While numerous Android malware kesep emerging online every now and then, this malware stayed under the radar for years. Identified as Mandrake, the malware is precisely serving as a spying tool for hackers targeting Android users.
Mandrake Malware Targeting Android Users
Researchers from Bitdefender have shared a detailed white paper on their findings regarding the Mandrake Android malware. Reportedly, the malware dubbed Mandrake is active in the wild at least for the past 4 years. During all this time, the malware remained undetected only to be caught by Bitdefender in early 2020.
Briefly, the malware worked as smart spyware targeting users via phishing campaigns and fake apps. The researchers noticed at least two major infection waves – between 2016 and 2017, and then between 2018 and 2020. While the first wave involved a malware strain with reduced malicious functionalities, the second wave involved a smarter malware version.
The researchers found the malware available on Google Play Store disguising at least 7 apps, each bearing a wide userbase. These included OfficeScanner, Abfix, Currency XE Converter, SnapTune Vid, CoinCast, Horoskope, and Car News – all from seemingly different developers.
Apparently, the apps looked legit as the attackers were kind enough to take care of users’ feedback and issue fixes. They also established a legit online backing these apps with websites and social media pages.
Upon reaching the target device, the malware used to execute in a three-stage process. The third-stage would only execute if the attackers would find the victim worthy enough to target.
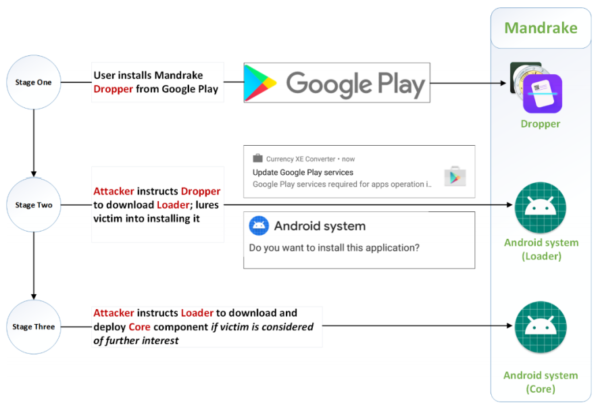
When executed, Mandrake runs stealthily on the victim’s device, exfiltrating data. It also exhibits numerous functionalities to take over the target device. These include,
- Extracting SMS messages
- Sending SMS to specified numbers
- Retrieving contact list
- Making phone calls
- Retrieving app list
- Installing/uninstalling apps
- Retrieving all account data
- Retrieve device and network details
- Screen recording
- GPS tracking
- Initiate factory reset to wipe malware
The last feature comes into action when the attackers find the exfiltrated data enough to steal. They would then quietly leave the device to stay undetected.
Malware Executes Targeted Attacks
Researchers found that this Android malware largely remained undetected for years due to its precise targeting of users. The campaign predominantly targeted users in developed regions, such as Europe, Australia, Canada, and America. Among these, Australia emerged as the most-hit region.
Whereas, the malware did not target users from low-income regions, such as Africa, Arab-speaking areas, and countries belonging to the former USSR. Specifically, the attackers have exempted about 90 countries from their hitlist.
Moreover, the malware also targeted users according to SIM cards. As stated in the white paper,
It also avoids running on devices with no SIM cards or with SIMs issued by specific operators. Most notably, it will not run with Verizon or China Mobile Communications Corporation (CMCC) operators, among others.
Furthermore, the malware would escape running on simulated environments by various tricks, such as CAPTCHA verifications on the app launch.
Despite all these details, the researchers couldn’t explain the origin of the attackers and their intent while targeting victims.
Nonetheless, the malware is still around with a high potential to expand its target radius. Hence, once again, the users must ensure to avoid using apps from new developers on unknown names.

