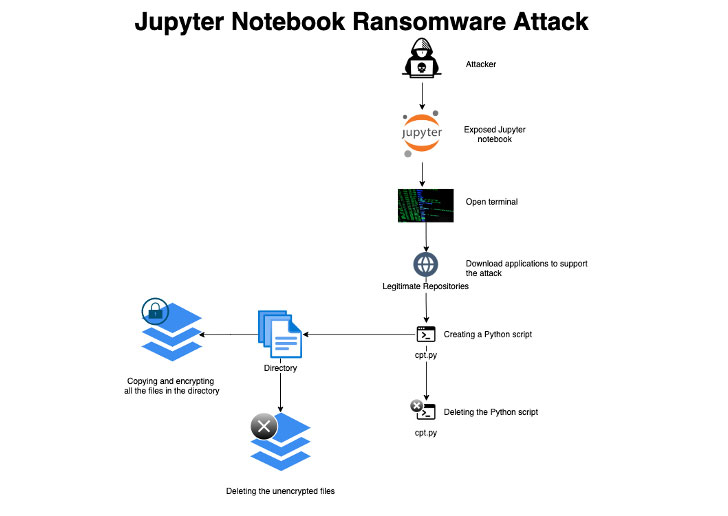
Researchers have disclosed what they say is the first-ever Python-based ransomware strain specifically designed to target exposed Jupyter notebooks, a web-based interactive computing platform that allows editing and running programs via a browser.
“The attackers gained initial access via misconfigured environments, then ran a ransomware script that encrypts every file on a given path on the server and deletes itself after execution to conceal the attack,” Assaf Morag, a data analyst at Aqua Security, said in a report.
The new ransomware sample, which the cloud security firm detected after it was trapped in one of its honeypot servers, is said to have been executed after the unnamed adversary gained access to the server and downloaded the necessary tools required to carry out the encryption process by opening a terminal.
Aqua Security characterized the attack as “simple and straightforward,” unlike other traditional ransomware-as-a-service (RaaS) schemes, adding that no ransom note was presented on the system, raising the possibility that the threat actor may have been experimenting with the modus operandi, or that the honeypot timed out before it could be complete.
The identity of the attacker remains unclear, although evidence unearthed during the incident analysis points to an actor of Russian origin, citing similarities with previous cryptomining attacks aimed at Jupyter notebooks.
“Since Jupyter notebooks are used to analyze data and build data models, this attack can lead to significant damage to organizations if these environments aren’t properly backed up,” Morag said.