Cybersecurity researchers have taken the wraps off what they call a “nearly-impossible-to-detect” Linux malware that could be weaponized to backdoor infected systems.
Dubbed Symbiote by threat intelligence firms BlackBerry and Intezer, the stealthy malware is so named for its ability to conceal itself within running processes and network traffic and drain a victim’s resources like a parasite.
The operators behind Symbiote are believed to have commenced development on the malware in November 2021, with the threat actor predominantly using it to target the financial sector in Latin America, including banks like Banco do Brasil and Caixa.
“Symbiote’s main objective is to capture credentials and to facilitate backdoor access to a victim’s machine,” researchers Joakim Kennedy and Ismael Valenzuela said in a report shared with The Hacker News. “What makes Symbiote different from other Linux malware is that it infects running processes rather than using a standalone executable file to inflict damage.”
It achieves this by leveraging a native Linux feature called LD_PRELOAD — a method previously employed by malware such as Pro-Ocean and Facefish — so as to be loaded by the dynamic linker into all running processes and infect the host.
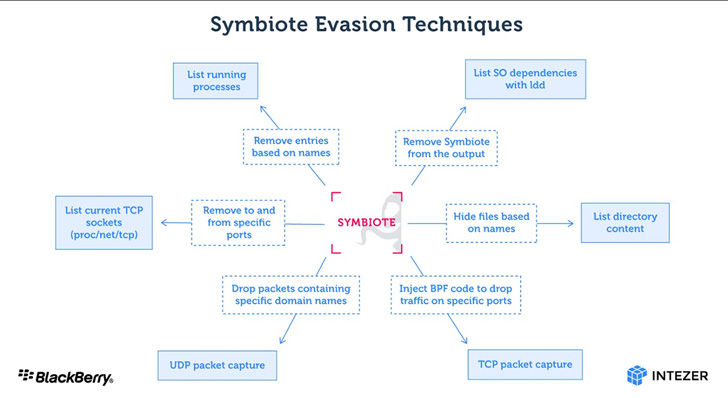
Besides hiding its presence on the file system, Symbiote is also capable of cloaking its network traffic by making use of the extended Berkeley Packet Filter (eBPF) feature. This is carried out by injecting itself into an inspection software’s process and using BPF to filter out results that would uncover its activity.
Upon hijacking all running processes, Symbiote enables rootkit functionality to further hide evidence of its presence and provides a backdoor for the threat actor to log in to the machine and execute privileged commands. It has also been observed storing captured credentials encrypted in files masquerading as C header files.
This is not the first time a malware with similar capabilities has been spotted in the wild. In February 2014, ESET revealed a Linux backdoor called Ebury that’s built to steal OpenSSH credentials and maintain access to a compromised server.
“Since the malware operates as a user-land level rootkit, detecting an infection may be difficult,” the researchers concluded. “Network telemetry can be used to detect anomalous DNS requests and security tools such as AVs and EDRs should be statically linked to ensure they are not ‘infected’ by userland rootkits.”