Researchers have discovered another serious vulnerability affecting Android phones. Dubbed as StrandHogg, the vulnerability even affects the latest devices running on Android 10. Exploiting the flaw allows an attacker to steal banking logins. Additionally, attackers are actively exploiting the bug already.
Android StrandHogg Vulnerability
Researchers from Norwegian security firm Promon have discovered a security flaw affecting Android devices. What they called StrandHogg, the vulnerability allows attackers to gain complete control of the target device without root.
Elaborating on their findings in a dedicated article, the researchers mention that StrandHogg even affects the latest Android 10.
The vulnerability caught the attention of the researchers after one of their clients informed them of a wave of bank fraud. They even supplied Promon with sample malware, investigating further allowed Promon to discover the vulnerability.
Digging further on the matter revealed that the vulnerability allows attackers to target Android devices via malicious apps. As stated in their post,
This exploit is based on an Android control setting called ‘taskAffinity’ which allows any app – including malicious ones – to freely assume any identity in the multitasking system they desire.
In brief, an attacker can exploit the bug to harvest device access permissions by masking a malicious app as a legit one.
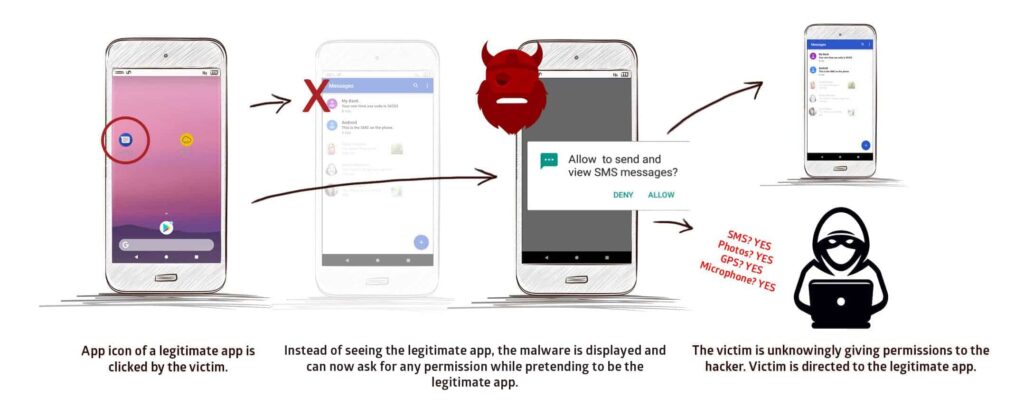
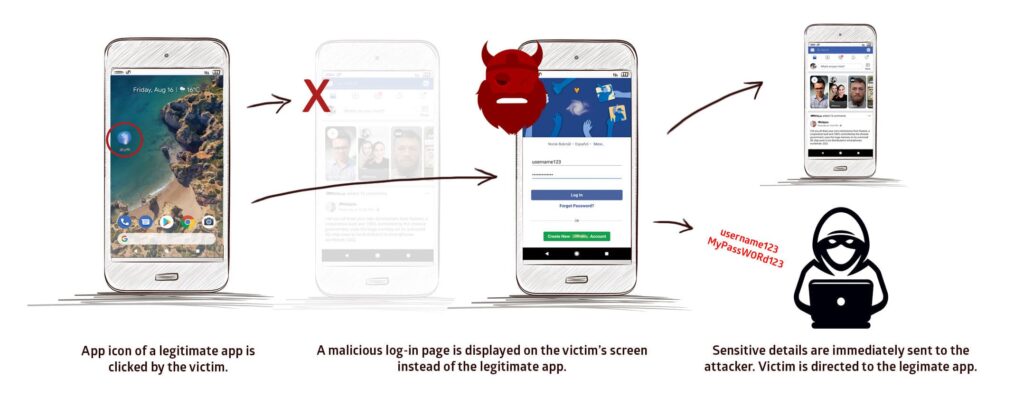
Likewise, attackers can also exploit this bug for phishing attacks by creating fake login pages of otherwise legit apps. These attacks threaten the integrity of users’ social media as well as online banking credentials.
The researchers have also shared the following video briefly demonstrating the exploit:
Active Exploitation Through Malicious Apps
Although, Promon explained that the malware they analyzed resided outside the Play Store. However there are malicious apps on the Play Store that can be used to download this malware through malware droppers.
Though Google has removed these malicious apps, the threat is still present. Researchers have already established how various malicious apps evade Google’s security for Play Store. Cybercriminals may still publish malware droppers on the Play Store and may continue to exploit the flaw.
According to Promon, around 500 of the most popular apps are still vulnerable to StrandHogg. Moreover, the researchers also highlight the active exploitation of the bug. According to Tom Lysemose Hansen, CTO Promon,
We have tangible proof that attackers are exploiting StrandHogg in order to steal confidential information. The potential impact of this could be unprecedented in terms of scale and the amount of damage caused because most apps are vulnerable by default and all Android versions are affected.
Since the vulnerability remains unpatched, users should remain vigilant while downloading apps from the Play Store. Likewise, Gustaf Sahlman, CEO Promon, also urges companies to apply robust security for their applications.
Let us know your thoughts in the comments.

