Today we report about further prey of the notorious MageCart attack. This time the victims turn out to be the online fashion store Sixth June, and the shopping site for the American Cancer Society. Reportedly, two separate researchers have found the Sixth June website and the Cancer.org shop site under MageCart attack. Ironically, despite receiving the alerts from the researchers, both the victims have paid no attention to the matter yet.
Two More Victims Of MageCart Attack
The security researcher with alias Jenkins on Twitter has discovered another website bearing the notorious payment skimmer MageCart. The researcher precisely found the website of fashion store Sixth June under the MageCart attack.
He shared his findings via one of his recent tweets.
Alongside Sixth June, another researcher has discovered a different website under the MageCart attack. In brief, the researcher Willem de Groot found the e-store of American Cancer Society bearing the malicious code. He disclosed these findings publicly via a separate blog post.
As stated by de Groot,
The Cancer.org skimmer loader hides itself by hiding behind the (legitimate) GoogleTagManager code. It searches for “checkout” (Y2hlY2tvdXQ=) and will then load the actual skimming code from thatispersonal.com/assets/cancer.js (copy).
Malicious E-Skimmer Continues To Exist…
Ironically, the two new victims, Sixth June and American Cancer Society shop, still remain under the MageCart attack. We could also verify the existence of the malicious code on both websites.
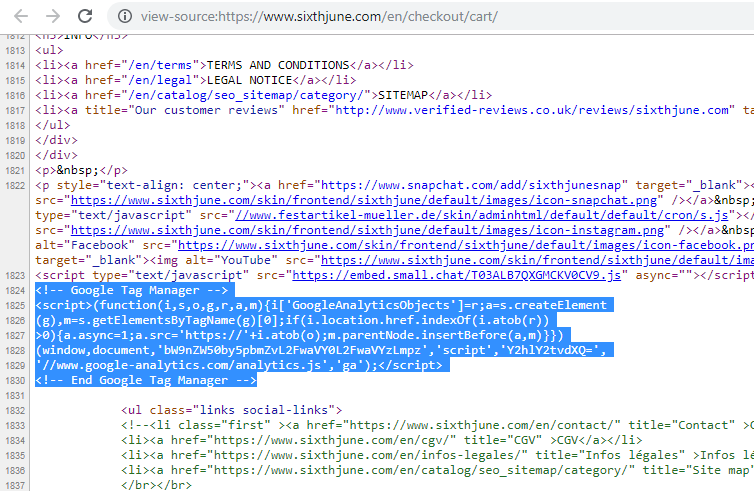
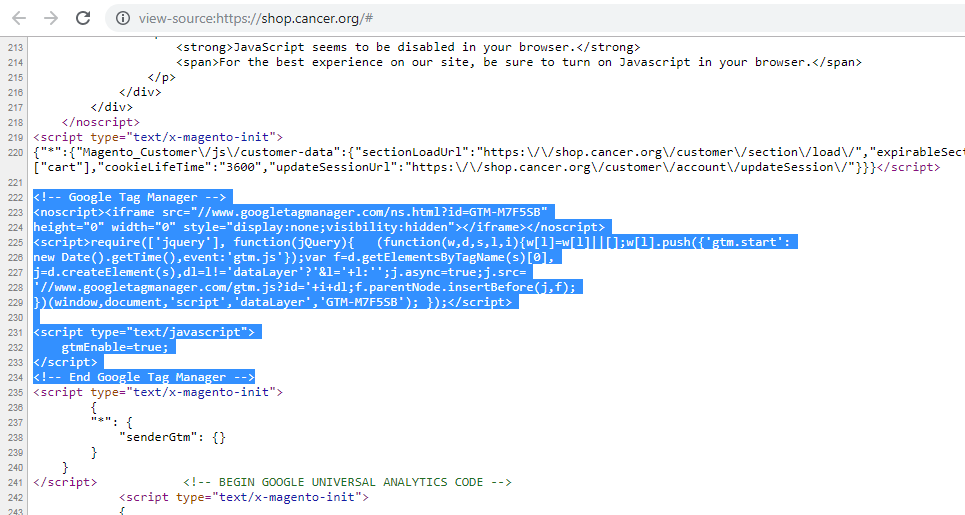
In both cases, the respective researchers have already notified the site authorities about the matter. Specifically, Jenkins notified Sixth June a week ago. Whereas, de Groot informed Cancer.org via their fraud hotline. Nonetheless, both the websites continue to bear the codes hinting toward no significant action having been taken.
On the other hand, customers who have collaborated with either of these websites, particularly those who made any purchases, should rest assured about having their card details lost to the hackers. Therefore, all those who have collaborated with these sites during the past few days (or a week), must contact their bank authorities to save potential losses.

