The Android malware tracked as BRATA has been updated with new features that grants it the ability to track device locations and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers.
The latest variants, detected late last year, are said to be distributed through a downloader to avoid being detected by security software, Italian cybersecurity firm Cleafy said in a technical write-up. Targets include banks and financial institutions in the U.K., Poland, Italy, and Latin America.
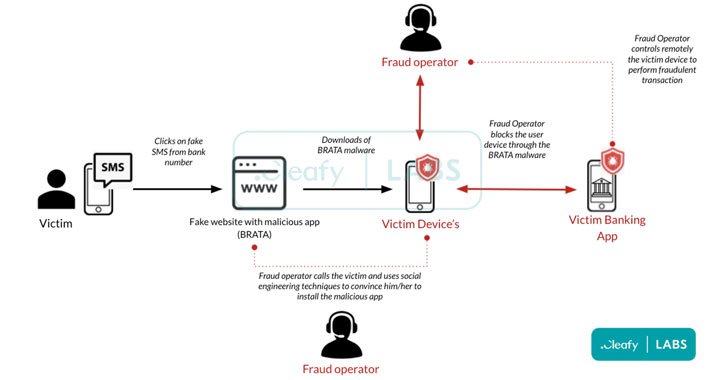
“What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device,” Cleafy researchers noted in December 2021. “By doing so, Threat Actors (TAs) can drastically reduce the possibility of being flagged “as suspicious”, since the device’s fingerprinting is already known to the bank.”
First seen in the wild at the end of 2018 and short for “Brazilian Remote Access Tool Android,” BRATA initially targeted users in Brazil and then rapidly evolved into a feature-packed banking trojan. Since then, the malware has received numerous upgrades and changes, while also posing as security scanner apps to elude detection.
The latest “tailored” samples of BRATA set aim at different countries and constitute an initial dropper — a security app dubbed “iSecurity” — that remains undetected by virtually all malware scanning engines and is used to download and execute the real malicious software.
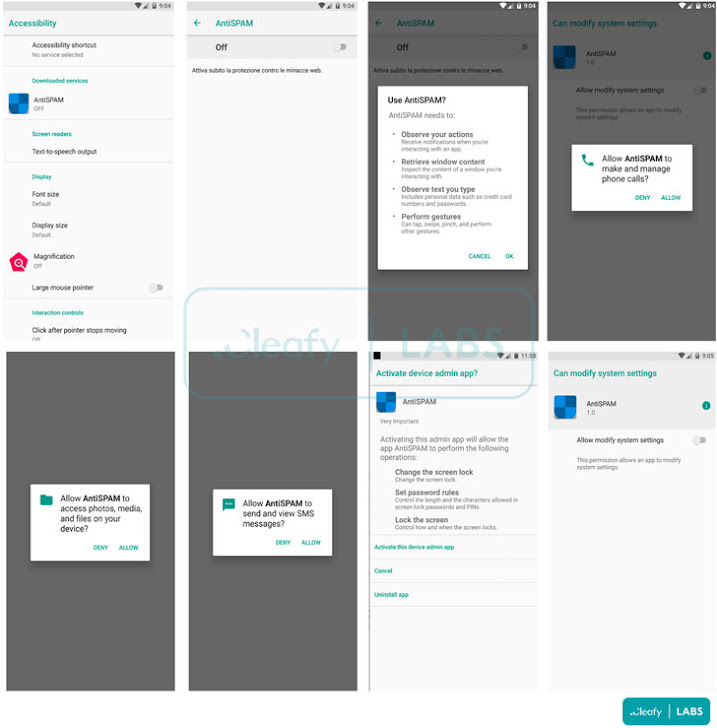
“After the victim installs the downloader app, it requires accepting just one permission to download and install the malicious application from an untrusted source,” the researchers said. “When the victim clicks on the install button, the downloader app sends a GET request to the C2 server to download the malicious .APK.”
BRATA, like other banking trojans observed in the wild, is known to abuse its Accessibility Service permissions obtained during the installation phase to monitor the user’s activity on the compromised device stealthily.
Furthermore, the new versions have incorporated a kill switch mechanism that allows the operators to restore the Android phone to its factory settings upon successfully completing a fraudulent wire transfer or in scenarios where the application is installed in a virtual environment.
“BRATA is trying to reach out to new targets and to develop new features,” the researchers said, adding threat actors are “leveraging this banking trojan for performing frauds, typically through unauthorized wire transfer (e.g., SEPA) or through Instant Payments, using a wide network of money mules accounts in multiple European countries.”