Safety researchers have found a uncommon piece of Linux spy ware that is presently totally undetected throughout all main antivirus safety software program merchandise, and consists of not often seen functionalities close to most Linux malware, The Hacker Information realized.
It is a identified undeniable fact that there are a only a few strains of Linux malware exist within the wild as in comparison with Home windows viruses due to its core structure and likewise as a result of its low market share, and likewise lots of them do not even have a variety of functionalities.
In recent times, even after the disclosure of extreme crucial vulnerabilities in varied flavors of Linux working methods and software program, cybercriminals didn’t leverage most of them of their assaults.
As an alternative, a lot of malware focusing on Linux ecosystem is primarily centered on cryptocurrency mining attacks for monetary acquire and creating DDoS botnets by hijacking susceptible servers.
Nevertheless, researchers at safety agency Intezer Labs just lately found a brand new Linux backdoor implant that seems to be beneath growth and testing section however already consists of a number of malicious modules to spy on Linux desktop customers.
EvilGnome: New Linux Spy ware
Dubbed EvilGnome, the malware has been designed to take desktop screenshots, steal recordsdata, seize audio recording from the person’s microphone in addition to obtain and execute additional second-stage malicious modules.
In keeping with a brand new report Intezer Labs shared with The Hacker News previous to its launch, the pattern of EvilGnome it found on VirusTotal additionally accommodates an unfinished keylogger performance, which signifies that it was uploaded on-line mistakenly by its developer.
EvilGnome malware masquerades itself as a legit GNOME extension, a program that lets Linux customers lengthen the performance of their desktops.
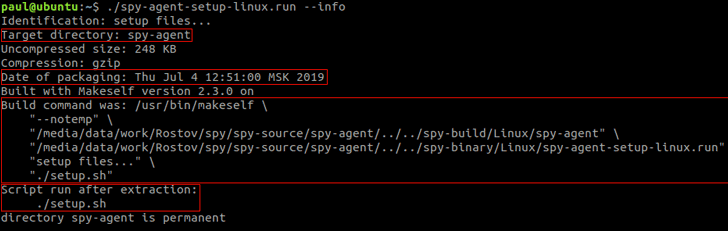
In keeping with the researchers, the implant is delivered within the type of a self-extracting archive shell script created with ‘makeself,’ a small shell script that generates a self-extractable compressed tar archive from a listing.
The Linux implant additionally good points persistence on a focused system utilizing crontab, just like home windows job scheduler, and sends stolen person knowledge to a distant attacker-controlled server.
“Persistence is achieved by registering gnome-shell-ext.sh to run each minute in crontab. Lastly, the script executes gnome-shell-ext.sh, which in flip launches the principle executable gnome-shell-ext,” the researchers stated.
EvilGnome’s Spy ware Modules
The Spy Agent of EvilGnome accommodates 5 malicious modules referred to as “Shooters,” as defined under:
- ShooterSound — this module makes use of PulseAudio to seize audio from the person’s microphone and uploads the information to the operator’s command-and-control server.
- ShooterImage — this module makes use of the Cairo open supply library to captures screenshots and uploads them to the C&C server. It does so by opening a connection to the XOrg Show Server, which is the backend to the Gnome desktop.
- ShooterFile — this module makes use of a filter checklist to scan the file system for newly created recordsdata and uploads them to the C&C server.
- ShooterPing — the module receives new instructions from the C&C server, like obtain and execute new recordsdata, set new filters for file scanning, obtain and set new runtime configuration, exfiltrate saved output to the C&C server, and cease any shooter module from working.
- ShooterKey — this module is unimplemented and unused, which most certainly is an unfinished keylogging module.
Notably, all of the above modules encrypt their output knowledge and decrypt instructions acquired from the C&C server with RC5 key “sdg62_AS.sa$die3,” utilizing a modified model of a Russian open supply library.
Potential Connection b/w EvilGnome and Gamaredon Hacking Group
Moreover, the researchers additionally discovered connections between EvilGnome and Gamaredon Group, an alleged Russian menace group that has been active since at least 2013 and has focused people working with the Ukrainian authorities.
Right here under, I’ve briefed a number of the similarities between EvilGnome and Gamaredon Group:
- EvilGnome makes use of a internet hosting supplier that has been utilized by Gamaredon Group for years and continues for use by it.
- EvilGnome additionally discovered to be working on an IP handle that was managed by the Gamaredon group two months in the past.
- EvilGnome attackers are additionally utilizing ‘.area’ TTLD for his or her domains, simply because the Gamaredon Group.
- EvilGnome employs methods and modules—like the usage of SFX, persistence with job scheduler, and the deployment of information-stealing instruments—that remind of Gamaredon Group’s Home windows instruments.
Learn how to Detect EvilGnome Malware?
To test in case your Linux system is contaminated with the EvilGnome spy ware, you’ll be able to search for the “gnome-shell-ext” executable within the “~/.cache/gnome-software/gnome-shell-extensions” listing.
“We imagine this can be a untimely take a look at model. We anticipate newer variations to be found and reviewed sooner or later, which might doubtlessly shed extra gentle into the group’s operations,” researchers conclude.
Since safety and antivirus merchandise are presently failing to detect the EvilGnome malware, researchers advocate involved Linux directors to dam the Command & Management IP addresses listed within the IOC part of Intezer’s weblog put up.