A U.S. federal government commission associated with international rights has been targeted by a backdoor that reportedly compromised its internal network in what the researchers described as a “classic APT-type operation.”
“This attack could have given total visibility of the network and complete control of a system and thus could be used as the first step in a multi-stage attack to penetrate this, or other networks more deeply,” Czech security company Avast said in a report published last week.
The name of the federal entity was not disclosed, but reports from Ars Technica and The Record tied it to the U.S. Commission on International Religious Freedom (USCIRF). Avast said it was making its findings public after unsuccessful attempts to directly notify the agency about the intrusion and through other channels put in place by the U.S. government.
At this stage, only “parts of the attack puzzle” have been uncovered, leaving the door open for a lot of unknowns with regards to the nature of the initial access vector used to breach the network, the sequence of post-exploitation actions taken by the actor, and the overall impact of the compromise itself.
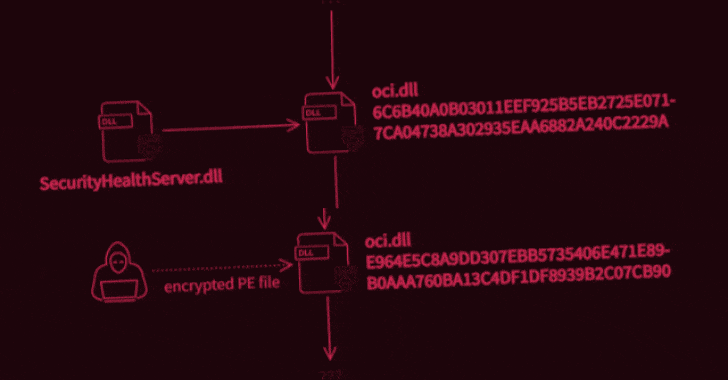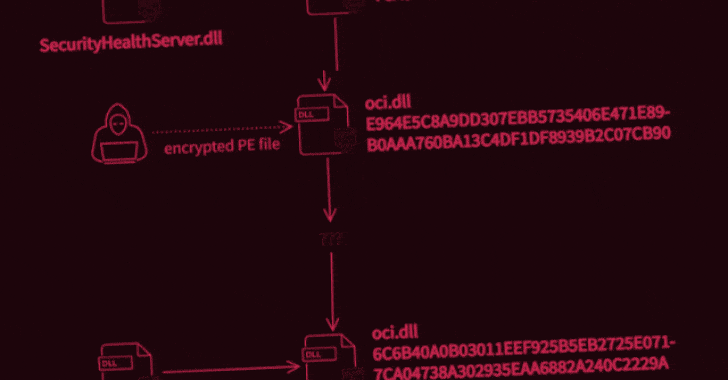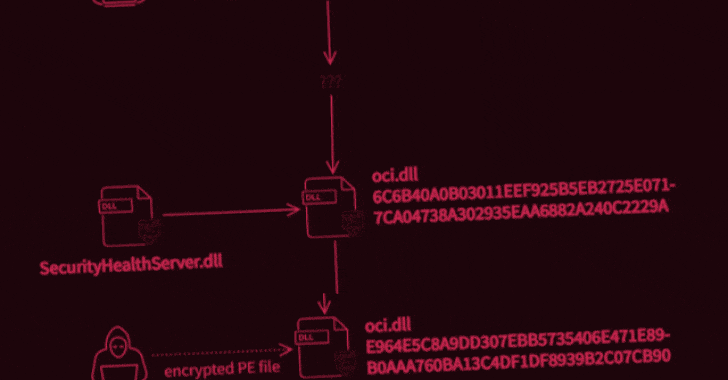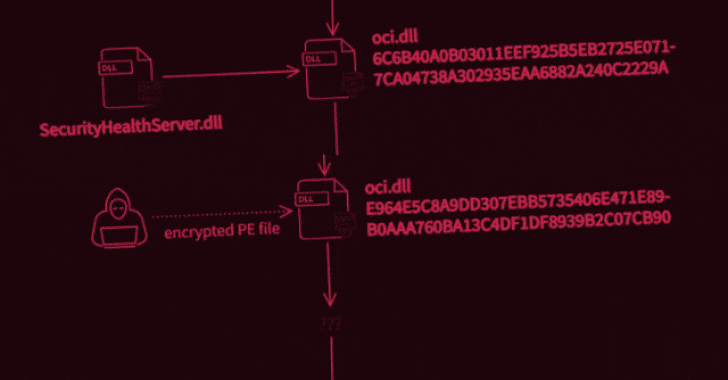
