At least three different advanced persistent threat (APT) groups from across the world have launched spear-phishing campaigns in mid-March 2022 using the ongoing Russo-Ukrainian war as a lure to distribute malware and steal sensitive information.
The campaigns, undertaken by El Machete, Lyceum, and SideWinder, have targeted a variety of sectors, including energy, financial, and governmental sectors in Nicaragua, Venezuela, Israel, Saudi Arabia, and Pakistan.
“The attackers use decoys ranging from official-looking documents to news articles or even job postings, depending on the targets and region,” Check Point Research said in a report. “Many of these lure documents utilize malicious macros or template injection to gain an initial foothold into the targeted organizations, and then launch malware attacks.”
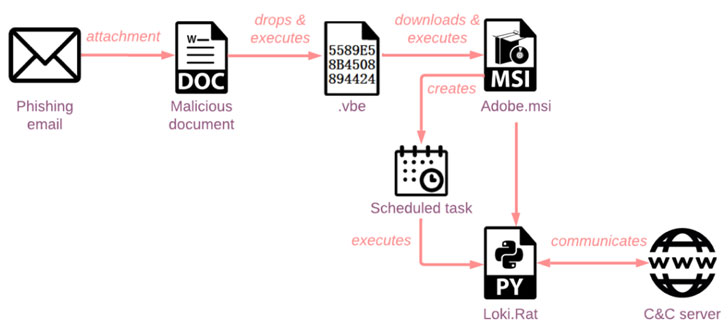
The infection chains of El Machete, a Spanish-speaking threat actor first documented in August 2014 by Kaspersky, involve the use of macro-laced decoy documents to deploy an open-source remote access trojan called Loki.Rat that’s capable of harvesting keystrokes, credentials, and clipboard data as well as carrying out file operations and executing arbitrary commands.
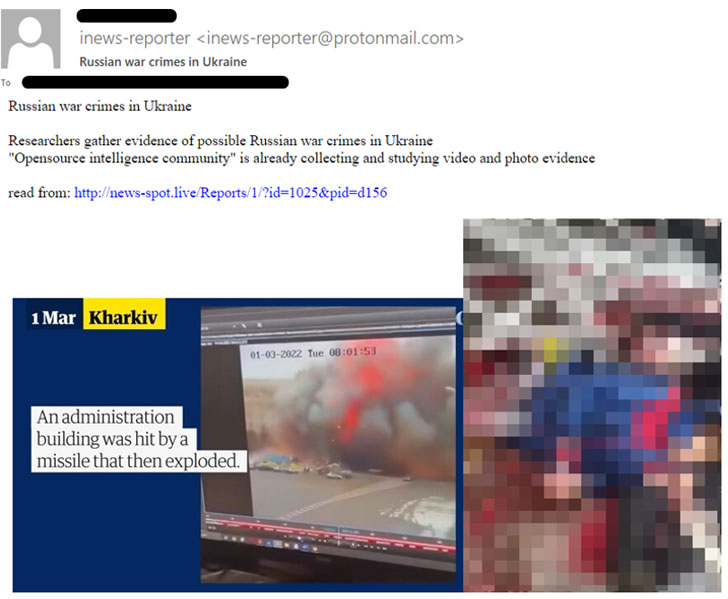
A second campaign is from the Iranian APT group known as Lyceum that Check Point said launched a phishing attack using an email purportedly about “Russian war crimes in Ukraine” to deliver first-stage .NET and Golang droppers, which are then used to deploy a backdoor for running files retrieved from a remote server.
Another example is SideWinder, a state-sponsored crew that’s said to operate in support of Indian political interests and with a specific focus on its neighbors China and Pakistan. The attack sequence, in this case, employs a weaponized document that exploits the Equation Editor flaw in Microsoft Office (CVE-2017-11882) to distribute information stealing malware.
The findings echo similar warnings from Google’s Threat Analysis Group (TAG), which disclosed that nation-state-backed threat groups from Iran, China, North Korea, and Russia and numerous other criminal and financially motivated actors are leveraging war-related themes in phishing campaigns, online extortion attempts, and other malicious activities.
“Although the attention of the public does not usually linger on a single issue for an extended period, the Russian-Ukrainian war is an obvious exception,” the Israeli company said. “This war affects multiple regions around the world and has potentially far-reaching ramifications. As a result, we can expect that APT threat actors will continue to use this crisis to conduct targeted phishing campaigns for espionage purposes.”