A serious vulnerability existed in Microsoft Teams that allowed account hijacking. Simply sending a malicious GIF to the victim could allow an adversary to take over the target account.
Microsoft Teams Account Hijacking via GIF
Researchers from CyberArk have discovered a serious account hijacking vulnerability in Microsoft Teams. Exploiting the bug allowed an attacker to stealthily takeover target accounts using a malicious GIF.
As stated in their blog post, the problem existed because of how Microsoft Teams generates access tokens. Briefly, Microsoft Teams client creates numerous access tokens for different purposes other than login. These include tokens for sharing images as well as one called ‘Skype Token’.
The Teams client uses one of these created tokens to allow a user to see images shared with them or by them, as those images are stored on Microsoft’s servers, which applies authorization control. This token, called “skype token,” can also be seen as a cookie named “skypetoken_asm.”
While user authentication for images may be a tedious process, Microsoft implements two cookies “authtoken” and “skypetoken_asm” for quick loading. The client stores the Skype Token to teams.microsoft.com and subdomains, including two vulnerable subdomains aadsync-test.teams.microsoft.com and data-dev.teams.microsoft.com.
If an adversary hijacks a vulnerable subdomain, They could then access the authtoken required to generate the skype token needed for authentication, simply by sending a malicious .GIF file. As stated by the researchers,
We considered this approach as well, sending an image to our victim with an “src” attribute set to the compromised sub-domain via Teams chat. When the victim opens this message, the victim’s browser will try to load the image and this will send the authtoken cookie to the compromised sub-domain.
The attacker could scrape the victim’s data stealthily. Moreover, an attacker could also exploit this bug to target enterprise accounts due to the wormable nature of the exploit.
This attack works for Microsoft Teams for desktop and web browser. The following image illustrates the attack scenario. Besides, the researchers have also shared the PoC in a demonstration video.
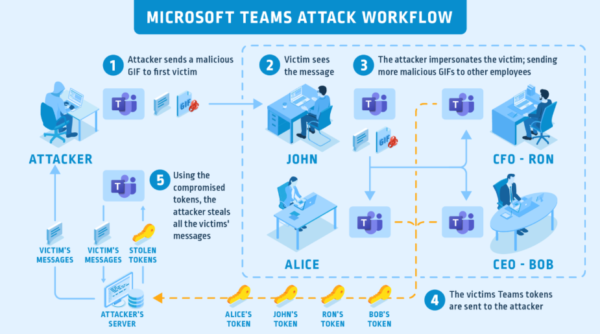
Microsoft Patched The Vulnerability
After discovering the flaw, the researchers reached out to Microsoft in March 2020 to inform them of the flaw. Following their report, Microsoft remedied the vulnerability by deleting the misconfigured DNS records of the two vulnerable subdomains. Microsoft also released patches in April 2020 to prevent similar bugs in the future.
Let us know your thoughts in the comments.