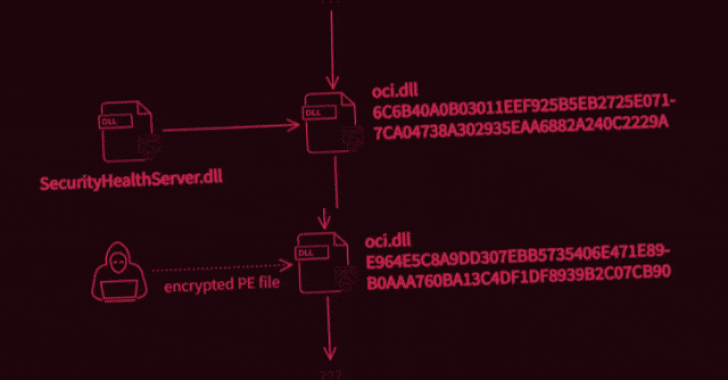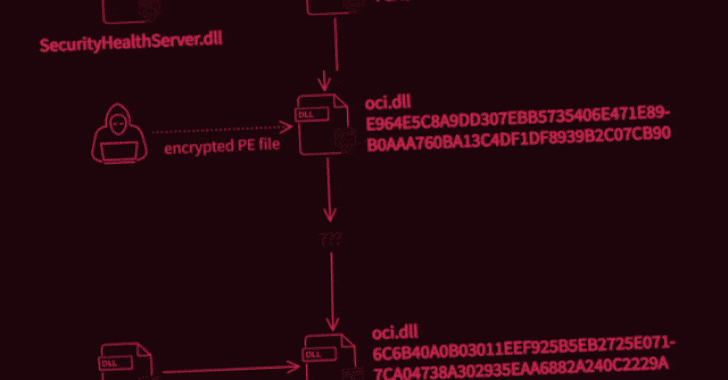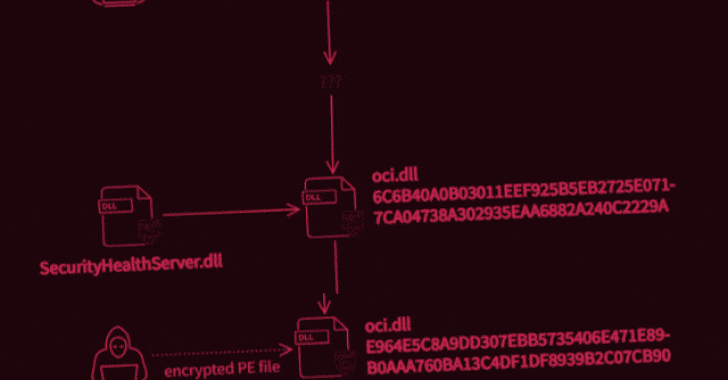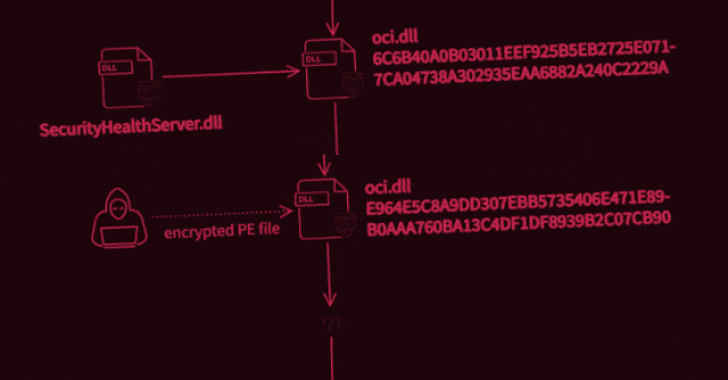
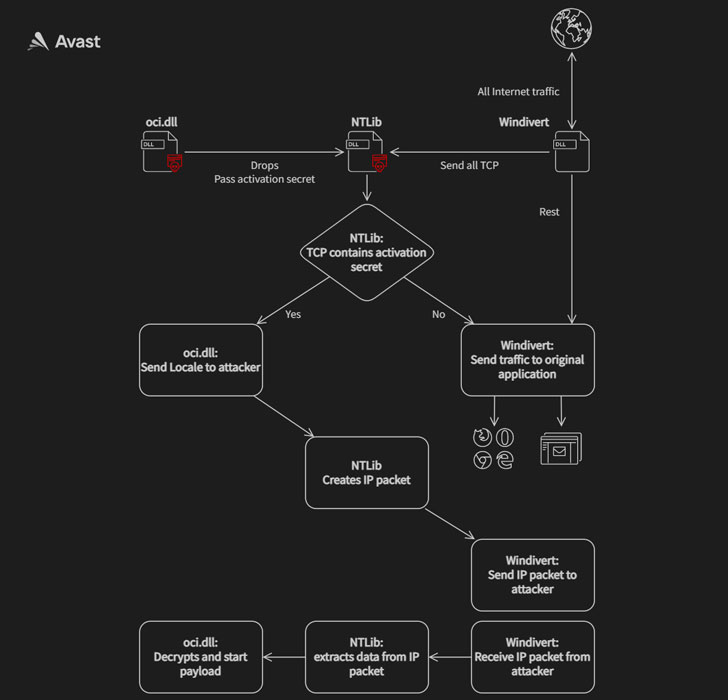
What’s known is that the attack was carried out in two stages to deploy two malicious binaries, the first of which potentially enabled the unidentified adversary to intercept internet traffic and execute code of their choosing, permitting the operators to take complete control over the infected systems. It achieves this by abusing WinDivert, a legitimate packet capturing utility for Windows.
Interestingly, not only both the samples masquerade as an Oracle library named “oci.dll,” the second-stage decryptor deployed during the attack was found to share similarities with another executable detailed by Trend Micro researchers in 2018, which delved into an information theft-driven supply chain attack dubbed “Operation Red Signature” aimed at organizations in South Korea. The overlaps have led the Avast Threat Intelligence Team to suspect that the attackers have had access to the source code of the latter.
“It is reasonable to presume that some form of data gathering and exfiltration of network traffic happened, but that is informed speculation,” the researchers said. “That said, we have no way to know for sure the size and scope of this attack beyond what we’ve seen.”