The innovativeness of hackers seems to have no end. Once again, they have worked out a means to evade security mechanisms to execute their phishing campaigns. This time, the attack exploits WeTransfer alerts to bypass email gateways.
WeTransfer Alerts Phishing Campaign
Researchers from Cofense have spotted another phishing campaign going on in the wild. This campaign exploits WeTransfer alerts to evade security measures.
As explained in their blog post, the scammers abuse the WeTransfer file hosting service to bypass email gateways.
The attack begins with emails reaching the victim’s mailbox made up as a WeTransfer notification for file sharing. The attackers seemingly use compromised email accounts for sending these phishing emails since these emails contain legit URLs to the WeTransfer service.
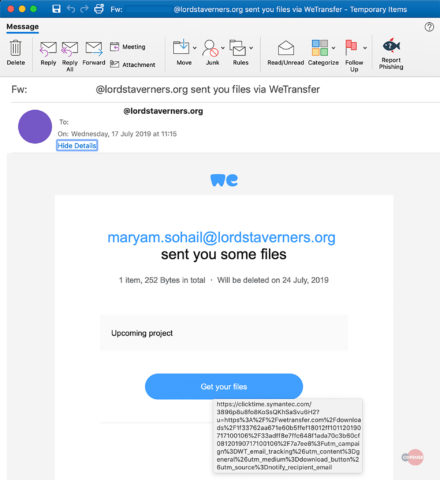
Clicking on these links redirects the victims to WeTransfer file-sharing webpages. These pages contain HTML or HTML files ready for download. Clicking on the files then redirect the user to the actual phishing sites.
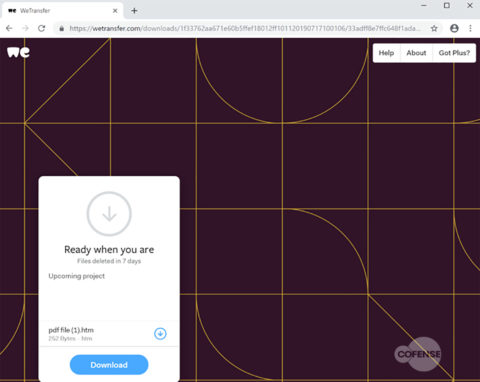
Like any other phishing scam, this one too, upon reaching the last phase, requires the users to enter their Office 365 account credentials.
Evasion Of Email Gateways
Because of the presence of trusted WeTransfer links, these phishing emails usually succeed in evading most security checks. According to the researchers,
These links will typically bypass gateways as benign emails, unless settings are modified to restrict access to such file sharing sites… These include ProofPoint, Office365 Safe Links, and Symantec.
Owing to this evasion strategy, despite being obvious, this phishing scam is likely to fool some users.
Earlier, the same researchers also highlighted another phishing campaign that tends to bypass security checks. In that case, the researchers evaded all defense measures by using QR codes.
Considering the growing number of such phishing attacks, each with a new strategy, it is imperative for users to “think twice” before clicking on any email they receive.
Stay safe!

