Many years ago, Madonna sang about sharing her secrets with us. While the IT version may not be as entertaining as what was discussed in that song, there are still important reasons to understand your corporate encryption secrets and how they are provisioned, managed and deployed. The tools to do this go by various monikers, including SSL/TLS certificate or key management tools, machine identity management, or PKI as a service.
These secrets are found all over the IT map, including those for servers, for applications, to encrypt your email messages, for authenticating to connect with IoT devices, to allow you to make edits to a piece of code, and for user identities to have access to a particular shared resource. For example, these certs are commonly used to encrypt web and database traffic across the internet to protect these applications from man-in-the-middle attacks and other compromises.
That adds up to a lot of certs to keep track of and the consequences are the typical business has to deal with hundreds, if not tens of thousands, of individual certs. Another example: The typical web server has a choice of three different types of SSL certs. What is worse is that these certs are designed to expire periodically—after a year typically—so renewals need to be done in a timely fashion by using automation tools.
Managing certificates
An earlier CSO article provided best practices for managing these certs. It has links to free testing tools for your SSL infrastructure and other suggestions on how to deploy and manage your certs, including specifics for managing Windows application and user certs. If you are new to the world of certs, you might want to start with some of these more exemplary tutorials that will give you a better overview of the issues and how the components all fit together:
This management capability isn’t the same as running a certificate authority (CA) to create the actual certs themselves, although some of the CAs, such as Digicert, Sectigo, GlobalSign and Entrust, offer management as one of their additional services. Management is needed because the CA options are numerous: running your own internal root CA, hosting a private CA on some managed service, using a public CA, or mixing private CAs on a public cloud.
Most enterprises have certs from a variety of sources and keeping track of them—when they expire, what they cover, whether they have been provisioned properly—isn’t an easy job. Ideally, you will want to use some kind of automation to ensure that the keys and secrets are properly protected, and you can scale up your protection as you deploy more servers and applications that depend on these secrets. This is why so many hackers are successful at breaching networks and finding weak or unprotected servers to compromise. You’ll want a tool to automate the provisioning and revocation of certificates, track lifecycle management, provide irrefutable logs for security audits and integrate with other back-end security applications.
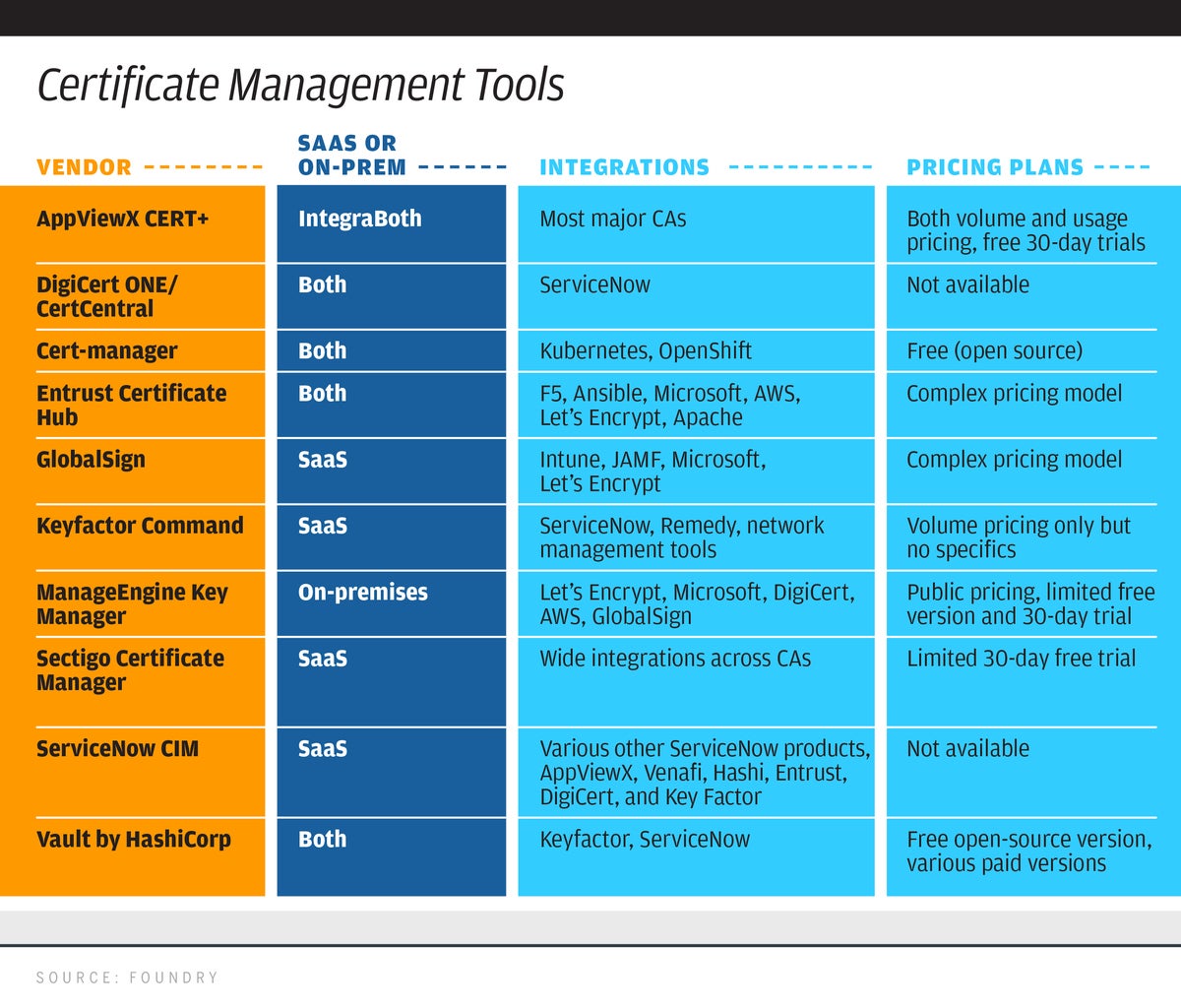
There are more than a dozen vendors, as you can see from the table below. (Note: Venafi did not respond to our request for information, so it is not included here.)
 Foundry
FoundryQuestions to ask certificate management vendors
Ask these questions when shopping for a certificate management vendor:
- What is the packaging? Some tools come as SaaS services (that run on a variety of public and private clouds), some are downable software, and some offer both.
