A previously undocumented espionage tool has been deployed against selected governments and other critical infrastructure targets as part of a long-running espionage campaign orchestrated by China-linked threat actors since at least 2013.
Broadcom’s Symantec Threat Hunter team characterized the backdoor, named Daxin, as a technologically advanced malware, allowing the attackers to carry out a variety of communications and information-gathering operations aimed at entities in the telecom, transportation, and manufacturing sectors that are of strategic interest to China.
“Daxin malware is a highly sophisticated rootkit backdoor with complex, stealthy command-and-control (C2) functionality that enables remote actors to communicate with secured devices not connected directly to the internet,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in an independent advisory.
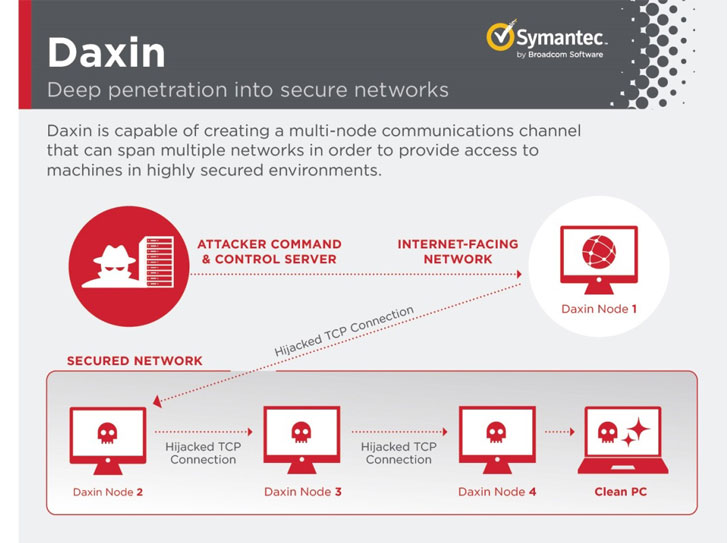
The implant takes the form of a Windows kernel driver that implements an elaborate communications mechanism that affords the malware a high degree of stealth and the capability to talk to machines that are physically disconnected from the internet.
It achieves this by expressly avoiding launching its own network services, instead opting to take advantage of legitimate TCP/IP services already running on the infected computers to blend its communications with normal traffic on the target’s network and receive commands from a remote peer.
“These features are reminiscent of Regin,” the researchers noted, referring to another sophisticated malware and hacking toolkit attributed to the U.S. National Security Agency (NSA) for government spying operations back in 2014.
Among the unusual aspects of Daxin, besides generating no suspicious network traffic to remain unseen, is its ability to relay commands across a network of infected computers within the attacked organization, creating a “multi-node communications channel” that permits recurring access to the compromised computers for extended periods of time.
While recent intrusions involving the backdoor are said to have transpired in November 2021, Symantec said it uncovered code-level commonalities with an older piece of malware called Exforel (aka Zala), indicating that Daxin may have been built by an actor with access to the latter’s codebase or that they are the work of the same group.
The campaigns have not been attributed to a single adversary, but a timeline of the attacks shows that Daxin was installed on some of the same systems where tools associated with other Chinese espionage actors like Slug were found. This includes the deployment of both Daxin and Owprox malware on a single computer belonging to a tech company in May 2020.
“Daxin is without doubt the most advanced piece of malware […] used by a China-linked actor,” the researchers said. “Considering its capabilities and the nature of its deployed attacks, Daxin appears to be optimized for use against hardened targets, allowing the attackers to burrow deep into a target’s network and exfiltrate data without raising suspicions.”
The disclosure arrives a week after China-based Pangu Lab outed a “top-tier” backdoor called Bvp47 put to use by the U.S. National Security Agency for over a decade targeting as many as 287 organizations in 45 countries located chiefly in China, Korea, Japan, Germany, Spain, India, and Mexico.