Android customers now face one other menace from a newly found malware marketing campaign. Termed ‘Bouncing Golf’ by the researchers, the brand new marketing campaign actively targets Android gadgets, significantly within the Center East. The marketing campaign infects Android gadgets with ‘GolfSpy’ malware that executes cyberespionage actions.
Bouncing Golf Malware Marketing campaign Targets Android
Researchers from TrendMicro have unveiled an ongoing malware marketing campaign focusing on Android customers. The Bouncing Golf marketing campaign is presently focusing on ME international locations for cyberespionage functions. The marketing campaign includes infecting the gadgets with ‘GolfSpy’ malware that pilfers information from the goal machine and spy on customers’ actions.
As elaborated by TrendMicro of their blog post, malware marketing campaign works by maliciously repackaging identified apps. These apps usually are not out there on the Google Play Retailer or some other marketplaces. Reasonably the marketing campaign markets these apps individually on social media by selling the web site internet hosting the apps.
Upon reaching the customers’ machine, the apps ship malware “AndroidOS_GolfSpy.HRX” that bears cyberespionage capabilities. The malware then collects info from the machine and sends it to a C&C server in encrypted type. Furthermore, the malware additionally receives instructions from a distant server to execute additional actions.
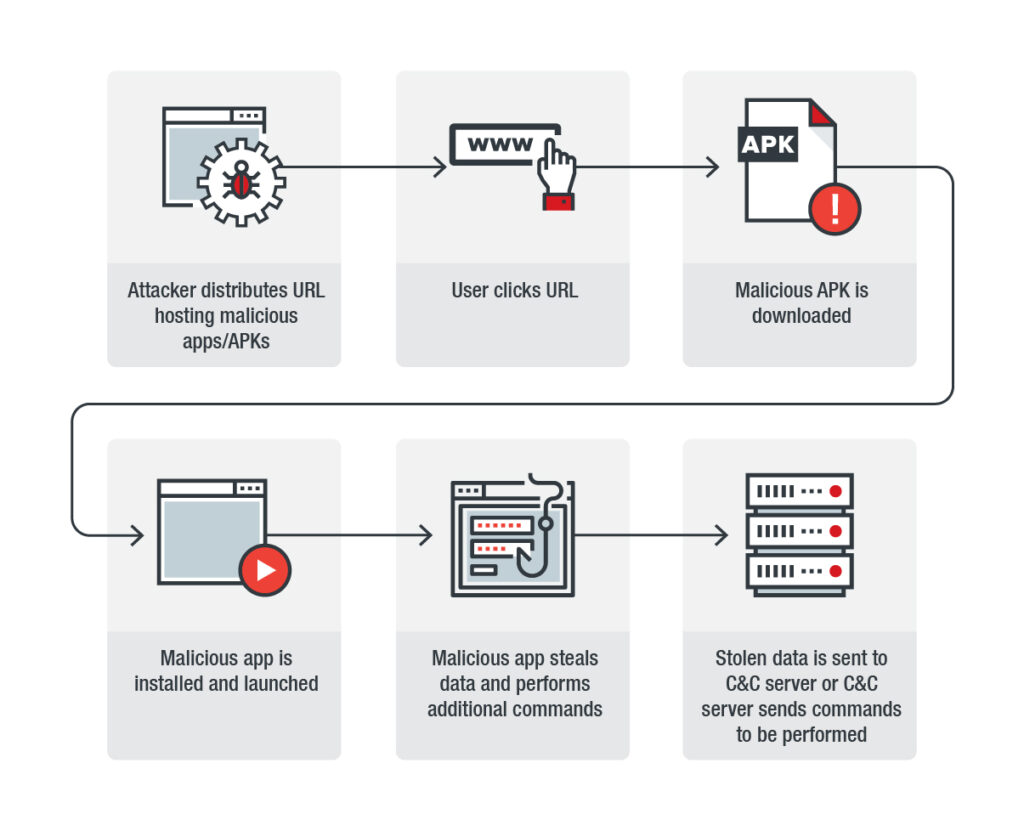
Describing the working of GolfSpy, the weblog said,
After it’s launched, GolfSpy will generate a novel ID for the affected machine after which gather its information reminiscent of SMS, contact record, location, and accounts on this format: “%,[],time”. The data is written right into a file on the machine. The attacker can select the information sorts to gather, that are written in a sure format.
In addition to amassing info, the malware additionally spies on person actions by monitoring and recording telephone calls. It additionally takes customers’ photographs by means of the entrance digital camera each time the person wakes the machine.
Resemblance With ‘Home Kitten’ Marketing campaign
Bouncing Golf malware marketing campaign has repackaged apps numerous well-liked apps to contaminate the gadgets. TrendMicro discovered as many as 660 gadgets contaminated with GolfSpy. The marketing campaign appeared predominantly energetic within the Center East, and it primarily pilfered military-related info from the gadgets.
Tracing again the observe of Bouncing Golf was a bit troublesome. In accordance with TrendMicro, the attackers have masked their C&C registrant info. Furthermore, the C&C server IP addresses additionally linked to various areas, together with Russia, Holland, Germany, and France.
Nonetheless, the best way Bouncing Golf repackages apps, the selection of apps, and the code strings of their decoding algorithm resemble with Domestic Kitten adware marketing campaign.
As said within the weblog,
The Android malware that each deploy share the identical strings of code for his or her decoding algorithm. The info that Home Kitten steals follows the same format with Bouncing Golf’s, with every kind of knowledge having a novel figuring out character. It’s additionally price noting that each campaigns repackage apps which are generally used of their goal’s international locations, reminiscent of Telegram, Kik, and Plus messaging apps.
Whereas the marketing campaign presently appears targeted on ME international locations solely, the researchers count on it to extend and diversify its distribution.
Tell us your ideas within the feedback.

