Hundreds of Linksys good routers world wide can leak consumer information to hackers. In accordance with a researcher, a vulnerability current in numerous fashions of Linksys Good WiFi routers world wide makes the customers weak to hacks. What’s upsetting right here is that the seller doesn’t at present think about the issue worthy of a repair.
Linksys Good WiFi Routers Vulnerability
Reportedly, a researcher Troy Mursch has found a severe vulnerability affecting varied fashions of Linksys Good WiFi routers. Explaining his findings in a blog post, Mursch revealed that the vulnerability can disclose delicate consumer data to a possible attacker upon an exploit.
We’ve found a persistent flaw affecting Linksys Good Wi-Fi routers that enables unauthenticated distant entry to delicate data.
An attacker with even little technical information can exploit the vulnerability with out requiring authentication. The exploit is fairly easy. An attacker merely has to go to the developer console upon after opening the router’s public IP handle within the net browser. Then scrolling right down to the JNAP will reveal the main points.
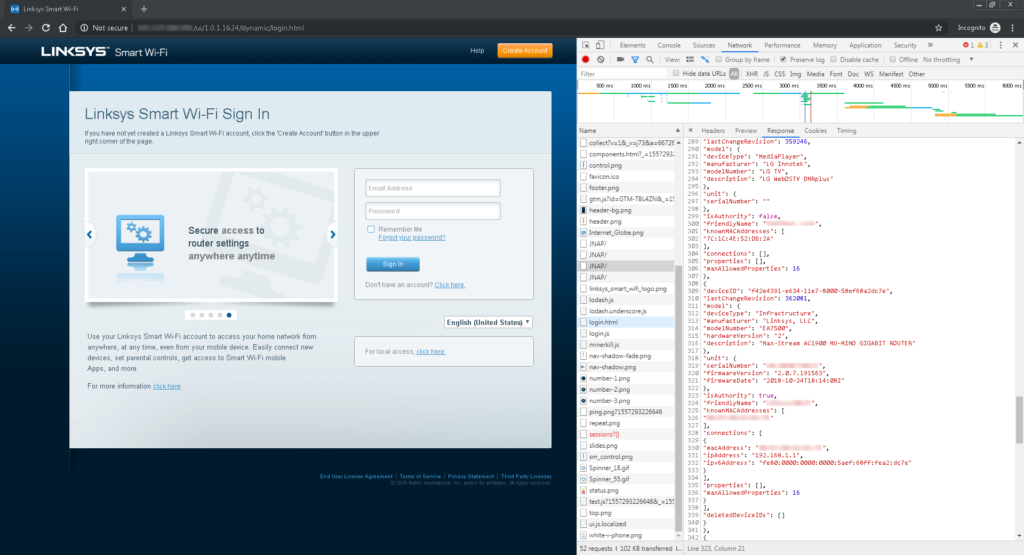
In accordance with Mursch, as a lot as 25,617 routers are exploitable via this vulnerability. The leaked information might embody gadget names, working system data, and full historic file of MAC addresses of units ever related. Whereas, in some circumstances, the uncovered data contains extra logs, resembling gadget kind, mannequin quantity, producer data, an outline, and system information resembling WAN settings, firmware replace settings, firewall standing, and DDNS settings.
An entire listing of units actively leaking the data is accessible on this link.
Vendor Refused A Repair
Whereas discussing the dangers related to this flaw, Mursch acknowledged,
This data permits attackers to achieve visibility inside your own home or enterprise community, enabling them to conduct focused assaults.
The exploit will be worst in case of units with default admin credentials. This contains virtually the whole lot from accessing the SSID credentials to hijacking net site visitors and concentrating on units behind the router. A possible attacker can scan for such units through the vulnerability found.
Satirically, the distributors don’t deem this vulnerability value a patch. Allegedly, they closed the researcher’s report with a “Not relevant / Received’t repair” standing.
Sadly, there appears no direct workaround both to mitigate the flaw. The customers of some fashions can, nonetheless, think about using a third-party firmware.
Most (however not all) fashions have the choice of utilizing third-party firmware, resembling OpenWrt, that may disable distant entry and forestall the leak of delicate data.
Take your time to touch upon this text.

