Yet one more phishing rip-off has caught the eye of the researchers. Once more, researchers have caught an e-mail phishing marketing campaign that tips customers by way of faux payments. Nevertheless, this one is exclusive in that it abuses SHTML File attachments within the emails.
Phishing Assault Exploiting SHTML File Attachments
Researchers at Mimecast have come throughout one other phishing marketing campaign bluffing customers. This time, the assault displays barely totally different conduct. Particularly, it makes use of SHTML file attachments in emails to trick customers.
As said of their blog post, using SHTML recordsdata is bizarre in that these recordsdata are predominantly associated to net servers. The assault begins within the normal manner – sending phishing emails to the victims. These emails seem as a receipt for some invoice funds, viewing which requires the customers to click on on the attachment.
Right here’s how the emails appear to be.
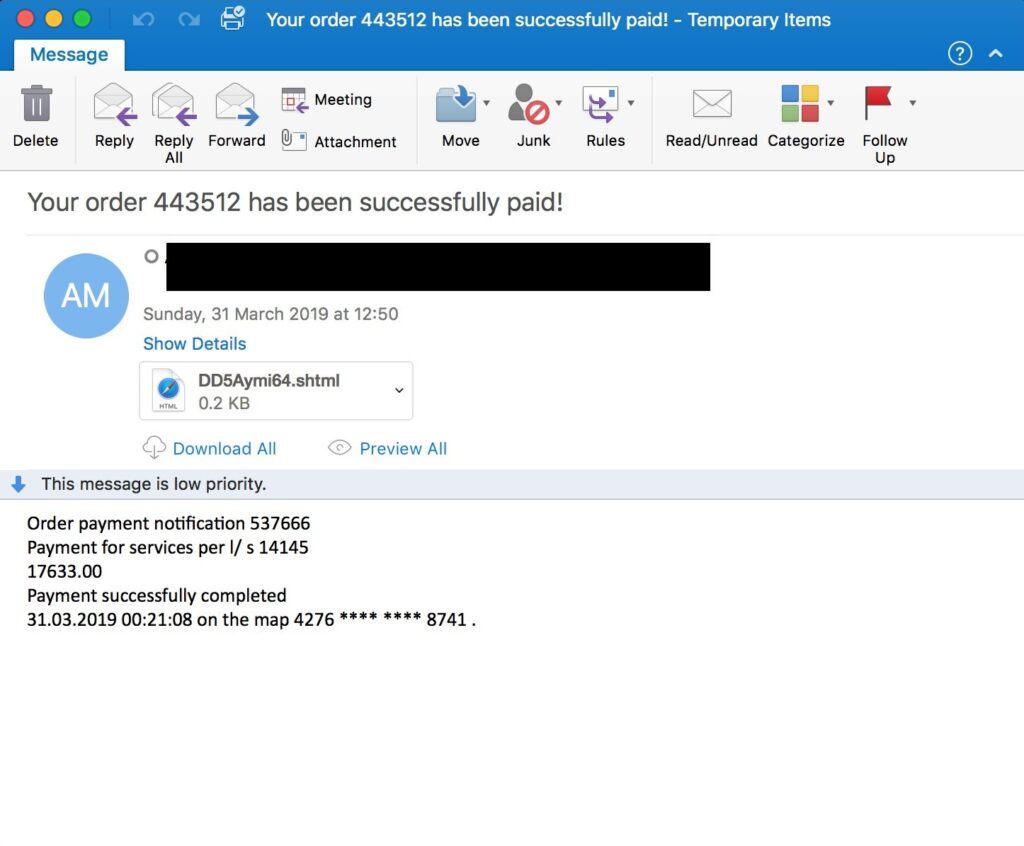
Upon clicking the attachment, the sufferer reaches the precise phishing website asking for data. A more in-depth inspection of the attachment reveals that these attachments assist emails evade URL evaluation by antimalware instruments. (We beforehand reported the same phishing rip-off evading safety measures by masking the URLs in QR codes.)
These SHTML recordsdata include JavaScript code masking the precise URL.
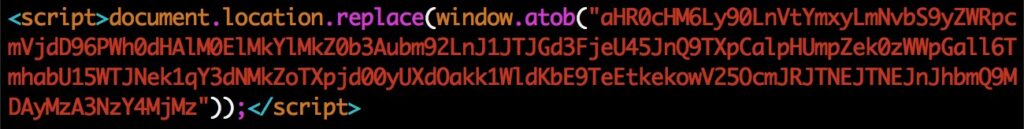
The second a person clicks on the attachment, they’re redirected to the phishing website, the place they need to supposedly enter the required delicate particulars.
Pricey UK Customers, Keep Cautious!
In response to the researchers, this phishing assault appears to originate from the UK. Ultimately, a serious a part of this marketing campaign resides within the UK, adopted by Australia and South Africa.
General, 55% of this marketing campaign was distributed within the UK, 31% in Australia, 11% in South Africa and three% elsewhere.
In South Africa and the UK, the prime targets appear to be the accounting and finance sectors. Whereas, in Australia, the assault appears focused in direction of the training sector.
Nonetheless, this doesn’t imply that the opposite customers ought to ignore such phishing campaigns. As all the time, everybody ought to stay vigilant whereas coping with emails, and opening attachments, each at a person and enterprise degree.

