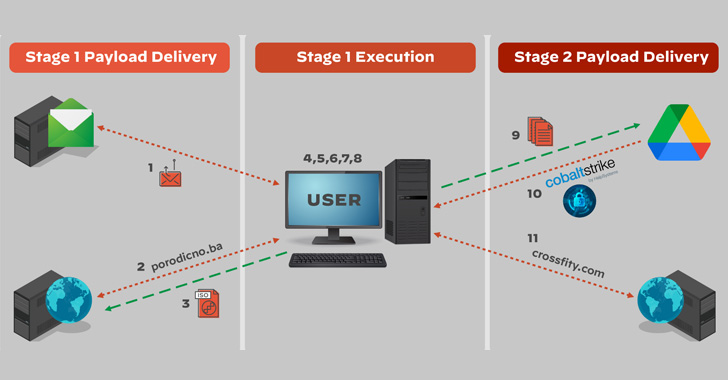
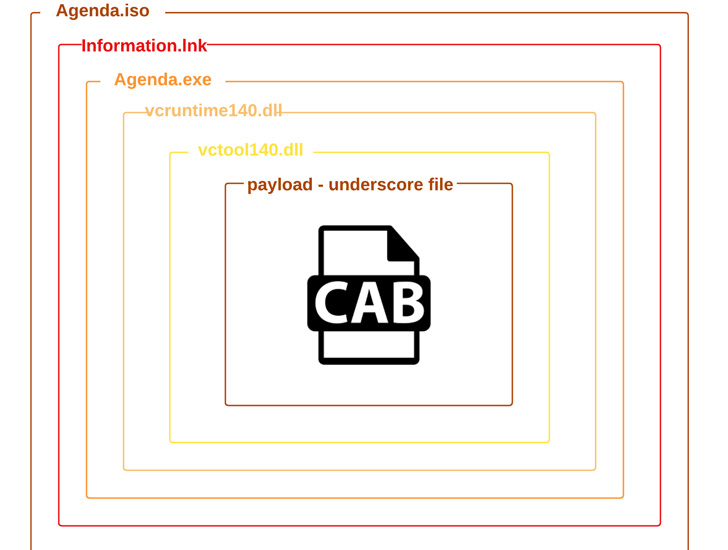
The Russian state-sponsored hacking collective known as APT29 has been attributed to a new phishing campaign that takes advantage of legitimate cloud services like Google Drive and Dropbox to deliver malicious payloads on compromised systems.
“These campaigns are believed to have targeted several Western diplomatic missions between May and June 2022,” Palo Alto Networks Unit 42 said in a Tuesday report. “The lures included in these campaigns suggest targeting of a foreign embassy in Portugal as well as a foreign embassy in Brazil.”
APT29, also tracked under the monikers Cozy Bear, Cloaked Ursa, or The Dukes, has been characterized as an organized cyberespionage group working to collect intelligence that aligns with Russia’s strategic objectives.
Some aspects of the advanced persistent threat’s activities, including the infamous SolarWinds supply chain attack of 2020, are separately tracked by Microsoft under the name Nobelium, with Mandiant calling it an evolving, disciplined, and highly skilled threat actor that operates with a heightened level of operational security.”
The most recent intrusions are a continuation of the same covert operation previously detailed by Mandiant and Cluster25 in May 2022, in which the spear-phishing emails led to the deployment of Cobalt Strike Beacons by means of an HTML dropper attachment dubbed EnvyScout (aka ROOTSAW) attached directly to the missives.
What’s changed in the newer iterations is the use of cloud services like Dropbox and Google Drive to conceal their actions and retrieve additional malware into target environments. A second version of the attack observed in late May 2022 is said to have adapted further to host the HTML dropper in Dropbox.
“The campaigns and the payloads analyzed over time show a strong focus on operating under the radar and lowering the detection rates,” Cluster25 noted at the time. “In this regard, even the use of legitimate services such as Trello and Dropbox suggest the adversary’s will to operate for a long time within the victim environments remaining undetected.”
EnvyScout, for its part, serves as an auxiliary tool to further infect the target with the actor’s implant of choice, in this case, a .NET-based executable that’s concealed in multiple layers of obfuscation and used to exfiltrate system information as well as execute next-stage binaries such as Cobalt Strike fetched from Google Drive.
“The use of DropBox and Google Drive services […] is a new tactic for this actor and one that proves challenging to detect due to the ubiquitous nature of these services and the fact that they are trusted by millions of customers worldwide,” the researchers said.
The findings also coincide with a new declaration from the Council of the European Union, calling out the spike in malicious cyber activities perpetrated by Russian threat actors and “condemn[ing] this unacceptable behavior in cyberspace.”
“This increase in malicious cyber activities, in the context of the war against Ukraine, creates unacceptable risks of spillover effects, misinterpretation and possible escalation,” the Council said in a press statement.