- What kinds of key management policies can be created? The more you can use automation, the more security you’ll have in managing your cert collection.
- Is this a standalone tool or part of a suite? For example, Venafi and Keyfactor have other on-premises tools or additional features to enforce and protect SSH keys across your enterprise.
- Have they been audited? Some of the vendors have done SOC 2 Type II and ISO 27001 audits and a few even allow you to examine them before becoming a customer (such as GlobalSign).
- Are there limits on the CAs they can manage? For example, Google’s Cert Manager can only handle Google or Let’s Encrypt CAs. Some of the other tools have a wider target and can manage a variety of third-parties’ CAs, such as the open-source cert-manager, which can manage certs from Let’s Encrypt, Hashi, Venafi and private CAs.
- Can the tool discover all your certs across your infrastructure? To be truly useful, you want to be able to seek out and find them all to ensure that you can manage your entire inventory, including being able to handle Microsoft’s Active Directory (AD) and user account certs. Some tools have downloadable agents that can search segmented networks or across firewalls.
- Can you get by with just the platform-as-a-service (PaaS) freebie cert managers? Probably not: The major PaaS vendors have their own cert management services that are typically free (AWS has some fees)—AWS Certificate Manager, Azure Key Vault, Google Cloud Platform Cert Manager, and Windows AD Certificate Services. They are limited in terms of CA support and specific to their platforms.
- Can the tool deploy certs on all kinds of domain configurations, including subdomains and support wildcard domains?
- Finally, what is the typical pricing? Some of the products are free, some have rather complex pricing schemes, or they charge per cert, which can get expensive. Hashi and ManageEngine are both notable in having public pricing schemes. None of the others offered specific pricing details, suggesting that each client has separate negotiated pricing quotes.
10 certificate management tools: A closer look
AppViewX CERT+
AppViewX CERT+ has three different packaging options: a true multi-tenant SaaS, a virtual machine (VM) that can be hosted on your premises, or as an instance in your AWS infrastructure. The code base is the same for each one. It has numerous default policies for many circumstances, including some for shortened cert valid time frames. It also has some of the SOC audits completed. AppViewX provides a cloud discovery agent that can be used to discover certs without having to make firewall rule changes.
The company offers two different pricing models, an unlimited model and one that is usage based. It integrates with most of the major CAs and support subdomains and wildcards and have SOC audits privately available for their customers.
DigiCert ONE
DigiCert has been in the CA business since taking it over from Verisign back when the internet was young. Today, its DigiCert ONE product offers full automation of private certs in a variety of packages, including on premises, private clouds and managed services. The company offers a full lifecycle management tool that covers both subdomains and wildcards, and also support Microsoft AD and user certs. It has an interesting feature where you can lock your domain to allow only DigiCert CA-issued certs as one way for IT to get ahold of this process. The company doesn’t discuss pricing.
