Another phishing campaign is active in the wild which targets users with TrickBot malware. This phishing campaign succeeds in delivering TrickBot as it evades secure email gateways by exploiting Google Docs.
Phishing Campaign Delivering TrickBot Malware
Researchers from Cofense have discovered another scary phishing campaign. This time, the phishing attack is more of a malware campaign delivering TrickBot. The phishing emails also manage to bypass any security checks or email gateways as they exploit legit Google Docs links.
As stated in their blog post, the attack begins by sending a malicious email to a user, like any other phishing attack. The email body contains an embedded URL behind an ‘Open in Docs’ button. To lure the user to click on this button, the email content hints of a previously sent document.
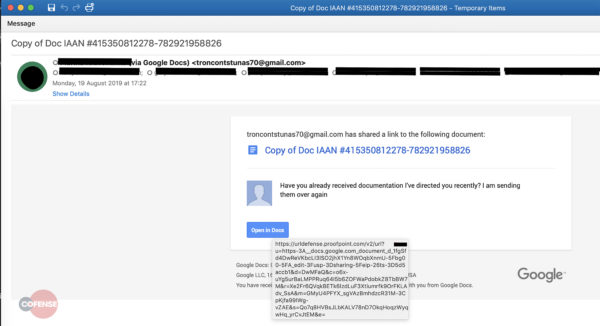
Clicking on this button (to open the supposed document) redirects the user to a link showing fake 404 error. This error then tricks the user to click on another link to download the document.
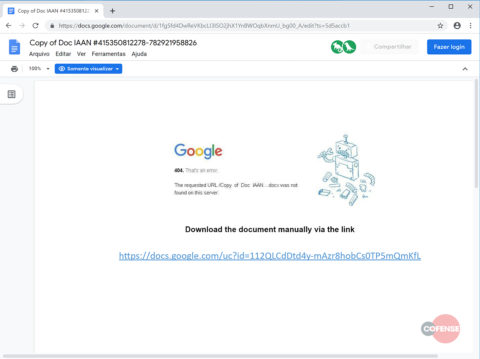
This is the actual malicious link which, when clicked, downloads the malware to the target device. However, it is difficult for the victim to identify this malware as it mimics a PDF file. However, if the user has enabled viewing file extensions on the device, he or she can spot the ‘.exe’ extension present with this PDF.
Malware Execution
After the user downloads the malicious file disguised as PDF, the payload executes. It then copies itself in the “C:ProgramData” folder to execute the malware. Besides, it also creates a copy in the “C:UsersREMAppDataRoamingspeedLan” location where the TrickBot config file is also present.
In addition, the malware also ensures repeat activities every 11 minutes for 414 days by setting up a task in Task Scheduler. Regarding this action, the researchers stated,
The scheduled task checks to see if the binary is running in memory every 11 minutes over a 1-year period. This means that the binary will stay persistent on the system if the process is terminated.
Then it carries on executing numerous times with Svchost that is responsible for various TrickBot modules.
This phishing campaign simply adds to the count on TrickBot appearances. In July, the malware emerged as a campaign targeting users via fake Office 365 sites.

