A previously undocumented strain of Android spyware with extensive information gathering capabilities has been found disguised as a book likely designed to target the Uyghur community in China.
The malware comes under the guise of a book titled “The China Freedom Trap,” a biography written by the exiled Uyghur leader Dolkun Isa.
“In light of the ongoing conflict between the Government of the People’s Republic of China and the Uyghur community, the malware disguised as the book is a lucrative bait employed by threat actors (TAs) to spread malicious infection in the targeted community,” cybersecurity firm Cyble said in a report published Monday.
The existence of the malware samples, which come with the package name “com.emc.pdf,” was first disclosed by researchers from the MalwareHunterTeam late last month.
Distributed outside of the official Google Play Store, the app, once installed and opened, displays a few pages of the book, including the cover page, an introduction, and a letter purportedly sent by Michael Kozak and Sam Brownback to Isa on June 15, 2018, condoling his mother’s death.
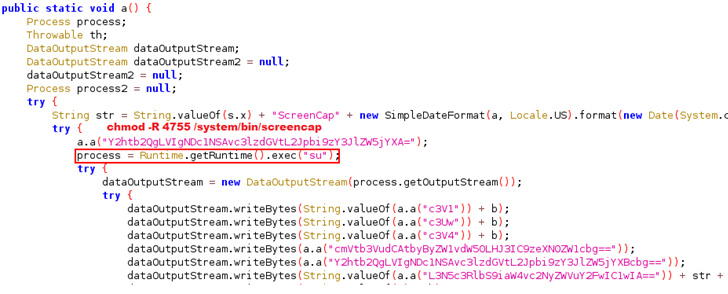
In reality, however, the malicious APK file is engineered to:
- hide app icon,
- steal device and SIM information,
- steal SMS messages, contacts and call logs,
- identify neighboring cell information (received signal strength, Cell ID location),
- make Calls and Send SMSs on behalf of victims,
- delete SMS and call logs,
- as well as take pictures from the infected device’s camera and capture its screen.
“TAs are leveraging various methods, including regional and biogeographical conflicts, to fulfill their malicious intentions,” the researchers said. “In this case, they are seen taking advantage of the Uyghur-Chinese conflict to target unsuspecting individuals.”