Cybersecurity researchers have detailed a “simple but efficient” persistence mechanism adopted by a relatively nascent malware loader called Colibri, which has been observed deploying a Windows information stealer known as Vidar as part of a new campaign.
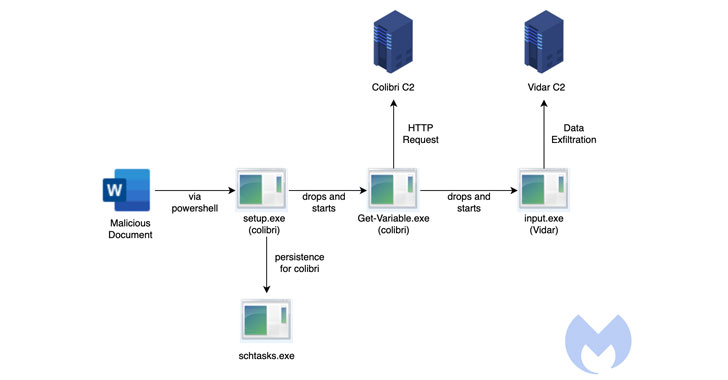
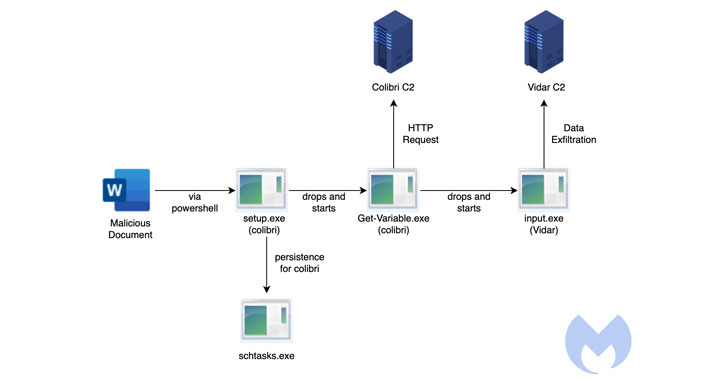
“The attack starts with a malicious Word document deploying a Colibri bot that then delivers the Vidar Stealer,” Malwarebytes Labs said in an analysis. “The document contacts a remote server at (securetunnel[.]co) to load a remote template named ‘trkal0.dot’ that contacts a malicious macro,” the researchers added.
First documented by FR3D.HK and Indian cybersecurity company CloudSEK earlier this year, Colibri is a malware-as-a-service (MaaS) platform that’s engineered to drop additional payloads onto compromised systems. Early signs of the loader appeared on Russian underground forums in August 2021.
“This loader has multiple techniques that help avoid detection,” CloudSEK researcher Marah Aboud noted last month. “This includes omitting the IAT (Import Address Table) along with the encrypted strings to make the analysis more difficult.”
The campaign attack chain observed by Malwarebytes takes advantage of a technique called remote template injection to download the Colibri loader (“setup.exe”) by means of a weaponized Microsoft Word document.
