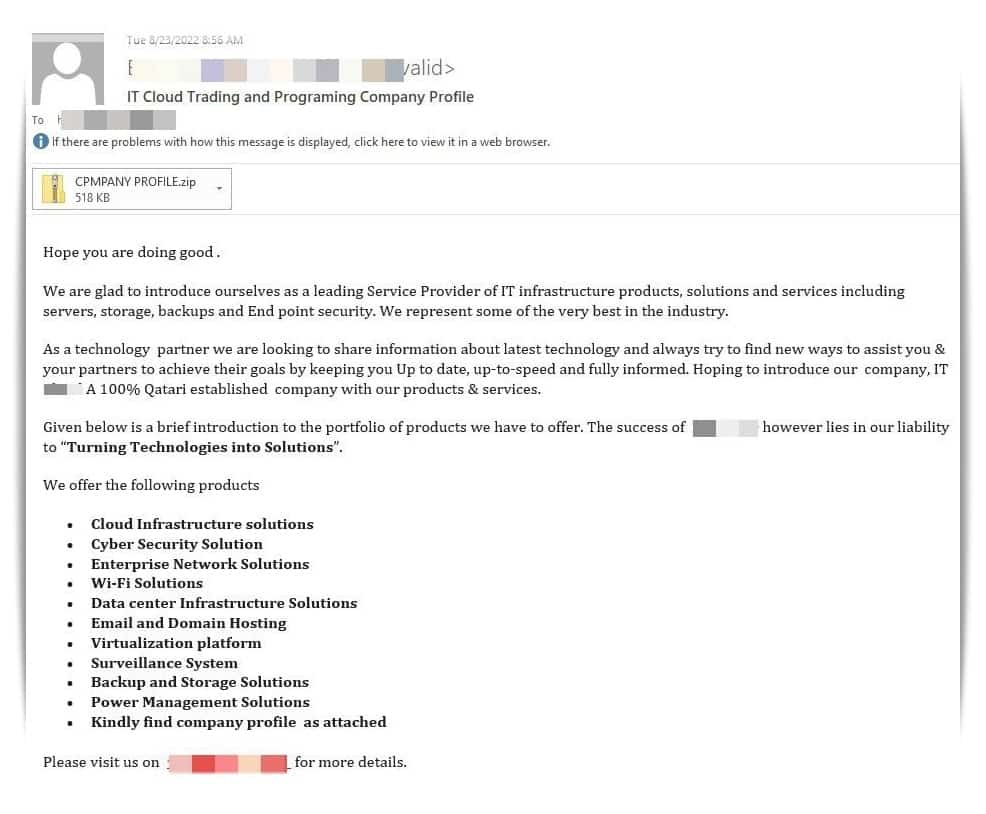
Snake Keylogger is back in action with a brand new malspam campaign spreading via phishing emails sent to corporate IT enterprises’ managers. Bitdefender Antispam Labs discovered the campaign on 23 August 2022.
What is a Keylogger?
A keylogger is a type of malicious software that records your keystrokes and sends them to a hacker. Keyloggers can be installed on your computer without your knowledge, usually through a malicious email attachment or infected website.
In some cases, attackers may use a physical keylogger on your device in shape of a malicious USB drive or a customized phone charging cable, etc.
Campaign Analysis
According to Bitdefender analysts, the IP addresses used in the attack originated from Vietnam, while the campaign’s primary targets were located in the USA, and thousands of inboxes have received the phishing email.
Attackers leverage the corporate profile of one of Qatar’s leading IT and cloud services providers to trap victims into opening a ZIP archive. This archive has an executable file titled “CPMPANY PROFILE.exe.”
This file, according to Bitdefender’s blog post, loads the notorious Snake Keylogger payload on the targeted system’s host. The data is exfiltrated through SMTP.
What is Snake Keylogger?
It is an infamous credential and info-stealing malware that exfiltrates sensitive data from infected machines. It has screenshot capturing and keyboard logging capabilities. It is a huge threat to enterprises because of its spying and data harvesting features.
In addition to that, it can steal information from system clipboards. It is also called 404 Keylogger. The trojan surfaced in 2020 and is currently available at underground marketplaces/message boards for a few hundred dollars. The malware is used commonly in financially motivated campaigns, including identity theft and fraud-based campaigns.
How to Protect Yourself?
A keylogger records every keystroke you make, giving hackers access to your personal information, passwords, and financial data. But there are steps you can take to protect yourself.
The best way to protect your device is by verifying the validity and origin of correspondence before clicking on any attachment. Also, install the industry’s most reliable security solutions and protect your accounts with 2FA or MFA processes.
Related News
- US Warns Firms About North Korean Hackers Posing as IT Workers
- Cisco Confirms Breach After Employee’s Google Account was Hacked
- Twitter Confirms Data Breach as 5.4M Accounts Sold on Hacker Forum
- Hackers posing as LinkedIn recruiters to scam military, aerospace firms
- Hackers hit Europe’s largest healthcare provider with Snake ransomware