Entrust Certificate Hub
Entrust offers actual certs—it was one of the first commercial CAs—and has been doing business for decades. Entrust Certificate Hub offers single tenant either as downloadable software (either as a VM or as part of Kubernetes) or as a managed service. Its certs are managed by a cloud-based management service.
Certificate Hub’s feature set is somewhat long in the tooth and the company is working to update to a more competitive offering and building a more robust policy engine. They support Microsoft, Let’s Encrypt, and AWS CAs and have an API to integrate with others such as Apache, F5, and NGINX services. Entrust has a fairly complex pricing scheme that offers three different feature sets (for discovering certs, for controlling them, and for a complete automation package) both in unlimited and in subscription, per-managed private CA pricing plans.
GlobalSign
GlobalSign offers a series of tools, including a cloud-based certificate manager that also integrates with Microsoft’s AD and user account certs, and a managed PKI platform. It comes with automation and a wide collection of policies and protocol support. Being its own CA, GlobalSign’s manager is primarily designed to handle its own certs, which is why they offer a wide collection of integrations to Microsoft Intune, Jamf, and Let’s Encrypt. The company recently added a more capable S/MIME cert feature. It supports subdomain and wildcard certs and has several different pricing models, including volume licenses and pay as you go. GlobalSign’s SSL certs are priced per active domain subscriptions. Unlike most of the vendors, the company offers public links on its website to audit reports.
Keyfactor Command
Keyfactor Command is a complete secrets management SaaS platform that is both broad and deep and offers a wide variety of services, including lifecycle cert automation, SSH and other encryption key management and code signing, in addition to another service that is focused on IoT cert management. Keyfactor has issued nearly a billion certs across the globe and a variety of pricing plans that include an “all you can eat, unlimited” plan, because Keyfactor doesn’t offer a per-cert pricing schedule. One of its customers has more than 500 million certs that they manage with this service. It works with DigiCert, Entrust, Sectigo, Microsoft (end user and AD), Vault, and self-signed CAs.
ManageEngine Key Manager Plus
Key Manager Plus is an on-premises-only product that has a wide variety of integrations to CAs such as DigiCert, Let’s Encrypt, Microsoft AD, AWS, and GlobalSign. It has a transparent pricing page and offers a forever free version (with limited functionality) and a 30-day free trial. It comes with a wide collection of management policies and can discover certs from a variety of sources and CAs, along with agents that can be used on segmented or firewalled networks.
Open-source solutions
Open-source tools for certificate management are mainly used for containerized applications, such as cert-manager. This is a joint effort run by the Cloud Native Computing Foundation and has contributions from Google, HashiCorp, Venafi, and other vendors. It is designed to work with both Kubernetes and OpenShift environments and can handle both public and private certs. Another tool is Certbot that is used to automatically use Let’s Encrypt certs to enable HTTPS.
Sectigo Certificate Manager
Sectigo has been in the CA business for many years. Certificate Manager, its cloud-based lifecycle management product, offers a wide collection of integrations such as AWS, Google, and Azure keys. Its policies and can discover and manage public and private certs. It is widely used by large enterprises to track and control their cert population with its built-in automation tools. Certificate Manager also has passwordless and document signing use cases. A limited function free 30-day trial is available, and pricing is available either by subscription or unlimited plans.
ServiceNow Certificate Inventory and Management
ServiceNow has its Certificate Inventory and Management service, but if you don’t have any other ServiceNow products, this tool isn’t a good first foray. You’ll need additional tools, such as its CMDB and ITOM Discovery modules, which can find all self-signed and CA signed and deployed TLS certificates. ServiceNew offers integrations with Microsoft, AWS, GoDaddy, AppViewX, Venafi, Vault, Entrust, DigiCert, and Keyfactor, but not any Java key stores.
Vault by HashiCorp
Vault is available in a variety of packaging, including on-premises and various cloud and managed platforms. There are two basic versions: a forever free open-source download and various enterprise paid versions. It comes from a deep command-line heritage, but there is a user interface for beginners or those who are command-line averse. It has dozens of integrations with Keyfactor (which you would want to use for discovery and dashboards), AWS Lambda, and ServiceNow, as well if you use any of Hashi’s popular DevOps tools. Public and private certs, subdomains, and wildcards are supported, and audits are privately available to customers.
Copyright © 2022 IDG Communications, Inc.