The loader then makes use of a previously undocumented persistence method to survive machine reboots, but not before dropping its own copy to the location “%APPDATA%LocalMicrosoftWindowsApps” and naming it “Get-Variable.exe.”
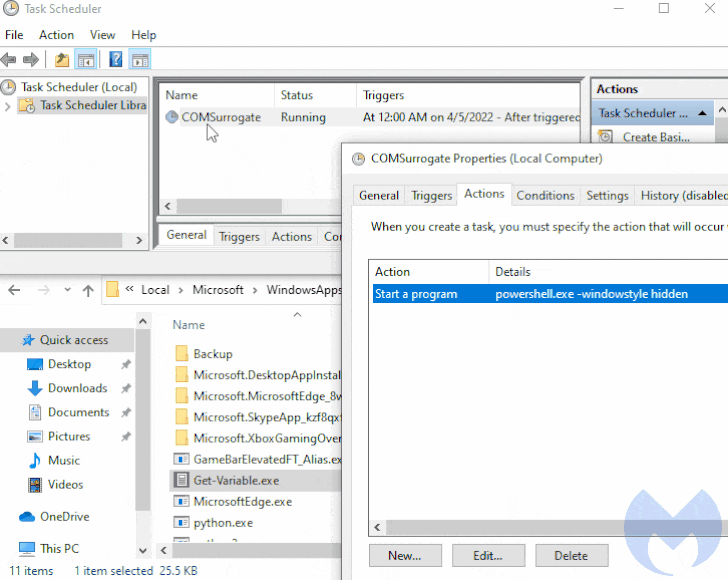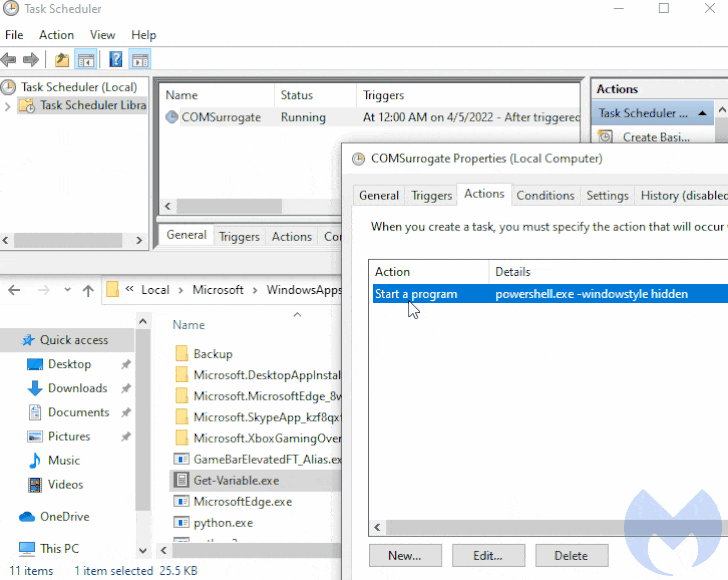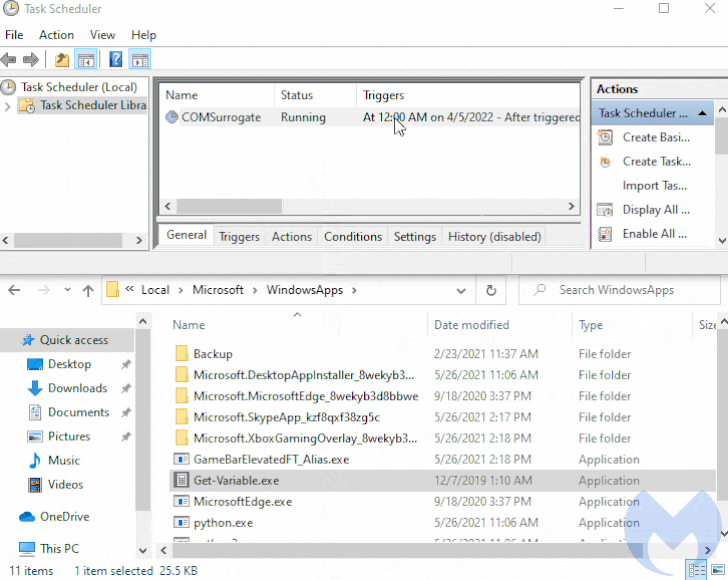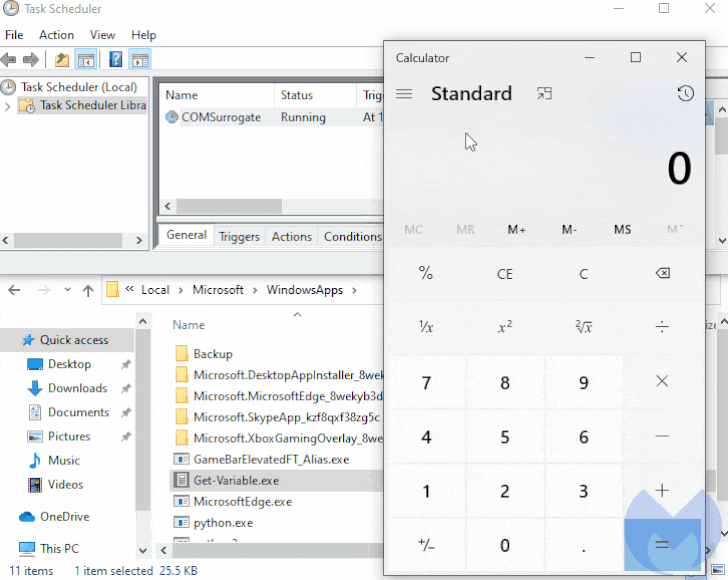
It achieves this by creating a scheduled task on systems running Windows 10 and above, with the loader executing a command to launch PowerShell with a hidden window (i.e., -WindowStyle Hidden) to conceal the malicious activity from being detected.
“It so happens that Get-Variable is a valid PowerShell cmdlet (a cmdlet is a lightweight command used in the Windows PowerShell environment) which is used to retrieve the value of a variable in the current console,” the researchers explained.
But given the fact that PowerShell is executed by default in the WindowsApps path, the command issued during the scheduled task creation results in the execution of the malicious binary in the place of its legitimate counterpart.
This effectively means that “an adversary can easily achieve persistence [by] combining a scheduled task and any payload (as long as it is called Get-Variable.exe and placed in the proper location),” the researchers said.
The latest findings come as cybersecurity company Trustwave last month detailed an email-based phishing campaign that leverages Microsoft Compiled HTML Help (CHM) files to distribute the Vidar malware in an effort to fly under the radar.