What is a Browser in the Browser attack
What’s up nerds! Mr.D0x has yet another attack vector mapped out for us. In early March an article was published here. It describes a new phishing attack called “Browser in the Browser” or BITB. This is a phishing attack that uses HTML and CSS to create a fake pop-up window within the browser that spoofs a login page such as windows, google etc. Below is a demo from Mr.D0x showing the difference between a phished login and a normal login.
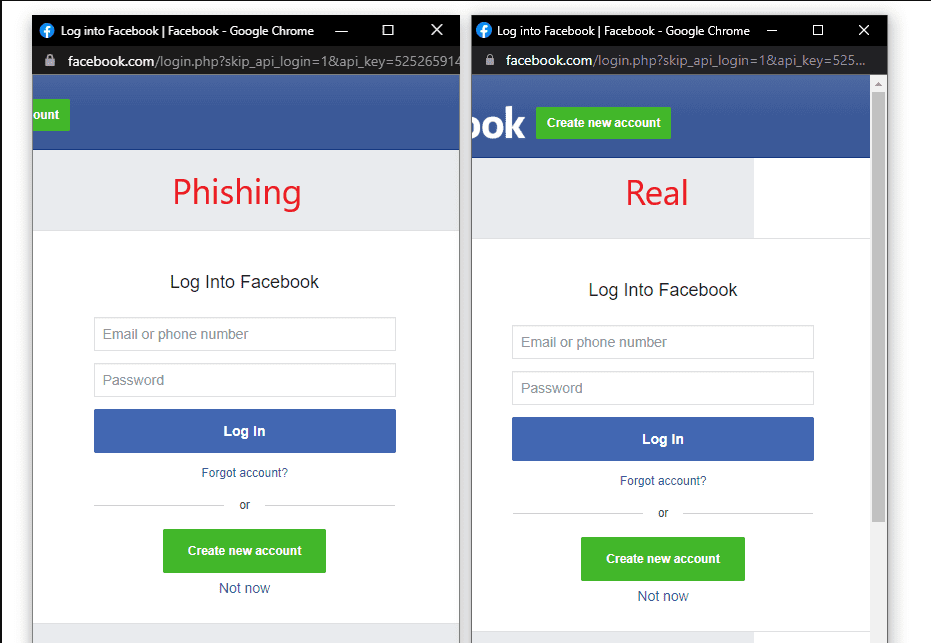
So you might be wondering why this login is important. Most online services nowadays allow you to use your Apple, Gmail or Facebook to login and connect your accounts. Then when you select this option a new browser window is opened with a login page displayed. We call this OAuth and hundreds of sites are using this protocol to help users avoid having to create a new account.
With BITB we spoof this OAuth page to capture credentials from users. This all happens with simple HTML/CSS code and, if implemented correctly, JavaScript can be used to spoof a whole website- Mr.d0x used a fake Canva page as his template in his proof-of-concept with one of his templates he created, which can be found on GitHub.
How is it used?
So here’s the thing, just like with any phishing campaign this attack requires your victim to actually land on the page and click the link. There are various ways to achieve this goal one being creating a spoofed site that uses the OAuth protocol. After we create the site we need to do some recon on the target machine. We need to know OS and browser preferences to know which pop-up template we need to use. Next, once deployed all we need to do is wait for the victim to land on our page and they will have the ultimate piece of mind knowing they are logging in securely to what appears to be a legitimate site.
Let me break it down for you. This technique uses a series of HTML and cascading style sheets to create a pop-up with the login, only its not a new browser. With HTML we create a window inside the original browser and style it with CSS from the original browser. This gives us the window with the logos, inputs and even a URL window with a valid URL displayed to instill more confidence in our target.

Where can I download BitB examples?
They have created the following Chrome templates for Windows and Mac:
Windows – Chrome (Light & Dark Mode)
Mac OSX – Chrome (Light & Dark Mode)
Check out: https://github.com/mrd0x/BITB
Conclusion
Finally the Browser in the Browser phishing technique is so simple to implement and very effective. This attack can be used on n00bs or experienced web users all the same. Just remember, if you cant move the popup out of the browser window, you know its a BitB attack. Mr.d0x did it again and his templates get 3 out of 5 bunnies.



Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive discount here
Help support LHN by buying a T-shirt or a mug?
Check out our selection here
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.

