Cybersecurity researchers today uncovered a new advanced version of ComRAT backdoor, one of the earliest known backdoors used by the Turla APT group, that leverages Gmail’s web interface to covertly receive commands and exfiltrate sensitive data.
“ComRAT v4 was first seen in 2017 and known still to be in use as recently as January 2020,” cybersecurity firm ESET said in a report shared with The Hacker News. “We identified at least three targets: two Ministries of Foreign Affairs in Eastern Europe and a national parliament in the Caucasus region.”
Turla, also known as Snake, has been active for over a decade with a long history of the watering hole and spear-phishing campaigns against embassies and military organizations at least since 2004.
The group’s espionage platform started off as Agent.BTZ, in 2007, before it evolved to ComRAT, in addition to gaining additional capabilities to achieve persistence and to steal data from a local network.
It is now known that earlier versions of Agent.BTZ were responsible for infecting US military networks in the Middle East in 2008. In recent years, Turla is said to have been behind the compromise of French Armed Forces in 2018 and the Austrian Foreign Ministry early this year.
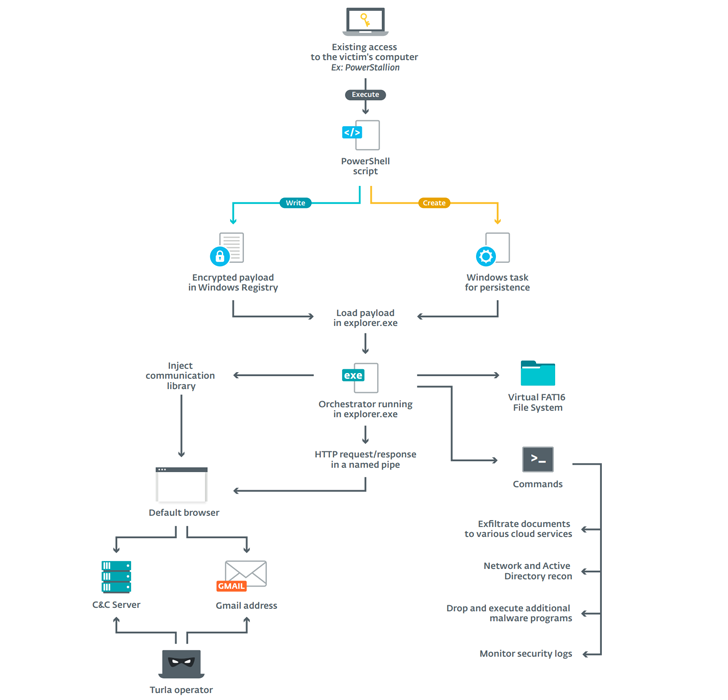
Newer versions of ComRAT backdoor have since ditched Agent. BTZ’s USB-stick infection mechanism in favor of injecting itself into every process of the infected machine and executing its primary payload in “explorer.exe.”
What’s New in ComRAT v4?
The ComRAT v4 (or “Chinch” by the malware authors), as the new successor is called, uses an entirely new code base and is far more complex than its earlier variants, according to ESET. The firm said the first known sample of the malware was detected in April 2017.
ComRAT is typically installed via PowerStallion, a lightweight PowerShell backdoor used by Turla to install other backdoors. In addition, the PowerShell loader injects a module called ComRAT orchestrator into the web browser, which employs two different channels — a legacy and an email mode — to receive commands from a C2 server and exfiltrate information to the operators.
“The main use of ComRAT is discovering, stealing, and exfiltrating confidential documents,” the researchers said. “In one case, its operators even deployed a .NET executable to interact with the victim’s central MS SQL Server database containing the organization’s documents.”
What’s more, all the files related to ComRAT, with the exception of the orchestrator DLL and the scheduled task for persistence, are stored in a virtual file system (VFS).
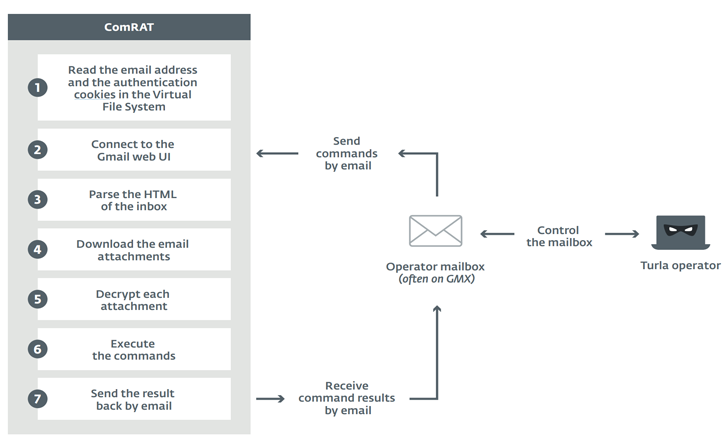
The “mail” mode works by reading the email address and the authentication cookies located in the VFS, connecting to the basic HTML view of Gmail, and parsing the inbox HTML page (using Gumbo HTML parser) to get the list of emails with subject lines that match those in a “subject.str” file in the VFS.
For each email that meets the above criteria, the comRAT proceeds by downloading the attachments (e.g. “document.docx,” “documents.xlsx”), and deleting the emails to avoid processing them a second time.
Despite the “.docx” and “.xlsx” format in the filenames, the attachments are not documents themselves, but rather encrypted blobs of data that include a specific command to be executed: read/write files, execute additional processes, and gather logs.
In the final stage, the results of the command execution are encrypted and stored in an attachment (with the double extension “.jpg.bfe”), which is then sent as an email to a target address specified in the “answer_addr.str” VFS file.
The “legacy” mode, on the other hand, makes use of the already existing C2 infrastructure (ComRAT v3.x) to issue remote commands, the results of which are compressed and transmitted to a cloud service such as Microsoft OneDrive or 4Shared.
The exfiltrated data comprises user details and security-related log files to check if their malware samples were detected during a scan of the infected systems.
Based on the Gmail email distribution patterns over a one-month period, ESET said the operators behind the campaign are working in the UTC+3 or UTC+4 time zones.
“Version four of ComRAT is a totally revamped malware family released in 2017,” ESET researcher Matthieu Faou said. “Its most interesting features are the Virtual File System in FAT16 format and the ability to use the Gmail web UI to receive commands and exfiltrate data. Thus, it is able to bypass some security controls because it doesn’t rely on any malicious domain.”