Astaroth Trojan that has been around for several years is now back with even more features. This time, Astaroth malware becomes sneakier as it abuses YouTube channel descriptions to hide its C&C servers.
Astaroth Malware Abuse YouTube Channel Description
Researchers from Cisco Talos Intelligence have presented a detailed analysis of the new Astaroth malware variant. As observed, Astaroth has reemerged with advanced features.
Briefly, the infostealing Trojan has now acquired two more functionalities. The first is the ability to evade security checks and sandbox environments. Hence, it tends to escapes any analyses by security researchers and virtual machines.
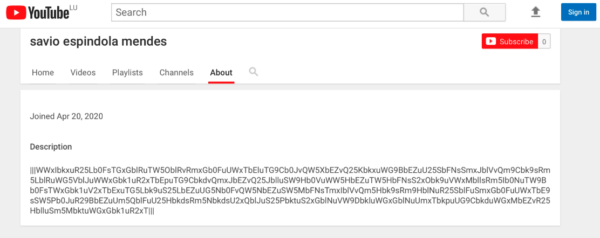
Secondly, the malware authors have established different YouTube channels, the description of which includes links to Astaroth C2 servers. Specifically, the “|||” delimiters in the description include the encrypted and base 64 encoded C&C domains.
Regarding the distribution, the malware reaches the target users via phishing emails. Once a user opens the malicious email and clicks on the given link, the executable reaches the target device.
However, it does not execute right away. Rather it is a multi-stage process during which the malware ensures to have reached the right target. If it detects a VM or a non-Brazilian user, the infection won’t continue.
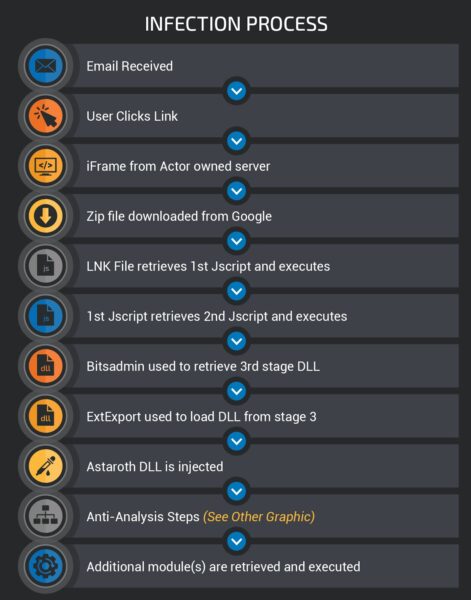
The following image depicts the stages of infection.
Malware Presently Active In Brazil
According to the researchers, the malware is actively targeting the users in Brazil. The malware distribution is taking place via phishing emails, which also includes COVID-19 themed campaigns.
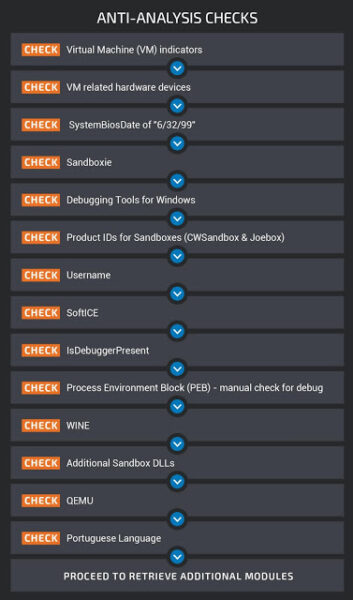
Besides, the malware authors have made sure to target the specific region leveraging the malware’s anti-sandbox checks. In fact, the location check happens at the same time when the malware checks for virtual machines and sandbox environments. Perhaps, it does so at the last stage when the malware looks for the Portuguese language (see image below).
However, the evasive and invasive nature of the Trojan hints that the threat actors may expand their target radius.
Even in the campaign discovered in early 2019, when Astaroth exploited antivirus tools, it targeted users in Brazil and Europe.
Let us know your thoughts in the comments.

