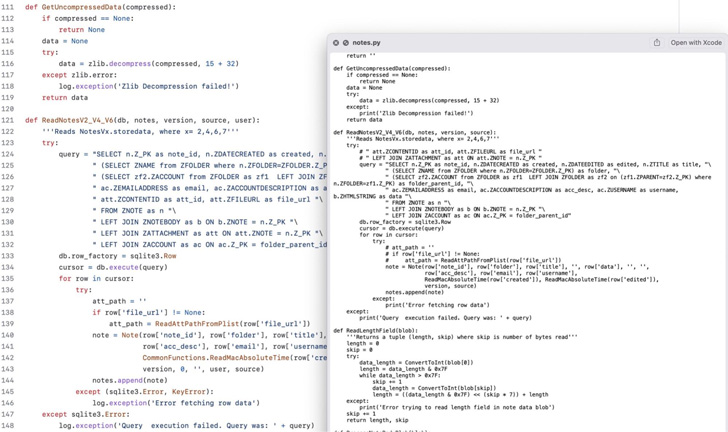
Besides leveraging AppleScripts, the malware also takes advantage of Python scripts for dropping fake application icons on the macOS Dock and stealing data from the legitimate Notes app.
The latest version of XCSSET is also notable for incorporating modifications to AppleScripts to account for Apple’s removal of Python 2.7 from macOS 12.3 released on March 14, 2022, indicating that the authors are continually updating the malware to increase their chance of success.
To that end, the adversary is said to have updated their “safari_remote.applescript” by eliminating Python 2 in favor of Python 3 for systems running macOS Monterey 12.3 and above.
Despite being in the wild for two years, very little is known about the identity of the threat actors and their motivations or their exact targets. That said, XCSSET malware attacks have been reported in China as recently as May 2022 that demanded victims pay 200 USDT in return for unlocking stolen accounts.
“At this point in time, it’s unclear whether these infected repos are victims or plants by threat actors hoping to infect unwary users,” the researchers noted. “It has been suggested that unsuspecting users may be pointed to the infected repositories through tutorials and screencasts for novice developers.”