It hasn’t been lengthy since we studied how Android apps evade app permissions to exfiltrate person information. As soon as once more, researchers have carried out one other research to disclose how Android apps hearken to customers’ dialog over loudspeakers. Dubbed ‘Spearphone’ the assault empowers perpetrators to seize all voice generated by means of a tool’s loudspeaker.
Spearphone Assault Breaching Speech Privateness
Researchers have demonstrated a brand new side-channel assault ‘Spearphone’ that permits capturing loudspeaker information. The Spearphone assault breaches speech privateness by exploiting the movement sensor ‘accelerometer’ and capturing speech reverberations generated by means of the loudspeaker. This, in flip, empowers the attackers to hear to each sound popping out of the loudspeaker together with conversations, music, or another audio.
As elaborated of their research paper, this vulnerability exists in most Android smartphones at present in use. The customers turn into weak to assaults as quickly as they put their telephones to loudspeaker mode when enjoying any audio recordsdata, throughout cellphone calls, or interacting with voice assistants.
Describing the Spearphone assault, the researchers acknowledged,
Spearphone is a three-pronged assault that performs gender, speaker and speech classification utilizing accelerometer’s response to the speech reverberations, generated by the sufferer’s cellphone’s audio system.
In line with this research, the flaw exists owing to the location of accelerometer and loudspeaker on the identical floor inside a smartphone.
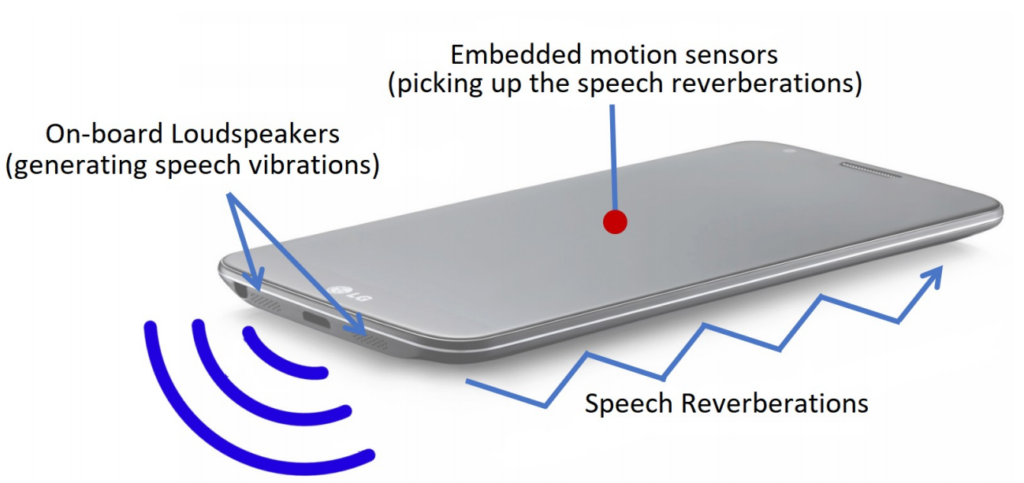
Because the accelerometer can sense the sound reverberations at sure loudness, it may possibly seize the voice generated from the loudspeaker. Thus, an attacker can exploit this glitch by way of a malicious utility that may abuse accelerometer to seize loudspeaker sounds.
Demonstration of Assault on Android Telephones
As a PoC, the researchers designed an Android app with malicious intent to seize accelerometer readings. Additionally they elaborate that the identical assault may also make use of a malicious Javascript operating on the goal cellphone’s browser.
For check gadgets, they took LG G3, Samsung Galaxy S6 and Samsung Be aware 4. Whereas, they carried out the experiment into two completely different setups for exact outcomes – handheld setup and floor setup (gadget positioned on a hardwood prime).
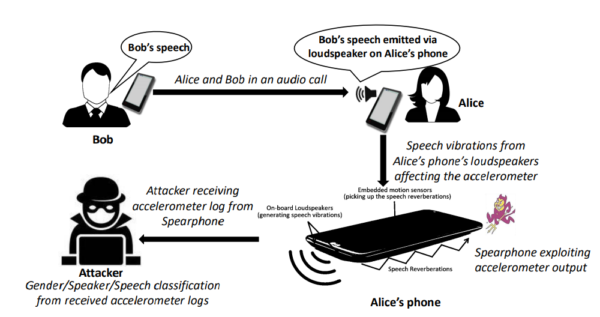
Right here is how the researchers have illustrated the assault state of affairs in case of a cellphone name.
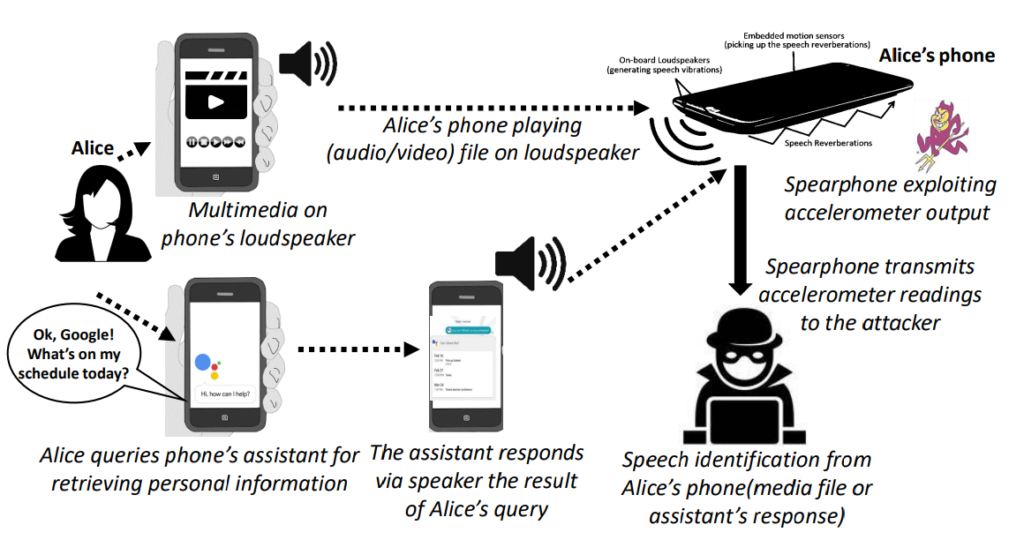
And, in case of media playback or interplay with voice assistants.
The researchers primarily carried out this research on Android telephones owing to their dominant market share and the convenience of entry by functions to a movement sensor. Nevertheless the movement sensor ‘accelerometer’ was discovered to be extra receptive to Spearphone assault than ‘gyroscope’.
Although, their research had some limitations that they’ve acknowledged of their paper. This doesn’t alleviate the hazards related to this assault.
The researchers have suggested implementing strict utilization permission coverage for Android apps as a potential mitigation. Furthermore, customers also needs to stay cautious when permitting apps to entry movement sensors on their gadgets. In addition to, utilizing vibration dampening materials across the built-in loudspeakers on the gadget can also assist mitigate the assault.
This isn’t the primary time {that a} research has demonstrated the vulnerability of movement sensors. Earlier, researchers have demonstrated a sensor calibration attack involving movement sensors to trace customers’ on-line actions.
Tell us your ideas within the feedback.

