Whereas utilizing encrypted messaging apps, some customers might imagine their conversations and media recordsdata exchanged in the course of the chats remained end-to-end-encrypted. Nonetheless, researchers have just lately made a opposite discovering. As found, a media file jacking vulnerability threatens the safety of most Android apps, together with WhatsApp and Telegram.
Media File Jacking Vulnerability
Researchers from Symantec have shared an in depth report concerning a media file jacking flaw threatening Android apps. In line with their findings, hackers can simply manipulate media recordsdata transferred over WhatsApp, Telegram, and different functions. Neither the sender nor the receiving consumer would ever discover this manipulation. The assault does nevertheless solely work underneath sure circumstances.
Speaking concerning the exploit of their blog post, Symantec researchers elaborated that hackers can manipulate incoming recordsdata on an contaminated machine even earlier than the recipient consumer truly sees them. That is attainable due to a sure time-lapse in the course of the writing of media recordsdata on the disk and the next UI immediate.
It stems from the lapse in time between when media recordsdata obtained by means of the apps are written to the disk, and when they’re loaded within the apps’ chat consumer interface (UI) for customers to devour. This crucial time lapse presents a chance for malicious actors to intervene and manipulate media recordsdata with out the consumer’s information.
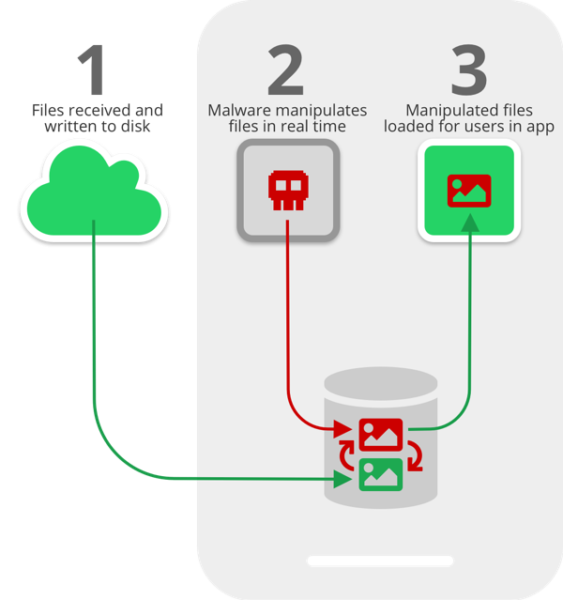
The execution of the assault primarily depends on the form of storage reminiscence. Whereas the machine’s inside storage permits app-restricted entry solely, the exterior storage clearly permits all apps to entry. It means the identical exterior storage can be open to entry by a malicious app as nicely. Therefore, if the customers select to retailer recordsdata on the exterior storage, the recordsdata turn out to be susceptible to media file jacking assault. It applies even to WhatsApp and Telegram media recordsdata.
Attainable Assault Eventualities:
The researchers demonstrated the next three completely different attainable conditions of media file manipulation.
- Picture manipulation: A malicious app on the recipient machine can manipulate the incoming picture file (together with the thumbnail preview) in real-time.
- Fee manipulation: Hackers can manipulate the billing particulars in fee invoices tricking the victims to make incorrect funds. This manipulation can be attainable with PDF recordsdata.
- Audio file manipulation: An attacker can meddle with the incoming audio file utilizing deep studying know-how, changing the unique message with a faux one – that too – within the unique voice of the audio.
Furthermore, the researchers worry that such assaults may contribute to spreading faux information. This will even goal Telegram information channels, affecting the credibility of the channel and concentrating on the receivers with faux information.
Attainable Mitigations
To the media file jacking vulnerability, WhatsApp customers are extra susceptible for the reason that app has the choice of storing media to machine’s gallery by default. Whereas, within the case of Telegram, it’s an elective function requiring handbook activation by a consumer.
In both case, the simplest means for normal Android customers to mitigate this assault is to cease utilizing exterior storage.Within the case of Telegram, they need to not select Gallery to retailer media recordsdata.To deactivate this feature, go to Settings -> Chat Settings -> Save to Gallery.
Whereas, in case of WhatsApp, they need to flip this feature off by way of Settings -> Chats -> Media Visibility.
As for extra promising options, the researchers advise builders to undertake the next measures.
- Storing a hash worth in a file’s metadata to validate its integrity previous to writing it to the disk.
- Utilizing private listing or inside storage for saving media recordsdata.
- Introduce options to encrypt delicate recordsdata.
In 2018, Verify Level Analysis additionally reported a couple of comparable flaw that they referred to as Man-in-the-Disk attack. The MiTD assault was additionally attainable due to the apps’ entry to the machine’s exterior storage.

